Reinforcement and protection method and system for software installation package
A software installation package and system protection technology, applied in the security field, can solve problems such as low difficulty of decompilation and inability to completely solve security problems of Android installation packages, and achieve the effects of improving security levels, protecting interests, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
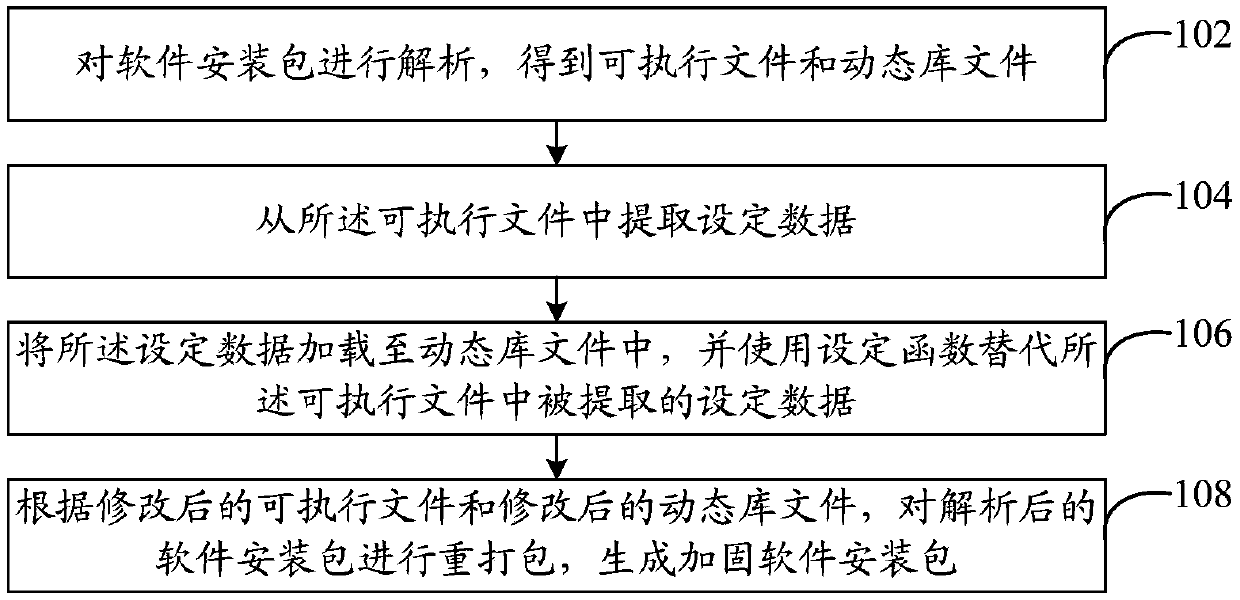
[0024] refer to figure 1 , shows a flow chart of steps of a method for hardening and protecting a software installation package in Embodiment 1 of the present invention. In this embodiment, the reinforcement protection method of the software installation package includes:
[0025] Step 102, analyzing the software installation package to obtain executable files and dynamic library files.
[0026] Taking the software installation package of the Android system as an example, the executable file can be but not limited to refer to the dex file (type of executable file on the Android platform), and the dynamic library file can be but not limited to refer to the so file (so file Refers to the library file under linux, the suffix is .so, hence the name. The so file is a dynamic link library file in ELF format, and the so file is dynamically loaded into the program when the program is running to support the running of the program).
[0027] Step 104, extract setting data from the e...
Embodiment 2
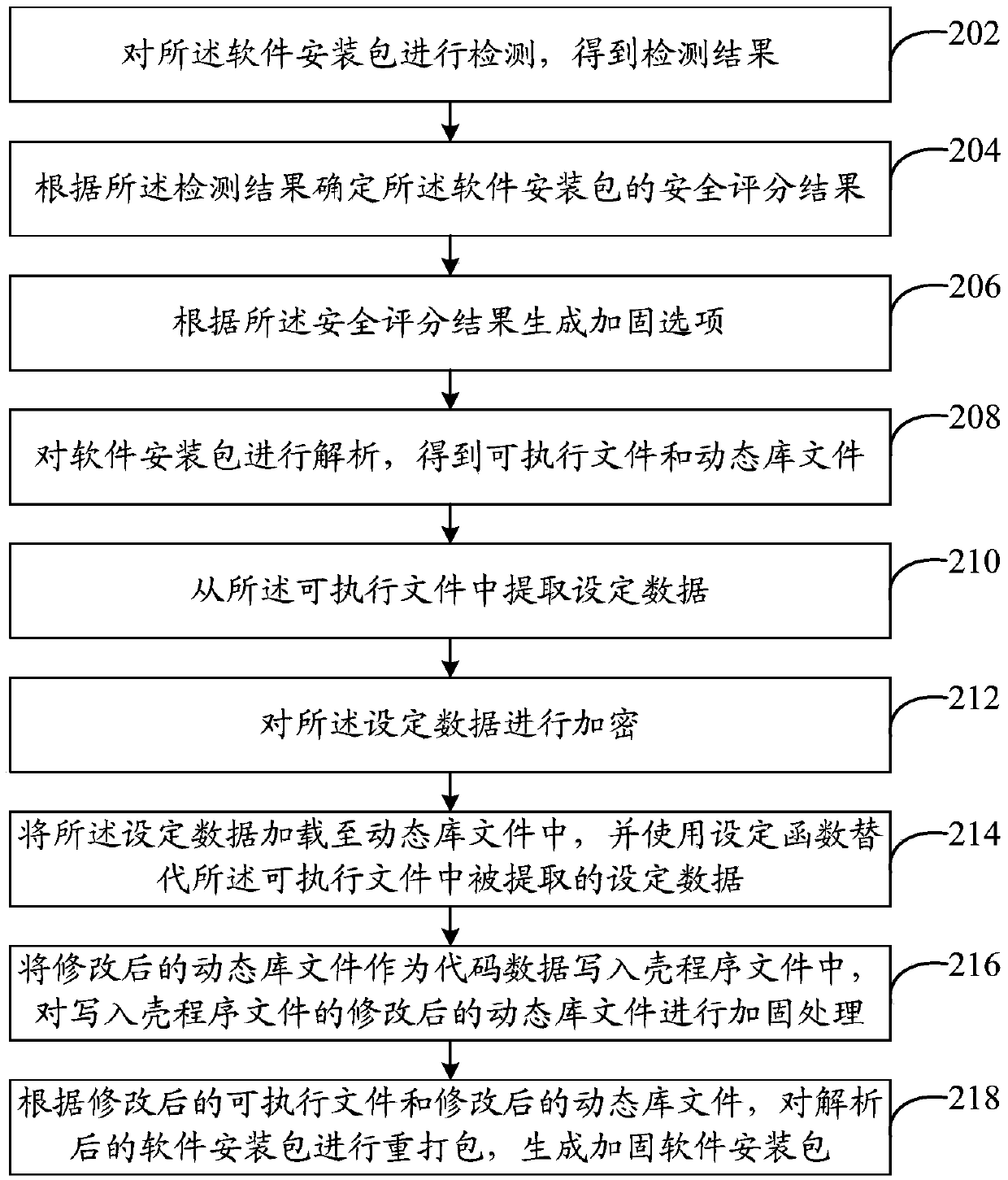
[0035] refer to figure 2 , shows a flow chart of steps of a method for hardening and protecting a software installation package in Embodiment 2 of the present invention. In this embodiment, the reinforcement protection method of the software installation package includes:
[0036] Step 202, detecting the software installation package, and obtaining a detection result.
[0037] In this embodiment, the security of the software installation package may be checked through the application on the third page, but not limited to. For example, at least one of the following detection results may be detected: a detection result of a dex file, a code obfuscation detection result, a secondary packaging detection result, and a source code detection result.
[0038] Step 204, determine the security scoring result of the software installation package according to the detection result.
[0039] In this embodiment, a comprehensive analysis may be performed on the above-mentioned multiple de...
Embodiment 3
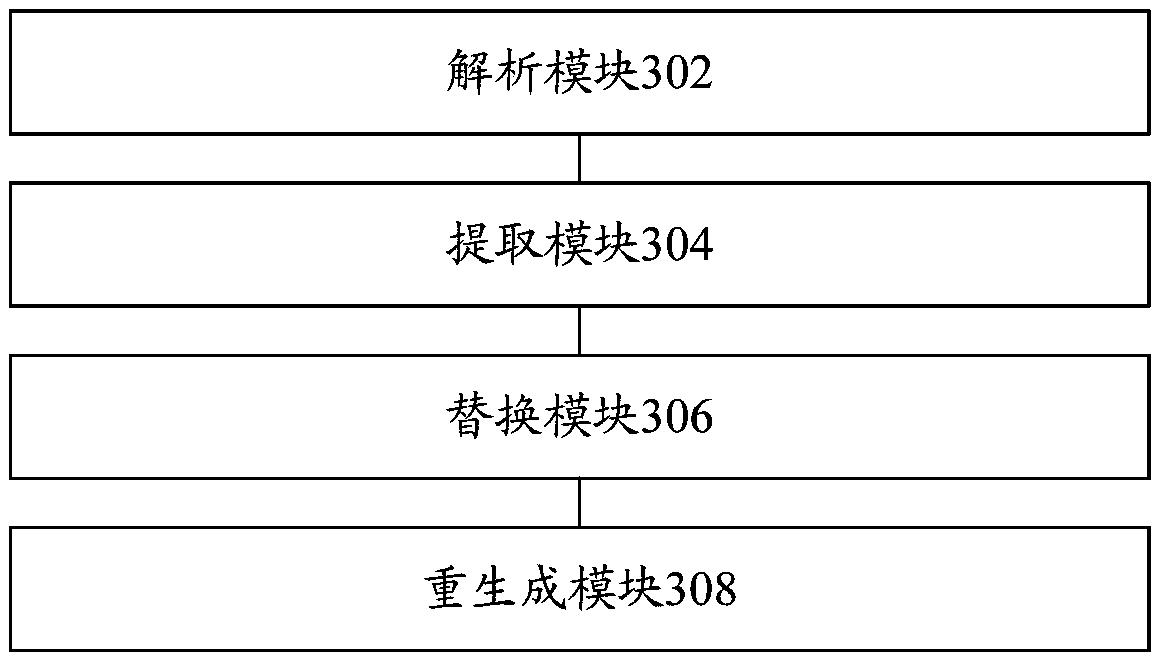
[0064] Based on the same inventive concept as the above-mentioned method embodiment, refer to image 3 , shows a structural block diagram of a hardening protection system for a software installation package in Embodiment 3 of the present invention. In this embodiment, the reinforcement protection system of the software installation package includes:
[0065] The parsing module 302 is configured to parse the software installation package to obtain executable files and dynamic library files.
[0066] The extracting module 304 is configured to extract setting data from the executable file.
[0067] A replacement module 306, configured to load the setting data into the dynamic library file, and use a setting function to replace the extracted setting data in the executable file.
[0068] In this embodiment, the setting function may be used to indicate the loading position of the setting data in the dynamic library file.
[0069] The regenerating module 308 is configured to repac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com