A Marker-based Integrity Authentication Method for Vector Maps
A vector map, authentication method technology, applied in the fields of information hiding and geographic information science, can solve the problem of not being able to have precise positioning, tampering, primitive disorder and vertex reverse order attacks at the same time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0093] Below in conjunction with accompanying drawing and example technical solution of the present invention is described further:
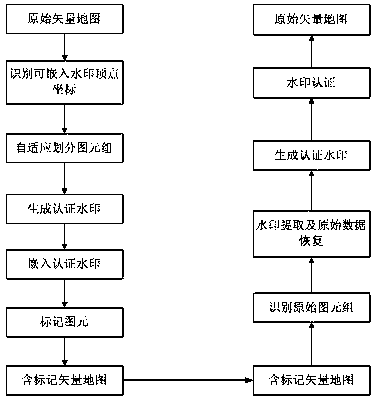
[0094] Such as figure 1 As shown, the flow chart of the mark-based vector map integrity authentication method of the present invention is generally divided into two aspects: A, vector map watermark embedding algorithm; B, vector map watermark authentication algorithm.
[0095] A. Vector map watermark embedding algorithm, the steps are as follows:
[0096] B. (1) Identify the vertex coordinates that can be embedded in the watermark;
[0097] C. According to the precision error tolerance of the vector map, identify the vertex coordinates that can be embedded in the watermark. The method for judging whether the x-coordinate and y-coordinate of the vertex of the graphic element are the vertex coordinates that can be embedded in the watermark is the same. The present invention uses the x-coordinate as an example to illustrate the method for judging...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com