Novel terminal safety soft secret key management method
A technology of terminal security and management method, applied in key distribution, can solve problems such as increased hardware cost, U-key loss, user troubles, etc., to ensure legality, prevent illegal tampering and information camouflage, and improve system security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
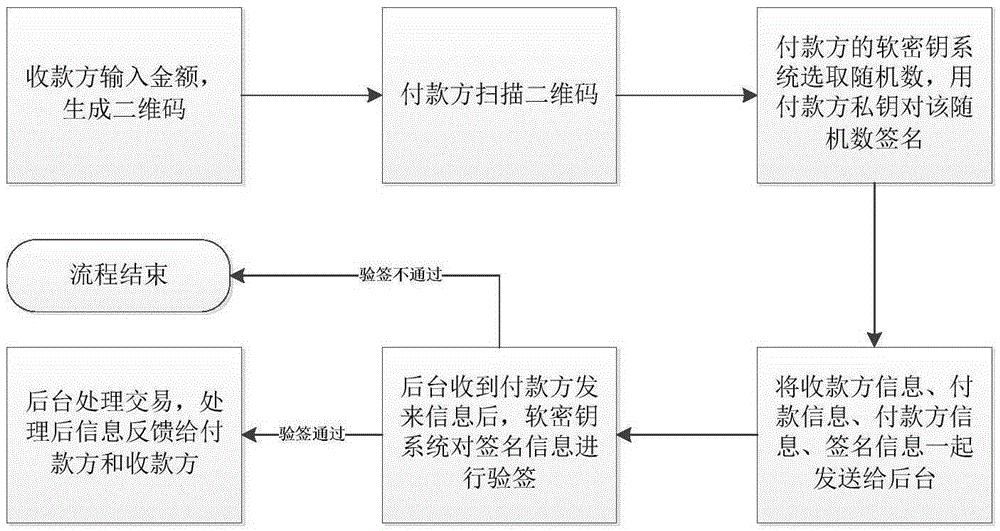
[0042] [Embodiment 1] Customer Zhang San pays customer Li Si online.
[0043] Such as figure 1 As shown, the payer Zhang San wants to pay the payee Li Si online, and both use the mobile phone e-wallet client to operate. The soft key system is installed on the Zhang San mobile phone, Li Si mobile phone, and the background management system. run. Li Si enters the amount on the mobile phone, and the e-wallet client generates a QR code with the payee information and payment information.
[0044] Zhang San scans the QR code, and the soft key system in Zhang San’s mobile phone selects a random number R, uses Zhang San’s private key to sign the random number R, and signs the recipient information, payment information, payer information, and signature The information is sent to the background management system together.
[0045] After the background management system receives the above information, the soft key system verifies the signature information: that is, the public key is mapped ou...
Embodiment 2
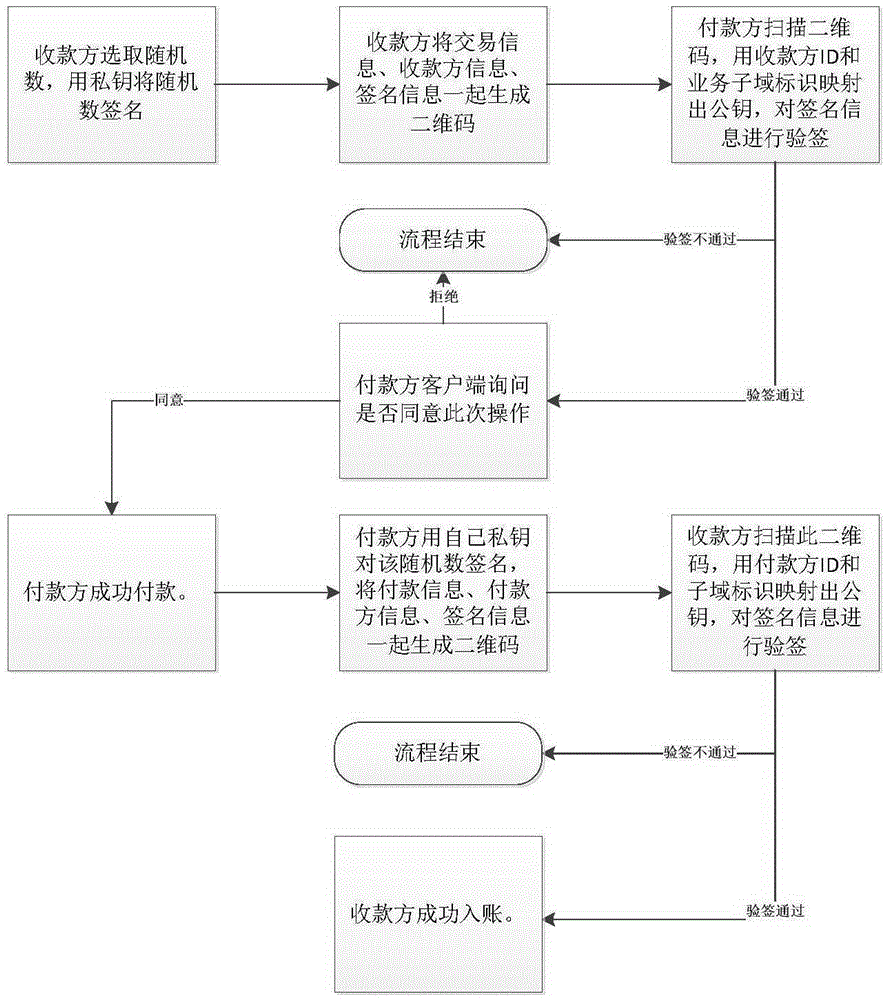
[0046] [Embodiment 2] Customer Zhang San pays customer Li Si offline.
[0047] Such as figure 2 As shown, the payer Zhang San wants to pay the payee Li Si offline, and both use the mobile phone electronic wallet client to operate, and the soft key system is installed and running on both Zhang San mobile phone and Li Si mobile phone. Li Si enters the amount on the mobile phone, the soft key system selects a random number R, uses the private key to sign the random number R, and generates a QR code with transaction information, Li Si ID information, and signature information.
[0048] Zhang San scans the QR code, the soft key system uses the Li Si ID and the business subdomain ID to map out the public key, and uses the public key to verify the signature information of Li Si. If the verification fails, the process ends.
[0049] If the verification is successful, Zhang San’s mobile client asks whether he agrees to the payment operation. If Zhang San refuses, the process ends. If Zhang...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com