Eyeball tracking technology based privacy protection method and system
A privacy protection system and eye tracking technology, applied in character and pattern recognition, instruments, digital data authentication, etc., can solve problems such as inconvenience and low user experience, and achieve the effect of convenient use, protection of personal privacy, and strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
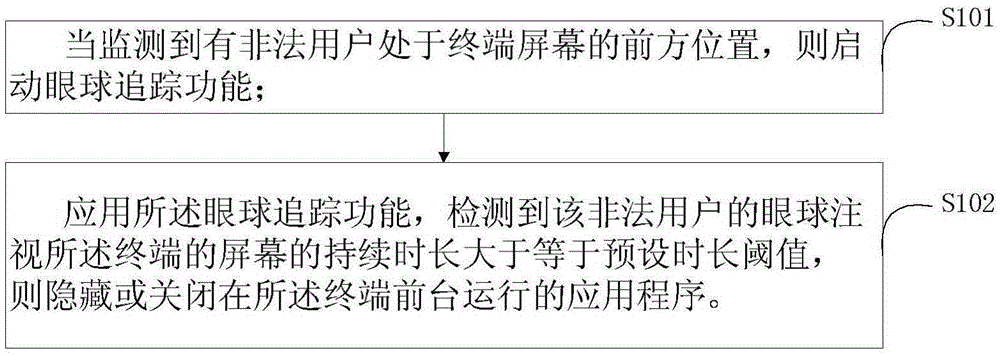
[0059] Please refer to figure 1, which is a method flowchart of the first embodiment of the privacy protection method based on eye tracking technology provided by the present invention. The privacy protection method based on eye tracking technology in the embodiment of the present invention can be applied to various smart devices, such as smart watches and smart phones.
[0060] The privacy protection method based on eye tracking technology includes:
[0061] Step S101, when it is detected that an illegal user is in front of the terminal screen, start the eye tracking function.
[0062] Preferably, the illegal user monitoring method includes a portrait recognition method (by judging whether the user portrait at the front of the terminal screen is legal for illegal user monitoring) and an infrared identification method (by judging whether the height of the user at the front of the terminal screen is legal for illegal user monitoring) ). Of course, those skilled in the art ca...
Embodiment 2
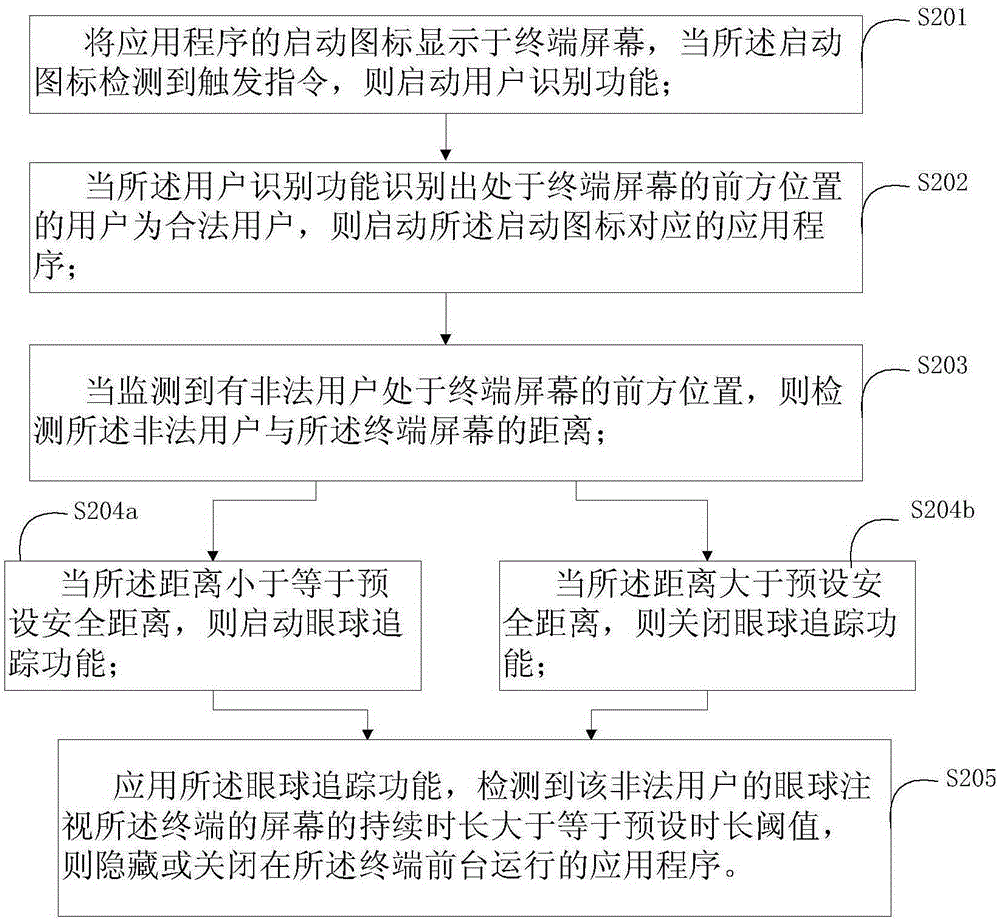
[0072] Please refer to figure 2 , which is a method flowchart of the second embodiment of the privacy protection method based on eye tracking technology provided by the present invention. In the embodiment of the present invention, on the basis of the first embodiment of the privacy protection method based on the eye tracking technology, the steps of starting the application program and the identification process of the illegal user / legal user are described in detail.
[0073] The privacy protection method based on eye tracking technology includes:
[0074] Step S201 , displaying the startup icon of the application program on the terminal screen, and starting the user identification function when the startup icon detects a trigger instruction.
[0075] Preferably, the trigger instruction detected by the startup icon corresponds to a screen click operation, and the screen click operation is more accurate than the touch screen operation, which can reduce the probability of mis...
Embodiment 3
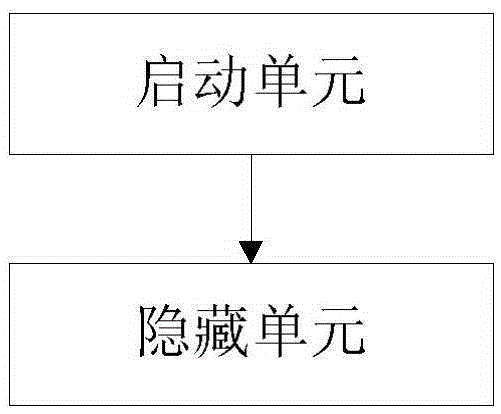
[0105] Please refer to image 3 , which is a structural block diagram of the first embodiment of the privacy protection system based on eye tracking technology provided by the present invention. The privacy protection system based on eye tracking technology can be applied to various smart devices, such as smart watches and smart phones.
[0106] The privacy protection system based on eye tracking technology includes:
[0107] The starting unit is used to start the eye tracking function when it is detected that an illegal user is located in front of the terminal screen;
[0108] The hiding unit is configured to apply the eye tracking function, detect that the duration of the illegal user's eyes watching the screen of the terminal is greater than or equal to a preset duration threshold, then hide or close the application program running in the foreground of the terminal.
[0109] The privacy protection system based on the eye tracking technology provided by the embodiment of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com