Method of improving blacklist matching efficiency of terminal equipment of AFC (Automatic Frequency Control) system
A system terminal and terminal equipment technology, applied in ticketing equipment, special data processing applications, instruments, etc., can solve problems such as low cost and reduced retrieval speed of AFC system terminal equipment blacklist
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0071] Embodiment 1: Selecting the separation linking method to solve the address conflict problem in the hash function H(key)
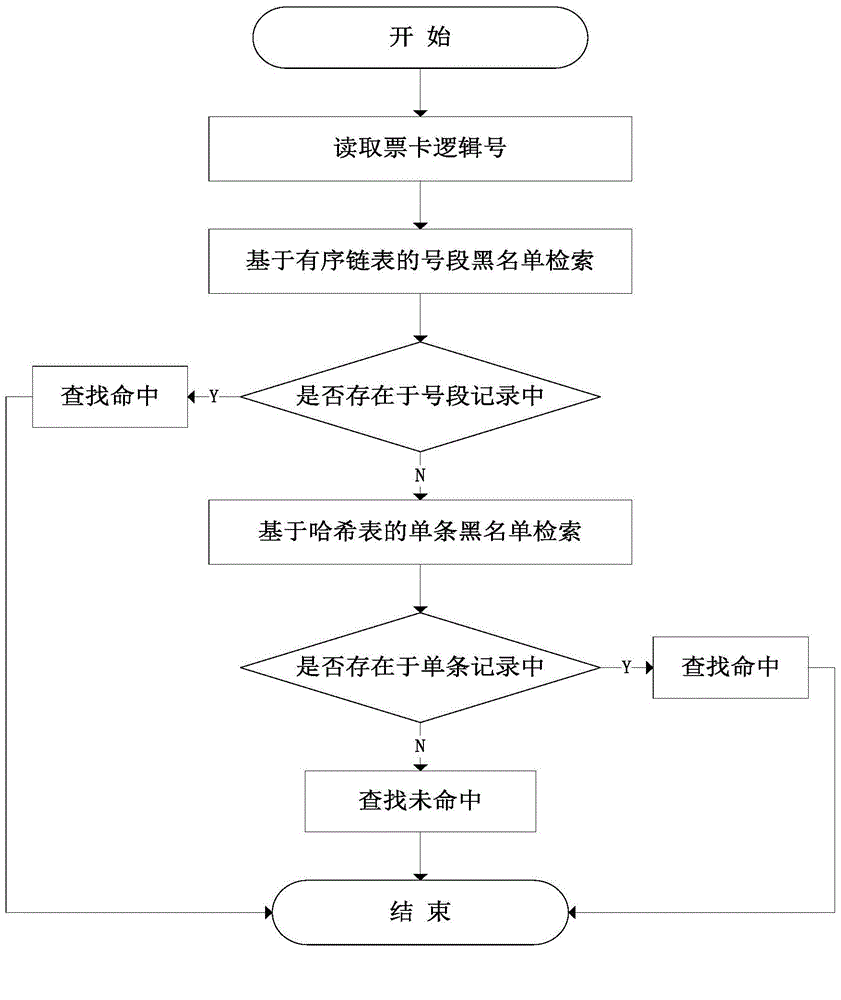
[0072] Such as figure 1 Shown is a schematic diagram of the steps of a method for improving the blacklist matching efficiency of terminal equipment in the AFC system. The present invention will be further described below in conjunction with examples.
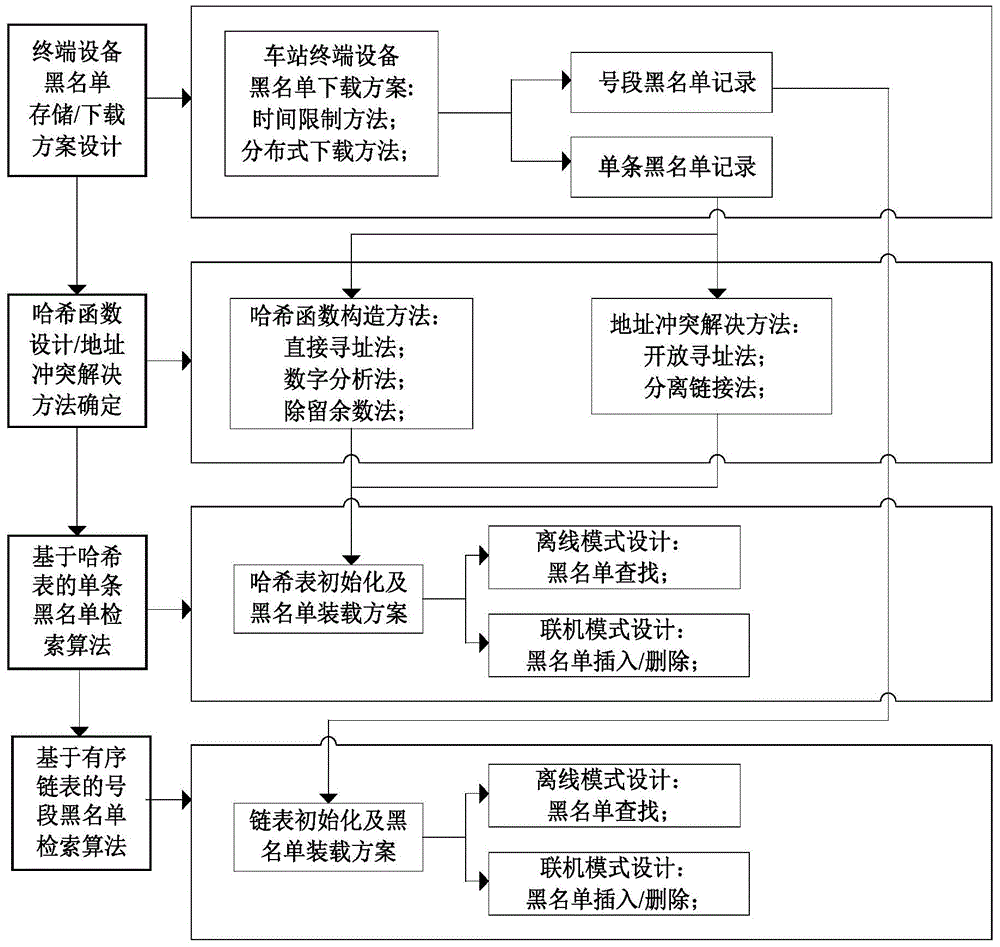
[0073] (1) Blacklist storage and download scheme design of station terminal equipment
[0074] This example takes the AFC system of Suzhou Metro as the implementation background. Its terminal embedded reader adopts 32-bit CPU and embedded operating system. The FLASH and memory should have sufficient capacity to run the operating system, application programs and save and ticket cards. related parameter files.
[0075] (1.1) When the distribution of logical numbers of blacklist tickets is relatively discrete, a single storage method is adopted; for some special cases, such as the loss of a w...
Embodiment 2
[0113] Embodiment 2: Select the open addressing method to solve the address conflict problem in the hash function H(key)
[0114] Although it is better to use the separate link method to solve the address conflict problem in Embodiment 1, the open addressing method can also be used. The difference between using the open addressing method and Embodiment 1 is:
[0115] In step (3.3.2), a single blacklist based on the hash table is inserted
[0116] ① Use the ticket logic number to be inserted into the blacklist record as the keyword key, and map it to the corresponding position H (key) in the hash table according to the hash function determined in (2.1); if you choose the open addressing method to solve the address conflict problem, then set the detector locate_times=0 and turn to ②;
[0117] ② If the position is not occupied, that is, logicalID=null, then store the effective field in the blacklist record to be inserted into this position, and return a Boolean value ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com