Method and device for accessing to physical resources
A technology of physical resources and physical addresses, applied in resource allocation, multiprogramming devices, program control devices, etc., can solve the problems of memory resource insecurity, memory resource leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
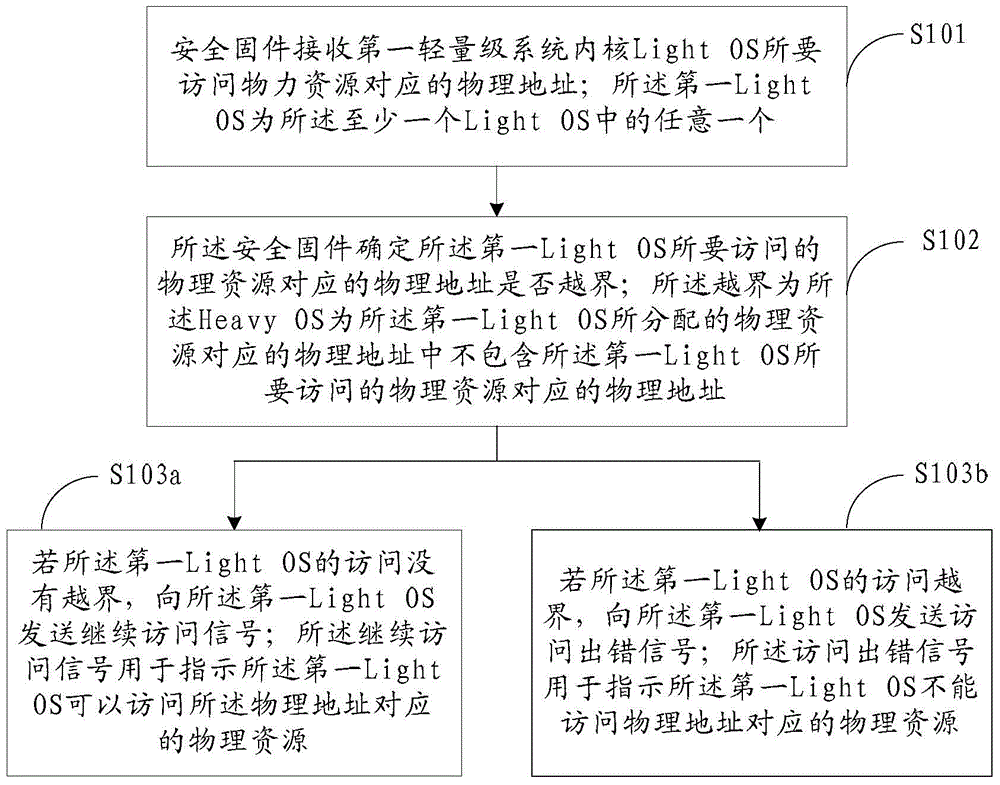
[0258] Next, a specific implementation solution for the method for accessing physical resources will be provided according to the above system. like Figure 4 As shown, it specifically includes the following steps:
[0259] Step 401, when the Heavy OS starts, initialize the security firmware.
[0260] Wherein, performing initialization settings on the security firmware; the initialization settings include: setting a capacity for storing second resource allocation mapping information in the security firmware; and binding the security firmware to the Heavy OS , so that the security firmware only stores or updates the second resource allocation mapping information under the control of the Heavy OS, and the security firmware only feeds back an abnormal access signal to the Heavy OS.
[0261]The second resource allocation mapping information may be a correspondence between the CPU included in the Light OS and the physical addresses of all or part of the physical resources allocat...
Embodiment 2
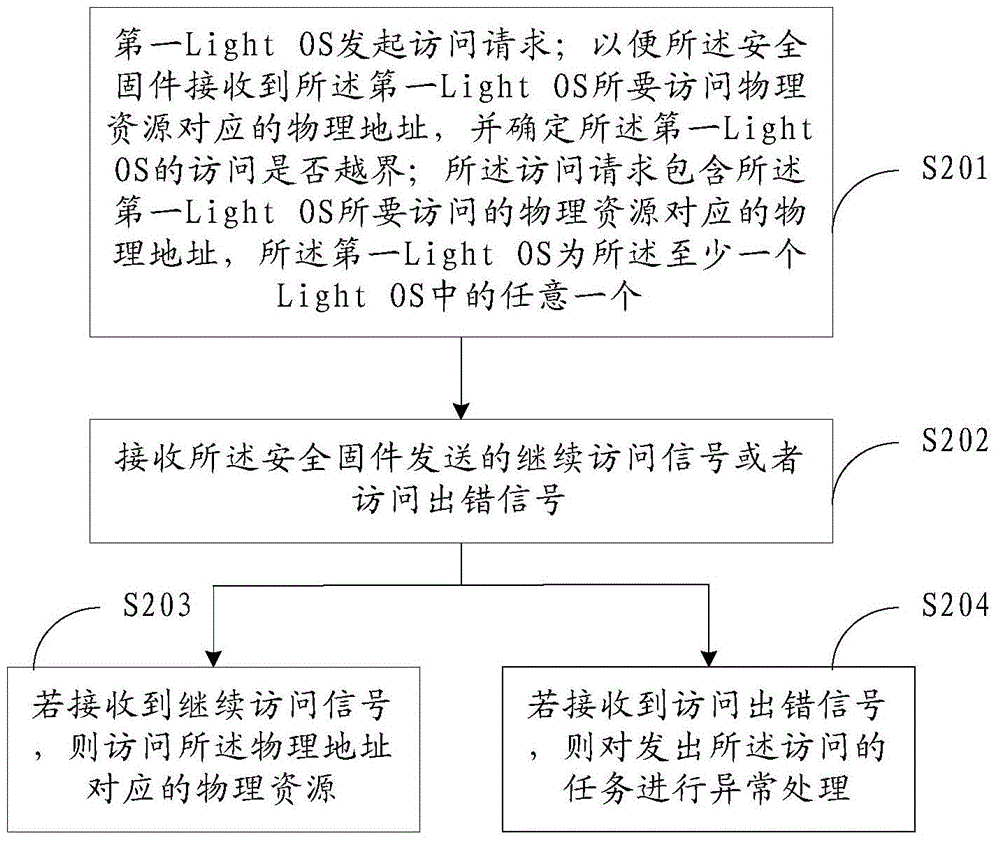
[0285] For the above-mentioned system, the embodiment of the present invention provides a method for accessing physical resources, the execution subject of which is the first Light OS, by monitoring the capability operation of the task process and the propagation path of key data in the first Light OS, to Guarantees access to kernel object resources. like Figure 5 As shown, the specific steps include:
[0286] Step 501, the first lightweight system kernel Light OS allocates kernel object resources for each task in the user space.
[0287] Wherein, the kernel object resource is that Light OS encapsulates kernel resources (such as memory, device, etc.) and exists in the form of an object (Object).
[0288] Specifically, the allocation of kernel object resources for each task in the user space by the first Light OS is completed by the Capability authorization module in the first Light OS, and the Capability authorization module is a part of the Capability mechanism. Among the...
Embodiment 3
[0301]For the above system, the embodiment of the present invention provides a method for accessing physical resources, the execution body of which is the Heavy OS, and the functional integrity of the Light OS is guaranteed by performing security detection on the Light OS. like Image 6 As shown, the specific steps include:
[0302] Step 601, the heavyweight system kernel Heavy OS sends a security inspection request to the first Light OS; correspondingly, the first Light OS receives the security inspection request sent by the Heavy OS.
[0303] Wherein, the security detection request is used to detect whether the first Light OS is abnormal; the Heavy OS may perform security detection on the first Light OS periodically or in real time, but it is certainly not limited thereto.
[0304] Further, before the Heavy OS performs security detection on the first Light OS, the method further includes: the Heavy OS periodically records the Capability table information of the first Light ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com