A method and system for identity authentication
A technology of identity information and identity identification, applied in the field of communication, can solve the problems of inability to resist server forgery attacks, inability to guarantee data transmission security, and complex computing operations, and achieve the requirements of low computing power of devices, ensure session security, and improve security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] In order to make the above objects, features and advantages of the present invention more comprehensible, the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
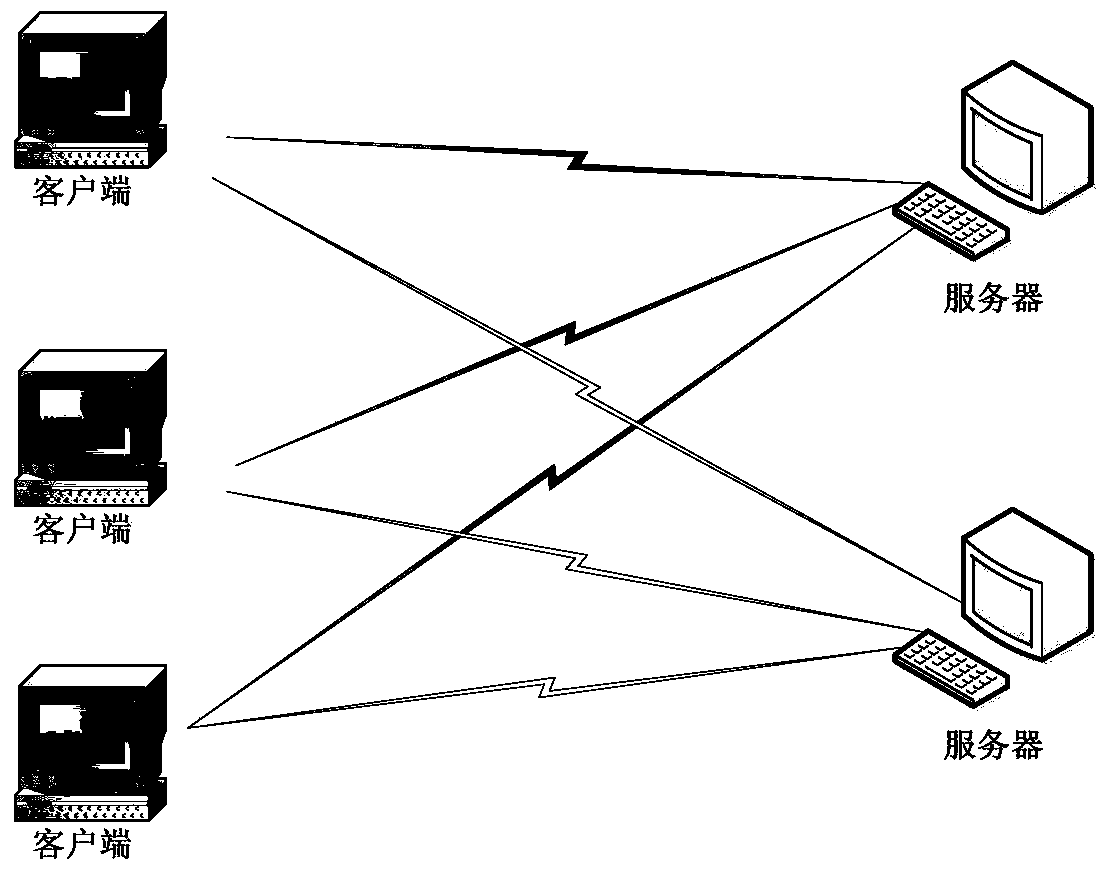
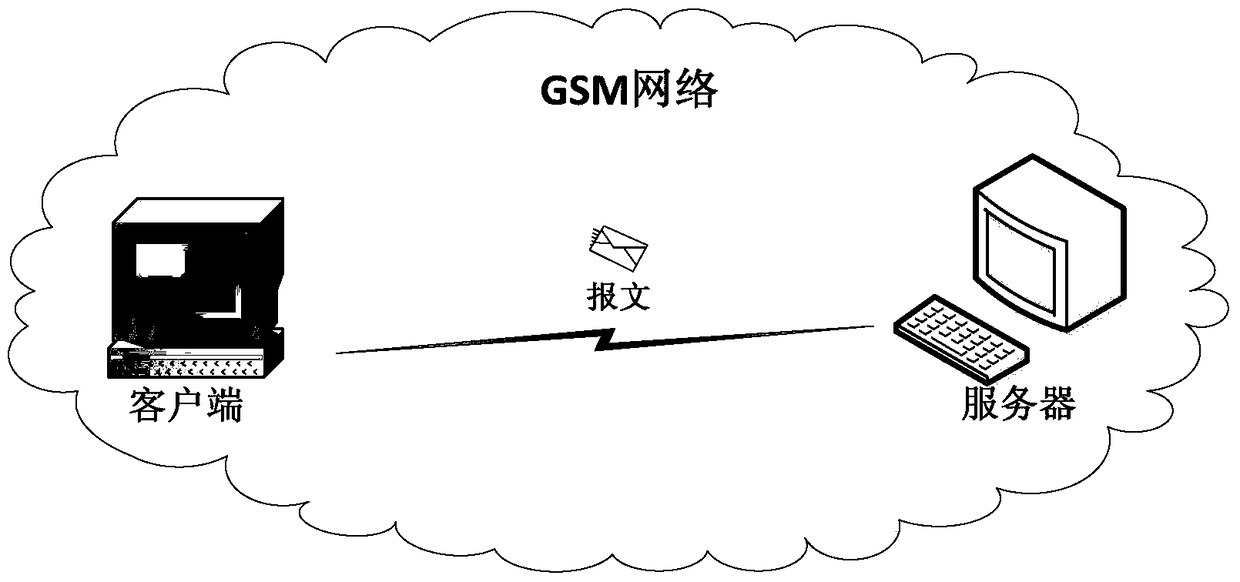
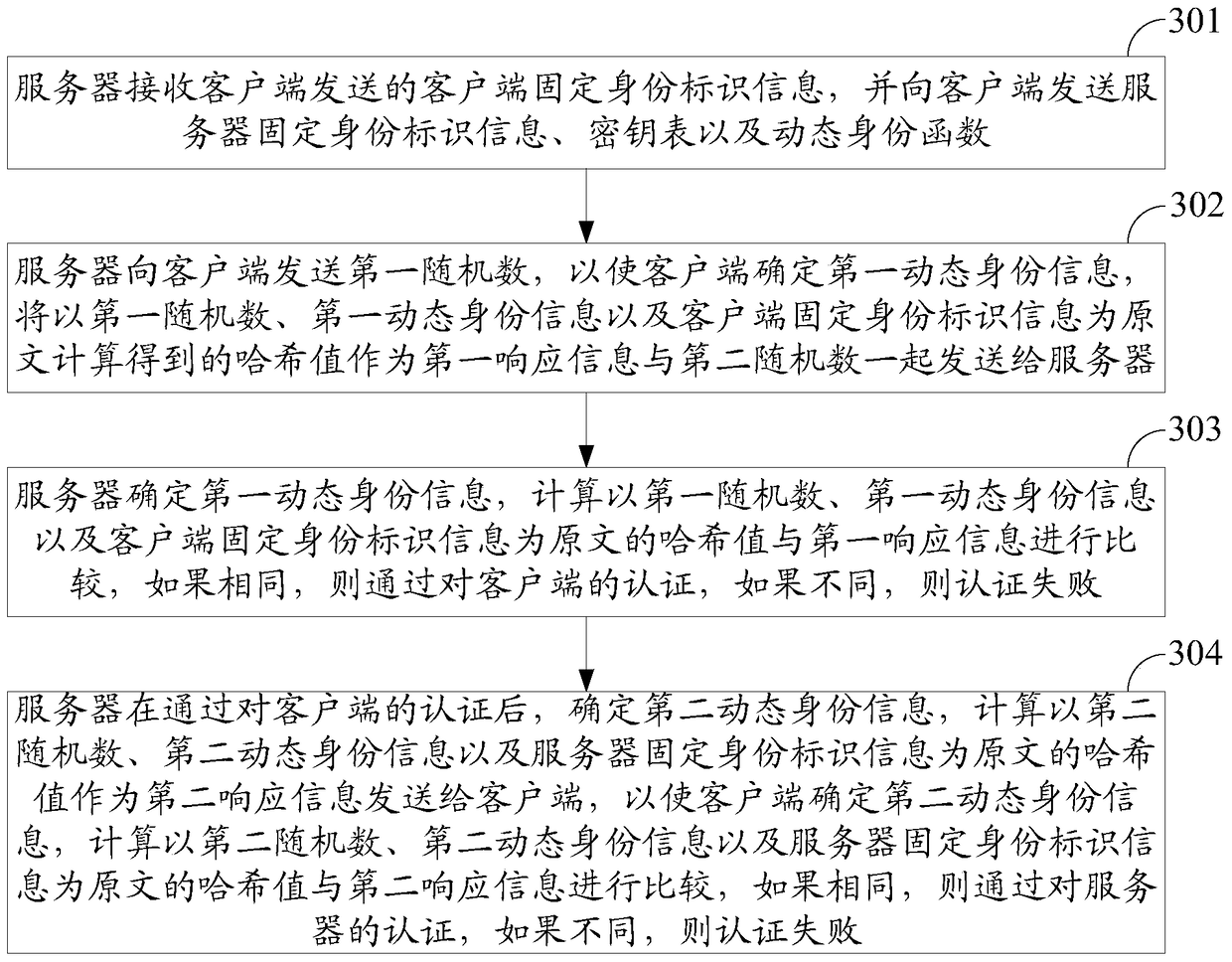
[0064] The identity authentication method and system provided in the embodiments of the present invention aim at the problems existing in the prior art, and propose a two-way identity authentication method based on multi-factor dynamic password and random key negotiation, with random numbers, dynamic identity information and The fixed identity information is combined with the hash value calculated from the original text as a dynamic password, and the identity of the communicating party is verified by verifying the dynamic password. At the same time or after the identity authentication, the server and the client work together to generate a random key sequence, and negotiate the session key according to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com