A method, device and terminal for securely starting a terminal
A technology for secure startup and terminal, applied in the electronic field, can solve the problems affecting terminal information security, malicious tampering of system files, etc., and achieve the effect of reducing the possibility of implanting malicious code, increasing user confidence, and increasing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
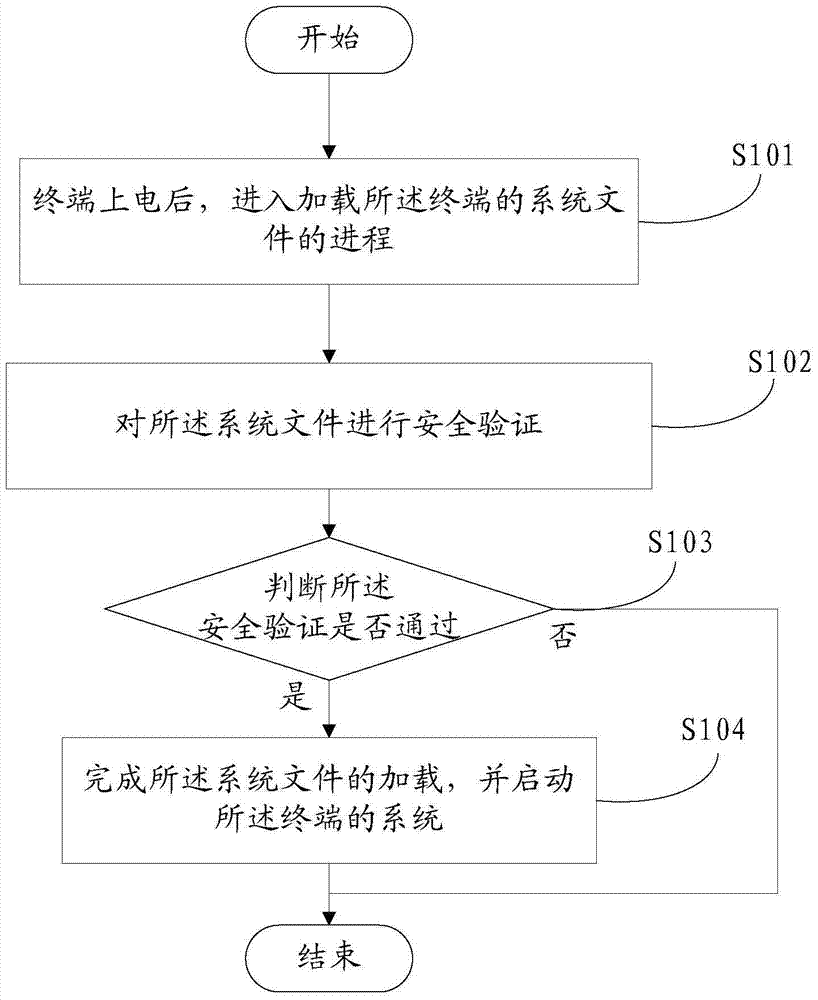
[0035] figure 1 It is a flowchart of a method for securely booting a terminal provided in Embodiment 1 of the present invention, which is composed of figure 1 As shown, in this embodiment, the terminal security startup method provided by the present invention includes:
[0036] S101: After the terminal is powered on, enter the process of loading the system file of the terminal;
[0037] The terminals involved in the present invention include: mobile phones, tablet computers, computers or palmtop computers, etc.; when the terminal is powered on, it starts the switch of the terminal; for this step, for example, during the startup process of the Android system, it enters the loading terminal When the system file is used, first load the Rom Soc (chip). There is a ROM (Read Only Memory) memory on the Soc chip. The code in the ROM is solidified in the form of a mask when the chip leaves the factory and cannot be modified; when the system starts, The code in the ROM is mainly respo...
Embodiment 2
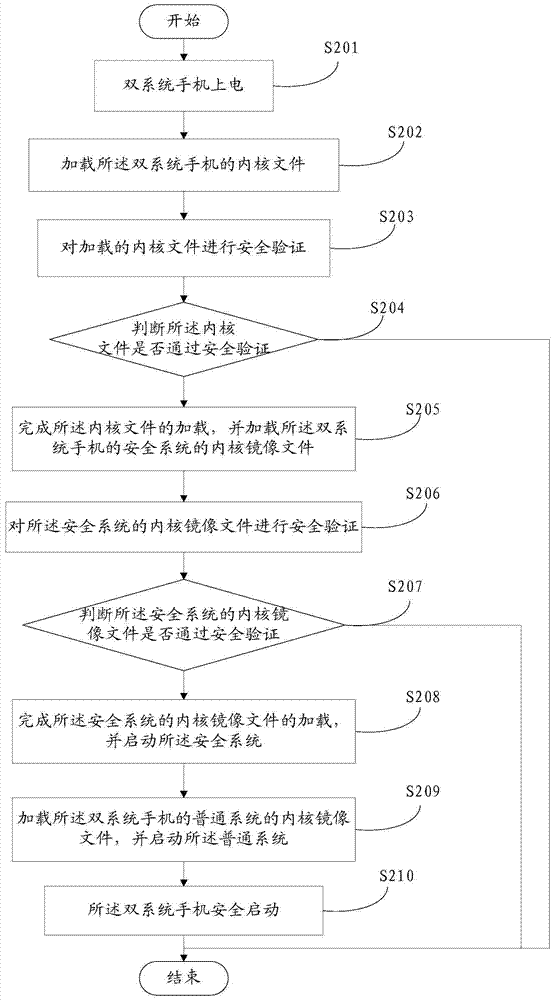
[0049] For example, the following describes the method in detail in practical applications, assuming that the terminal is a dual-system mobile phone, and the dual systems are security system and general information respectively; figure 2 It is a flow chart of a terminal secure boot method provided in Embodiment 2 of the present invention, which is composed of figure 2 As shown, in this embodiment, the secure boot method provided by the present invention includes:
[0050] S201: Power on the dual-system mobile phone;
[0051] S202: Load the kernel file of the dual-system mobile phone; for example, in the dual-system mobile phone, the kernel file is a linux kernel file;
[0052] S203: Perform security verification on the loaded kernel file; for example, by performing signature verification on the kernel file;
[0053] S204: Judging whether the kernel file has passed the security verification; if so, turn to S205, if not, then end; for example, when performing signature verif...
Embodiment 3
[0062] image 3 A schematic structural diagram of a terminal security boot device provided in Embodiment 3 of the present invention, which is represented by image 3 As shown, in this embodiment, the terminal security boot device 30 provided by the present invention includes: a file loading module 301, a security verification module 302, a judging module 303, and a system startup module 304; the file loading module 301 is used on the terminal After powering on, enter the process of loading the system file of the terminal; the security verification module 302 is used to perform security verification on the system file loaded by the file loading module 301; the judging module 303 is used to judge the security verification module 302 whether the security verification is passed; the system startup module 304 is configured to complete the loading of the system file and start the system of the terminal if the judging result of the judging module 303 is yes.
[0063] The secure acti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com