Security access method of xmpp protocol based on sensor network
A sensor network and protocol security technology, applied in security devices, transmission systems, electrical components, etc., can solve problems such as limited use of TLS, difficulty in implementing encryption algorithms, and high communication overhead, and achieve authentication efficiency and energy consumption optimization , Realize the confidentiality and integrity of information, and protect the effect of link security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] Hereinafter, the preferred embodiment of the present invention will be described in detail with reference to the accompanying drawings; it should be understood that the various data and methods of this embodiment, the preferred embodiment is only a special example of the implementation method of the present invention, not for limitation The scope of protection of the present invention.
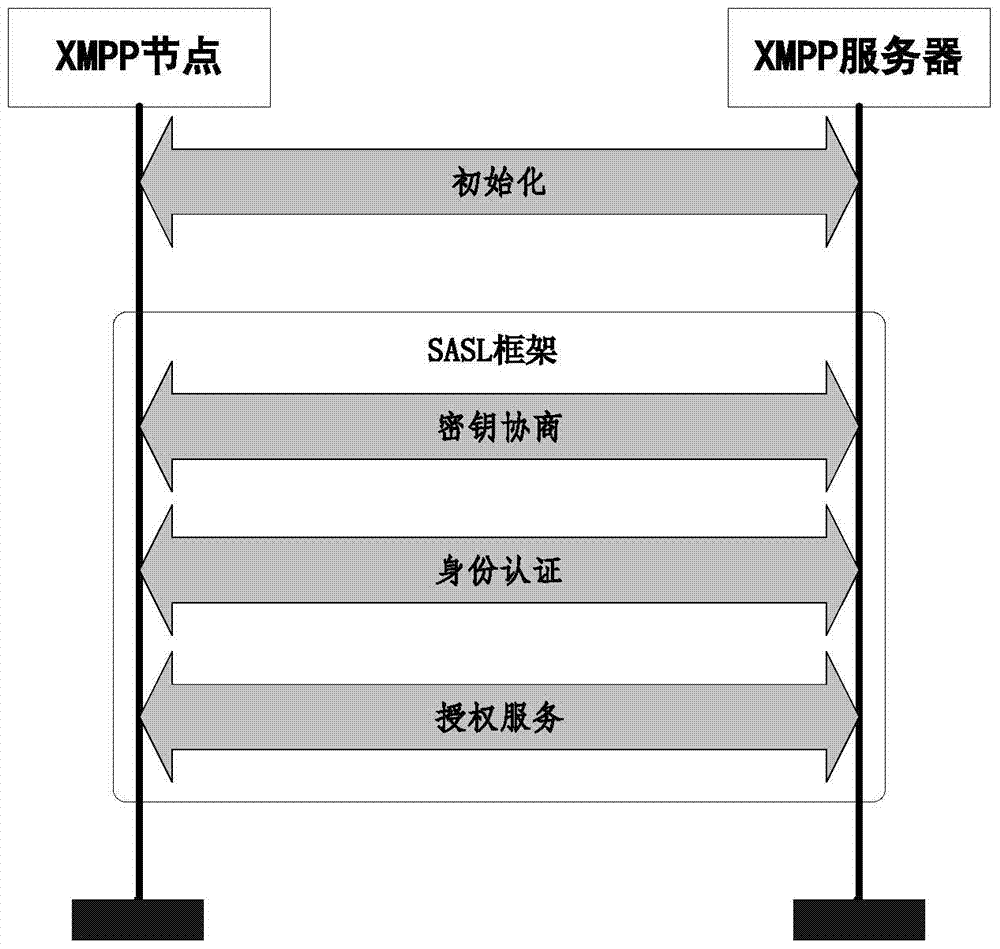
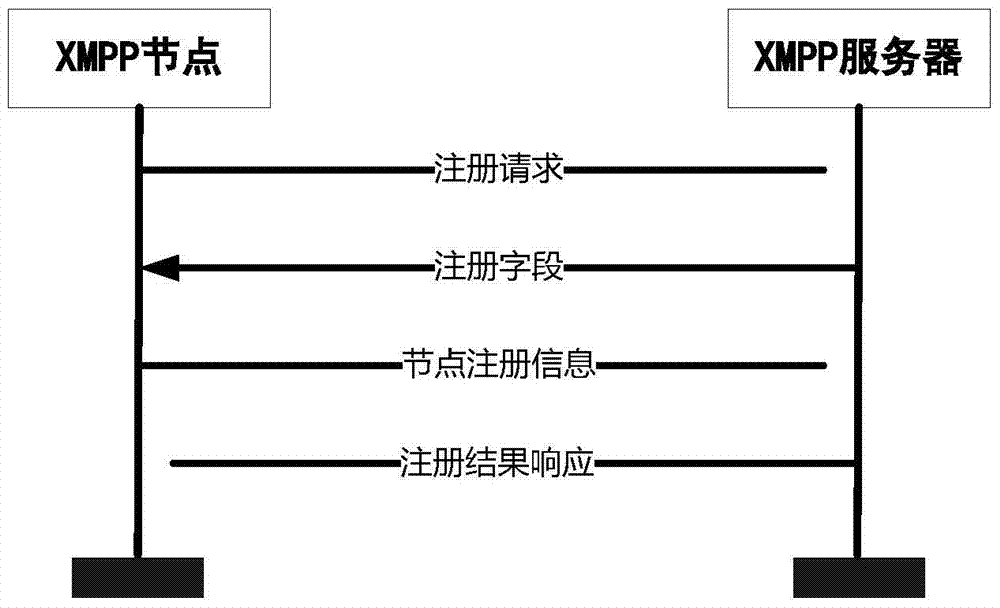
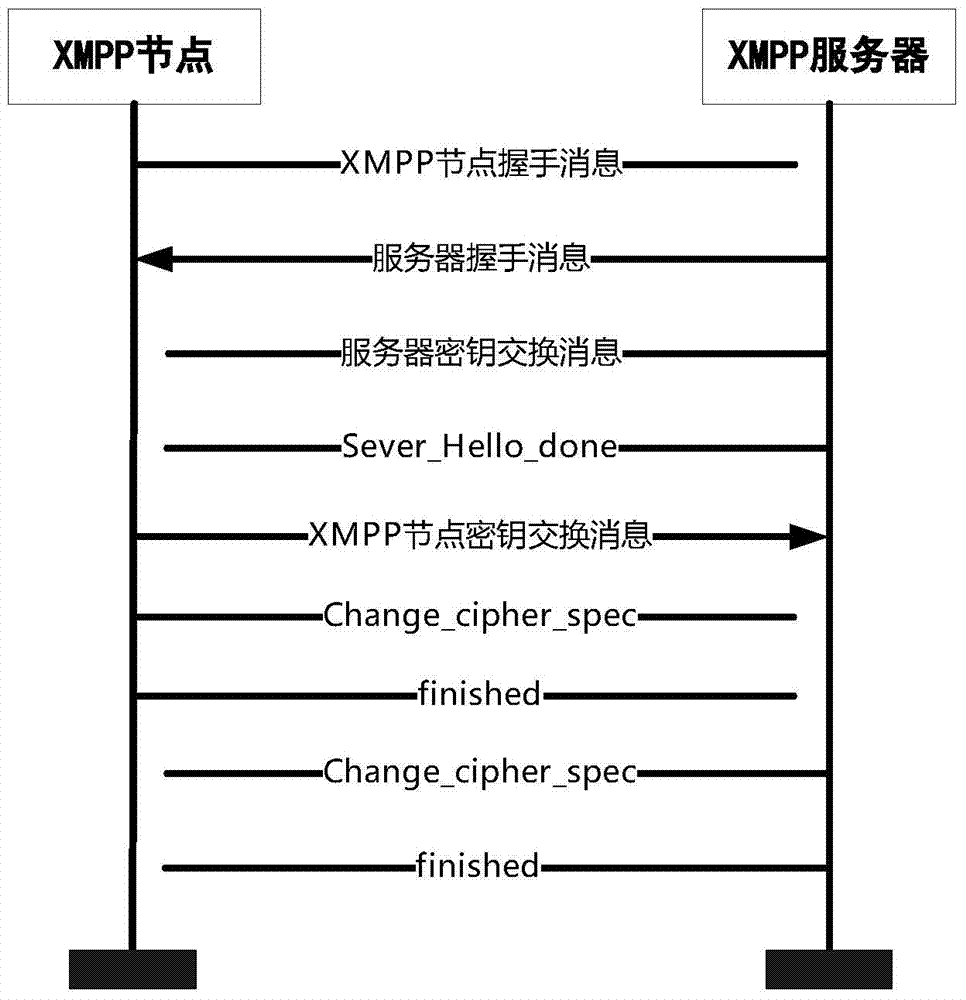
[0055] figure 1 This is a schematic diagram of the work control process provided by the embodiments of the present invention, as shown in the figure: The DIGEST-AES security mechanism, an XMPP security mechanism suitable for sensor networks provided by the present invention, includes: the initialization phase, where XMPP nodes and XMPP servers are encrypted Key negotiation, XMPP node access authentication and authorization services. First, in the initialization phase, the XMPP node registers with the server and submits registration information; when the node needs to access the network, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com