Embedding and extracting method for software watermark
A software watermarking and watermarking technology, applied in the direction of program/content distribution protection, etc., can solve problems such as incomprehension, inability to apply directly, and inapplicable to Android platform application software protection, etc., to achieve the effect of improving concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
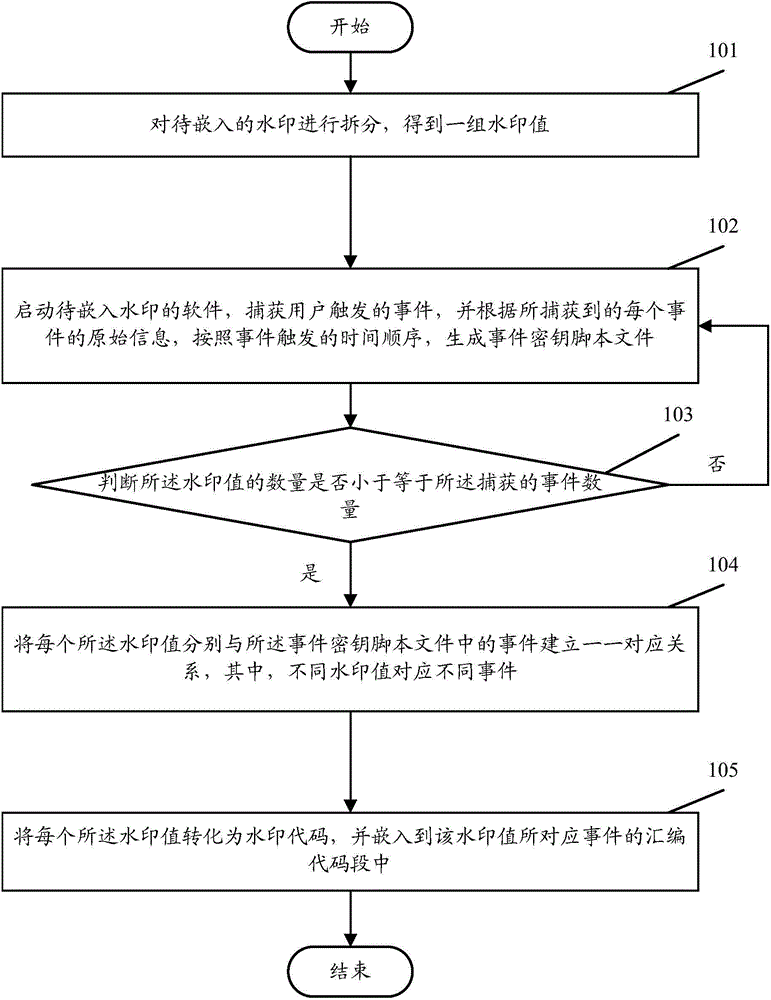
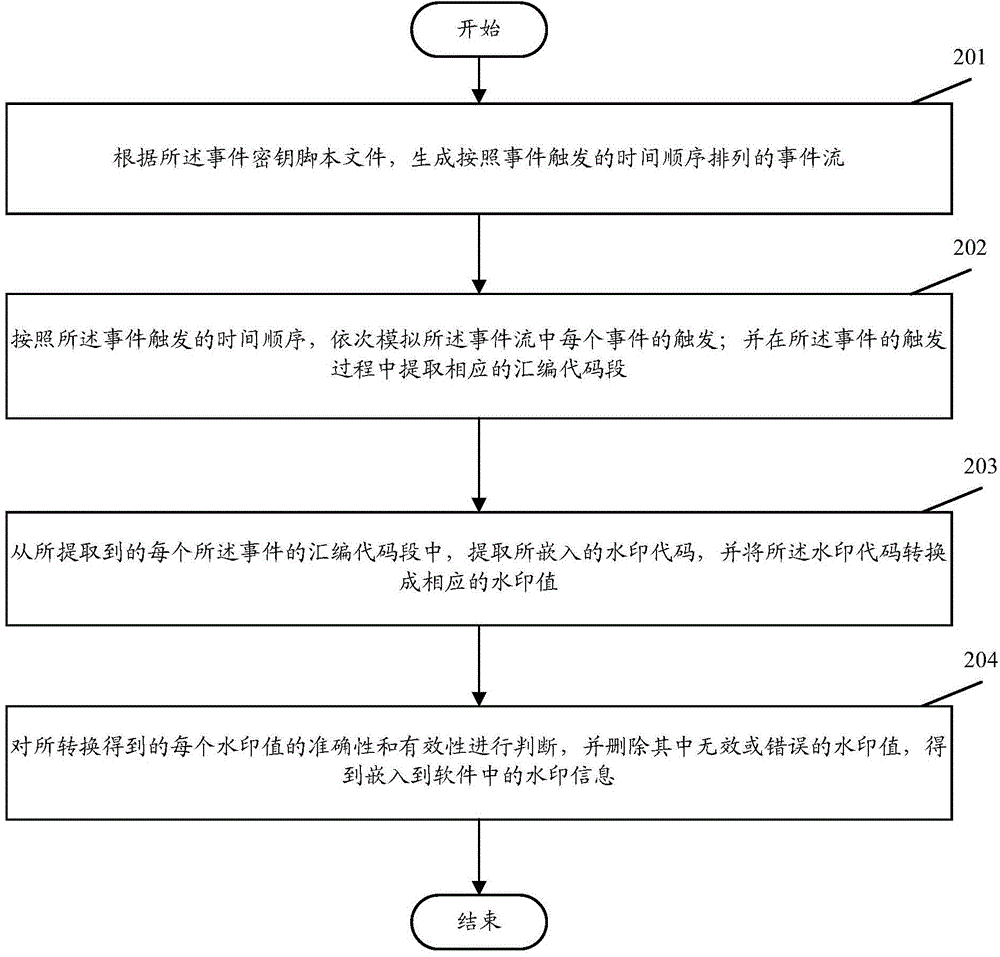
[0036] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0037] The core idea of the present invention is: according to the application event flow (key) of the application software triggered by the user and the watermark information to be embedded, generate the corresponding watermark code, and embed it in the assembly code segment corresponding to each event (that is, the Dalvik byte code segment). In this way, by establishing a logical dependency relationship between the watermark and the program itself, the concealment of the watermark information can be improved. In addition, the embedding of the watermark is carried out based on the assembly code, therefore, the dependence on the source code is avoided, so that the present invention is easy to implement.
[0038] figure 1 It is a schem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com