Method and device for safely operating file upon fingerprint identification sensor
A technology of fingerprint identification and safe operation, applied in computer security devices, instruments, digital data authentication, etc., can solve problems such as loss, troublesome important information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
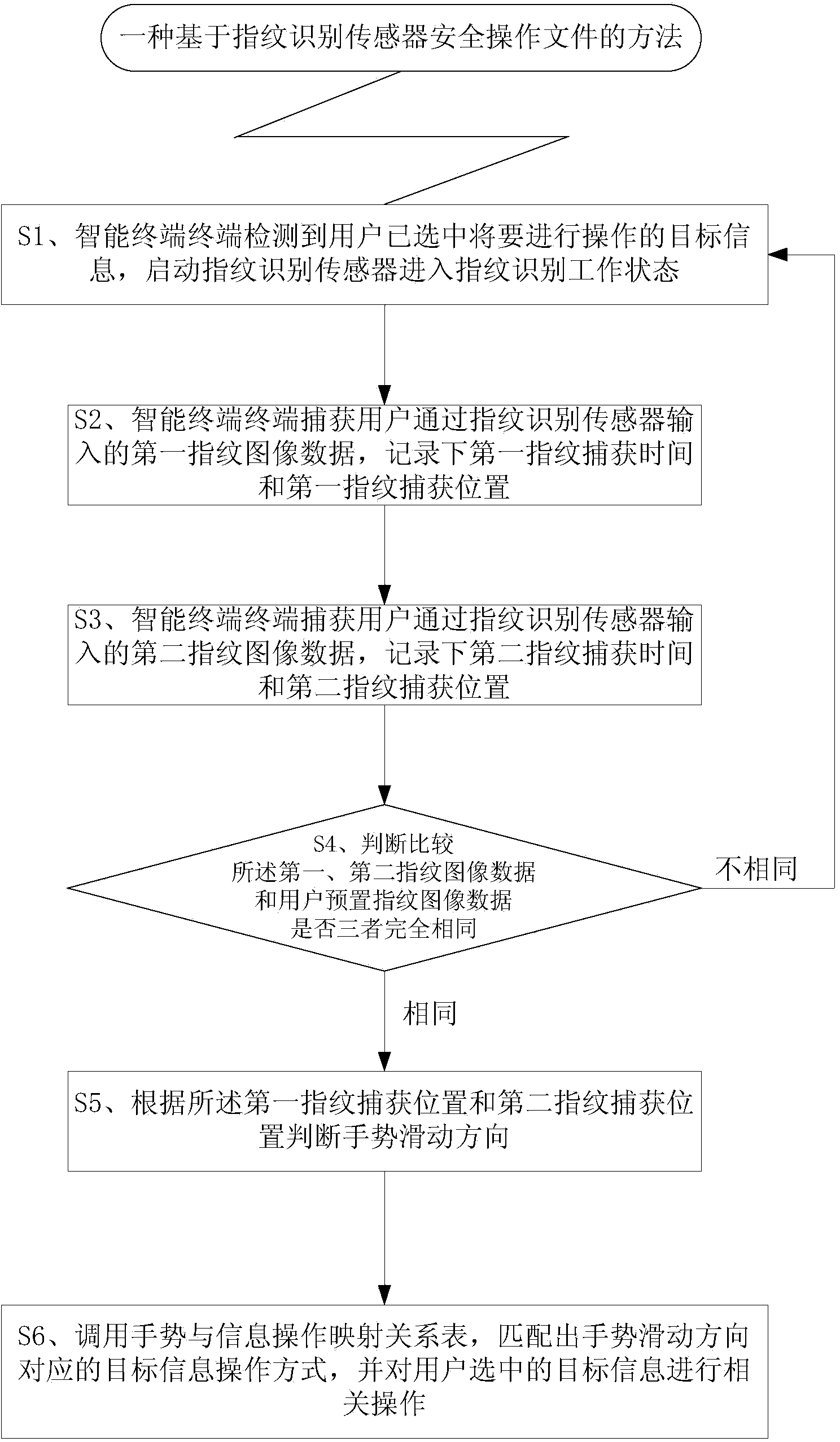
[0068] See figure 1 , figure 1 It is a flow chart of the method for securely operating files based on the fingerprint recognition sensor in the first embodiment. figure 1 The shown method for securely operating files based on a fingerprint recognition sensor is applied to an intelligent mobile terminal equipped with a fingerprint recognition sensor. The fingerprint recognition sensor recognizes gestures, and combined with fingerprint verification, it realizes the encryption function of special operations related to important information, and at the same time ensures the convenience of special operations related to important information without affecting the user's operating experience.
[0069] Wherein the intelligent mobile terminal includes a mobile phone, a tablet computer, a palm Internet device and the like.
[0070] Such as figure 1 As shown, the method for safely operating files based on fingerprint recognition sensors disclosed in this embodiment includes the follow...
Embodiment 2
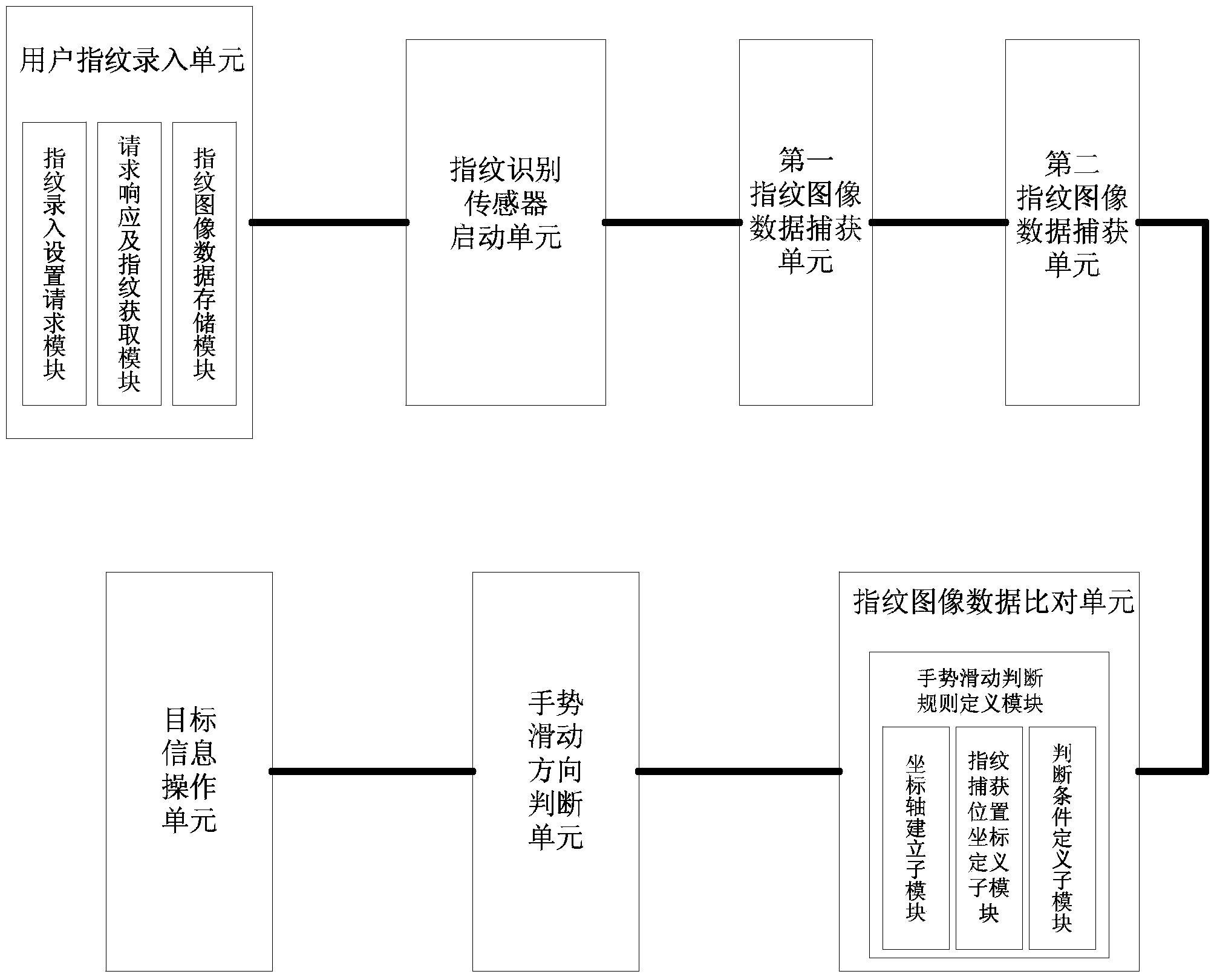
[0096] See figure 2 , figure 2It is a block diagram of a device for securely operating files based on a fingerprint recognition sensor in the second embodiment.
[0097] This embodiment discloses a device for securely operating files based on a fingerprint recognition sensor, which is applied to an intelligent mobile terminal equipped with a fingerprint recognition sensor, wherein the intelligent mobile terminal includes a mobile phone, a tablet computer, and a palm Internet device and the like.
[0098] Such as figure 2 As shown, the device specifically includes the following units:
[0099] A. User fingerprint entry unit,
[0100] Specifically, the unit includes:
[0101] A.1. The fingerprint entry setting request module, which is used for the smart mobile terminal operating system to receive the fingerprint entry setting request sent by the user.
[0102] A.2. Request response and fingerprint acquisition module, which is used for the smart mobile terminal operating ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com