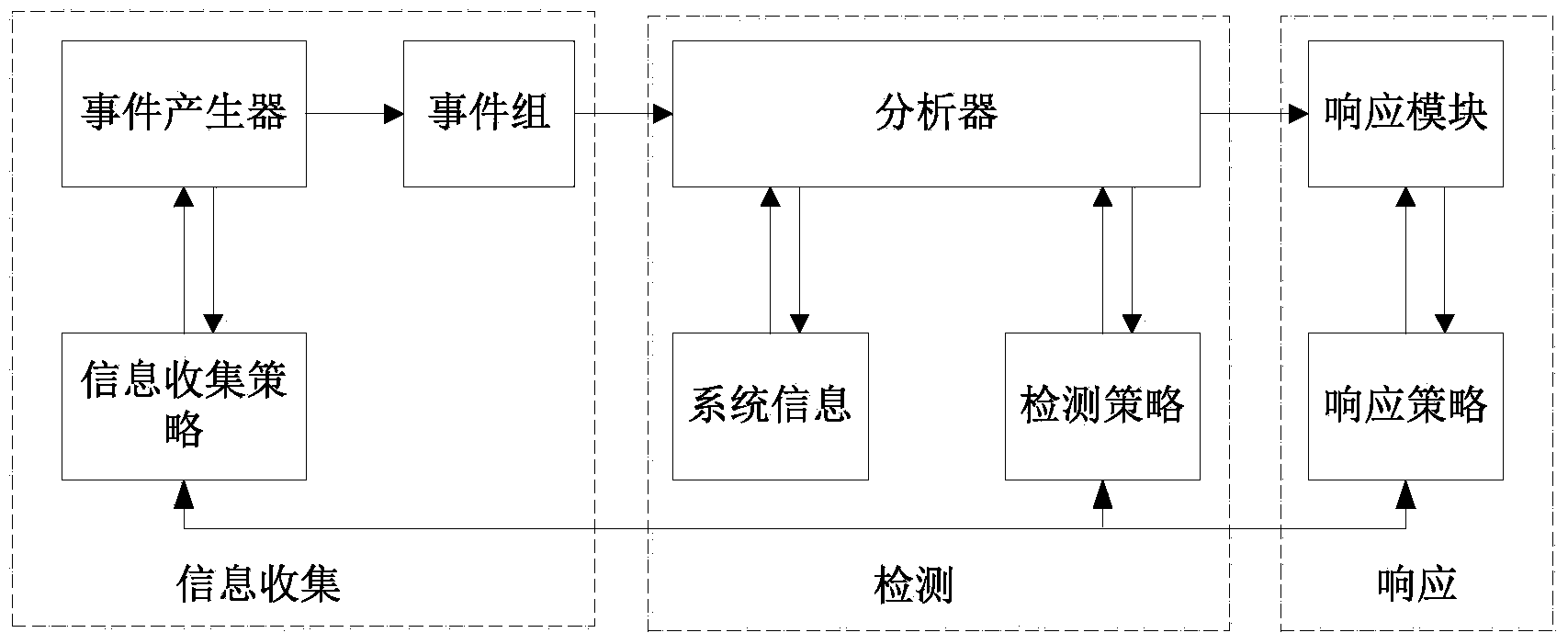
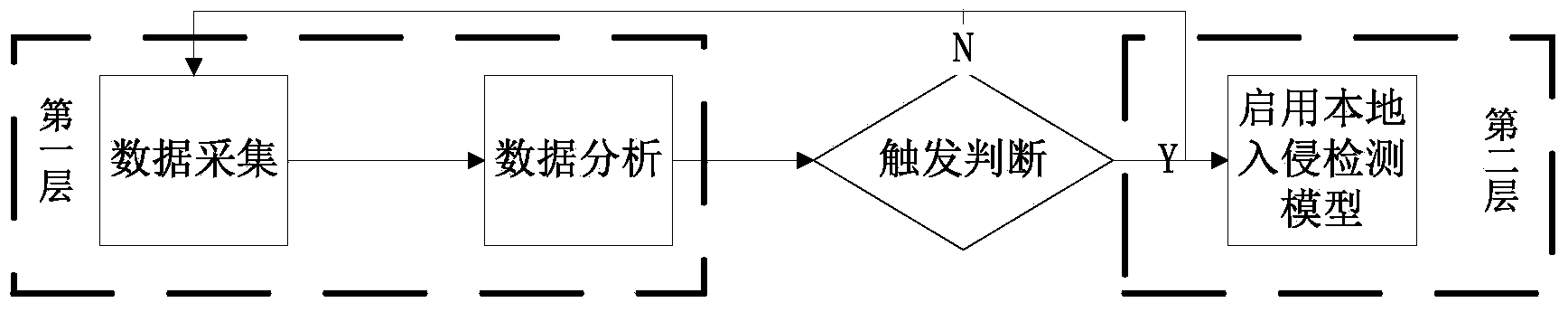
Double-layer trigger intrusion detection method based on flow prediction
A technology for intrusion detection and traffic prediction, applied in advanced technology, security devices, electrical components, etc., can solve problems such as long training time and a large number of training samples
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The present invention will be further described below in conjunction with the accompanying drawings.
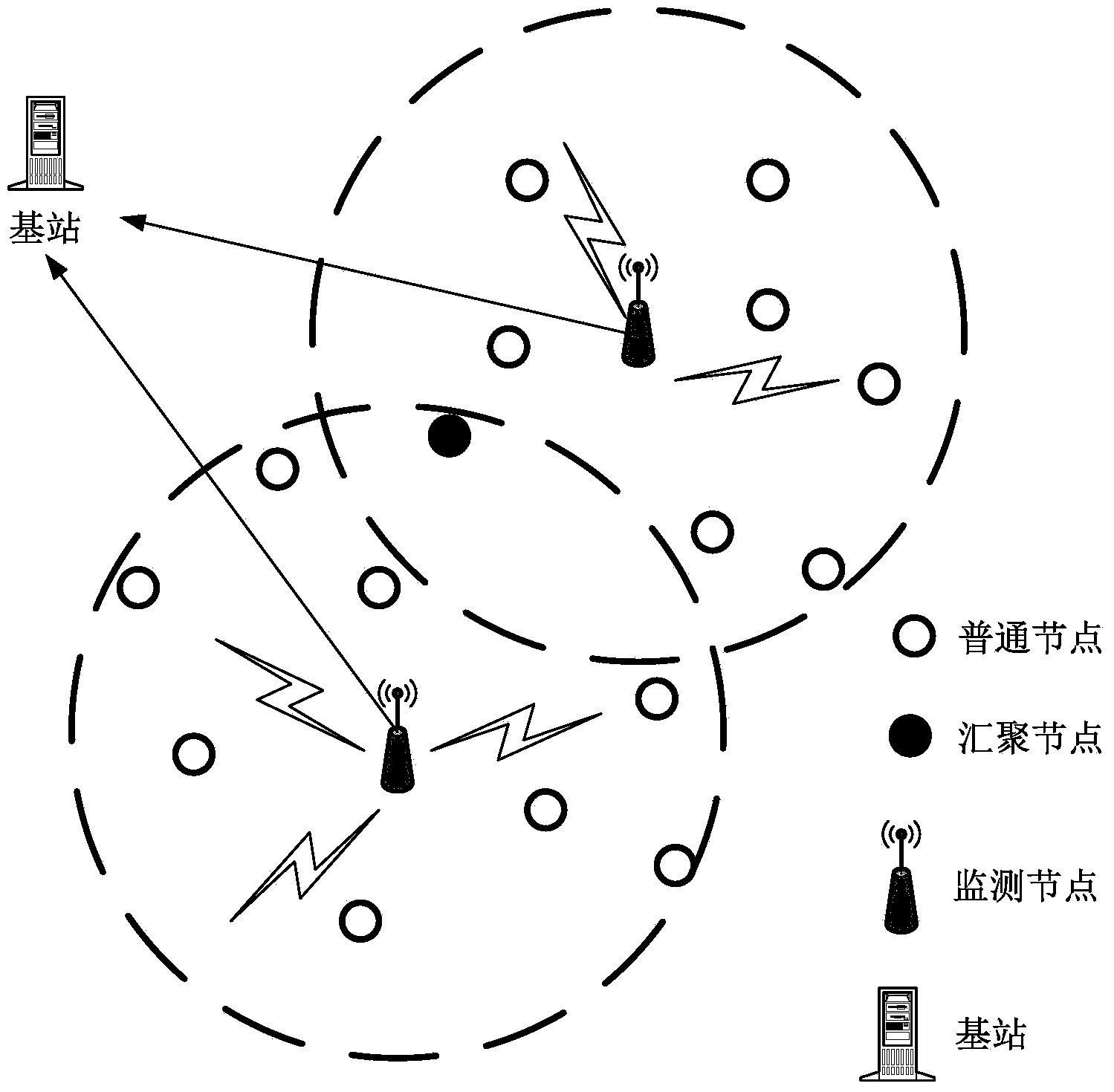
[0062] The invention proposes a double-layer trigger intrusion detection method based on traffic prediction technology in a wireless sensor network. The structure of the intrusion detection system in the wireless sensor network is as follows figure 2 The sensor nodes in the shown wireless sensor network are divided into several areas by the monitoring nodes, and the nodes within the detection radius of the same monitoring node belong to the same area. Since the detection ranges of different monitoring nodes may overlap, the areas divided according to the detection radius of the monitoring nodes may also overlap. Any node in the network belongs to at least one area. The entire network consists of the following 4 elements:
[0063] Ordinary node: sensor node, which is an ordinary node with built-in local intrusion detection system;
[0064] Convergence node: sink no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com