Bidirectional authentication method, device and system
A two-way authentication and authentication information technology, applied in the field of network security, can solve problems such as low security requirements, inability to verify hardware information, and unavoidable connection fraud, so as to achieve the effect of avoiding connection fraud, ensuring security, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] In order to make the technical problems, technical solutions and advantages to be solved by the present invention clearer, the following will describe in detail with reference to the drawings and specific embodiments.
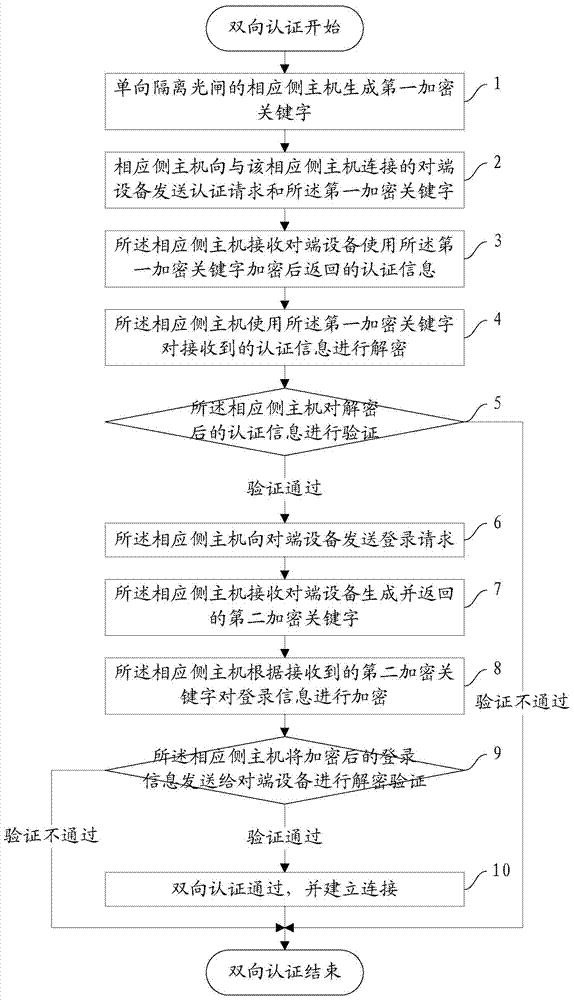
[0071] The present invention provides a two-way authentication method, such as figure 1 shown, including:
[0072] Step 1: The host computer on the corresponding side of the one-way isolation optical gate generates the first encrypted keyword;
[0073] Step 2: the corresponding side host sends an authentication request and the first encrypted keyword to the peer device connected to the corresponding side host;
[0074] Step 3: The host on the corresponding side receives the authentication information returned by the peer device encrypted with the first encryption keyword, and the authentication information includes the hardware information of the peer device;
[0075] In this step, the peer device encrypts the authentication information using the first...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com