Verification method, device, server, service data center and system
A technology for business data and verification methods, applied in the network field, can solve the problem that the verification code technology cannot protect the security of network services, and achieve the effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
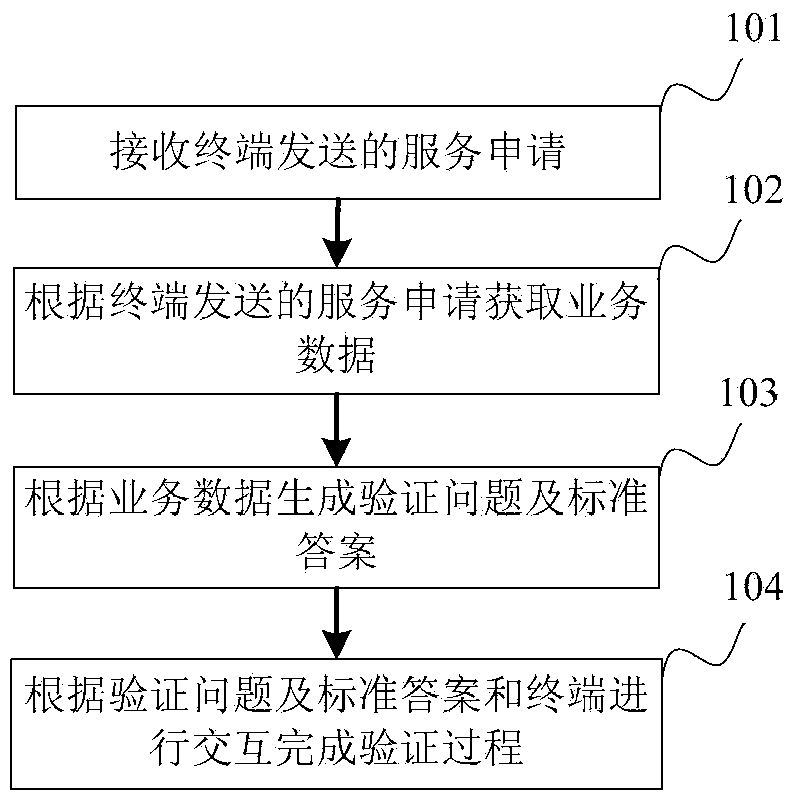
[0036] Please refer to figure 1 , which shows a method flowchart of the verification method provided in Embodiment 1 of the present invention. This verification method includes:
[0037] Step 101, receiving a service application sent by a terminal;
[0038] The server receives the service application sent by the terminal.
[0039] Step 102, obtaining business data according to the service application sent by the terminal;
[0040] The server obtains service data according to the service application sent by the terminal, and the service data is a collection of service characteristics of the service applied for by the terminal.
[0041] Step 103, generating verification questions and standard answers according to business data;
[0042] The server generates verification questions and standard answers based on business data.
[0043] Step 104, interacting with the terminal according to the verification questions and standard answers to complete the verification process;
[...
Embodiment 2
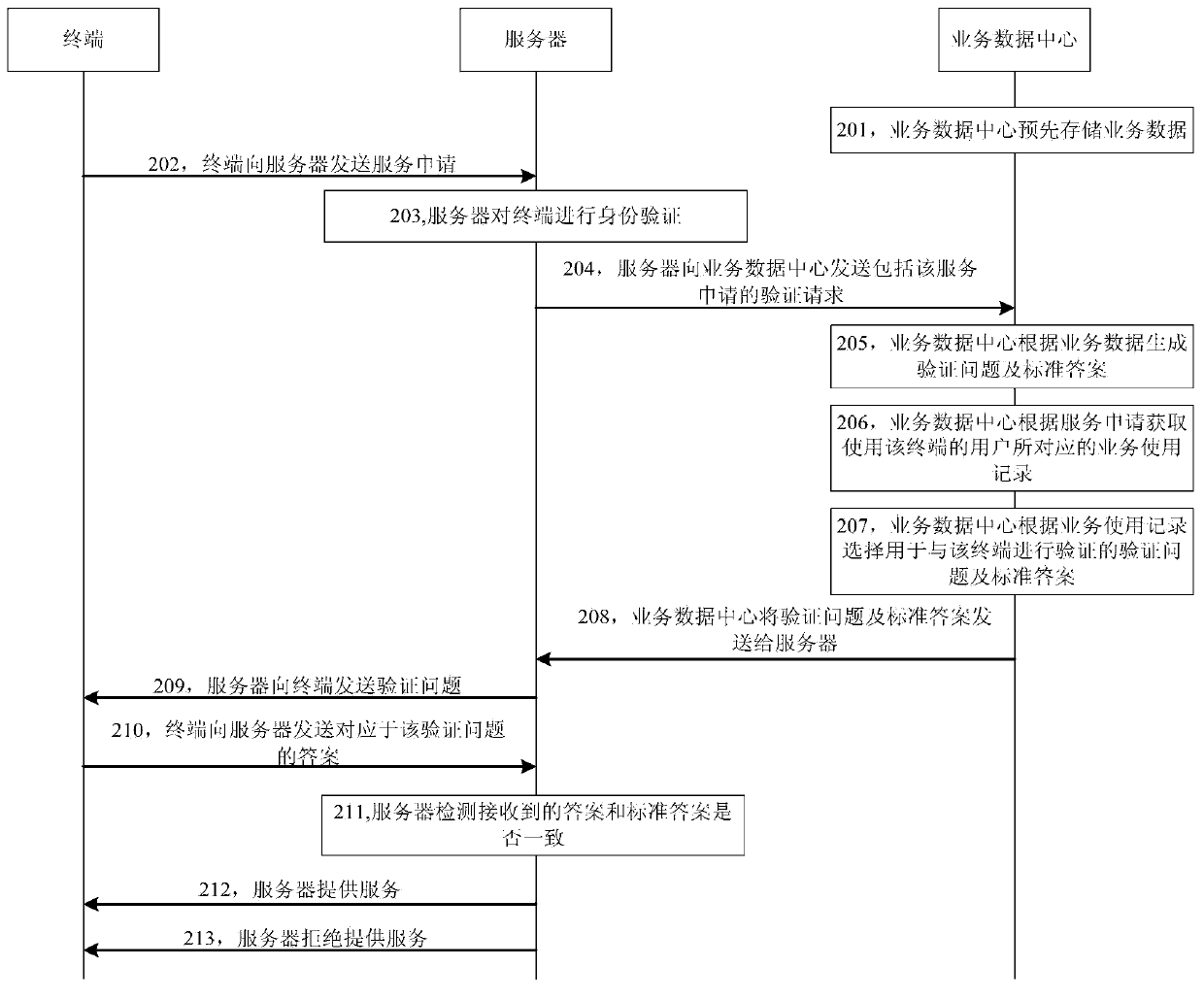
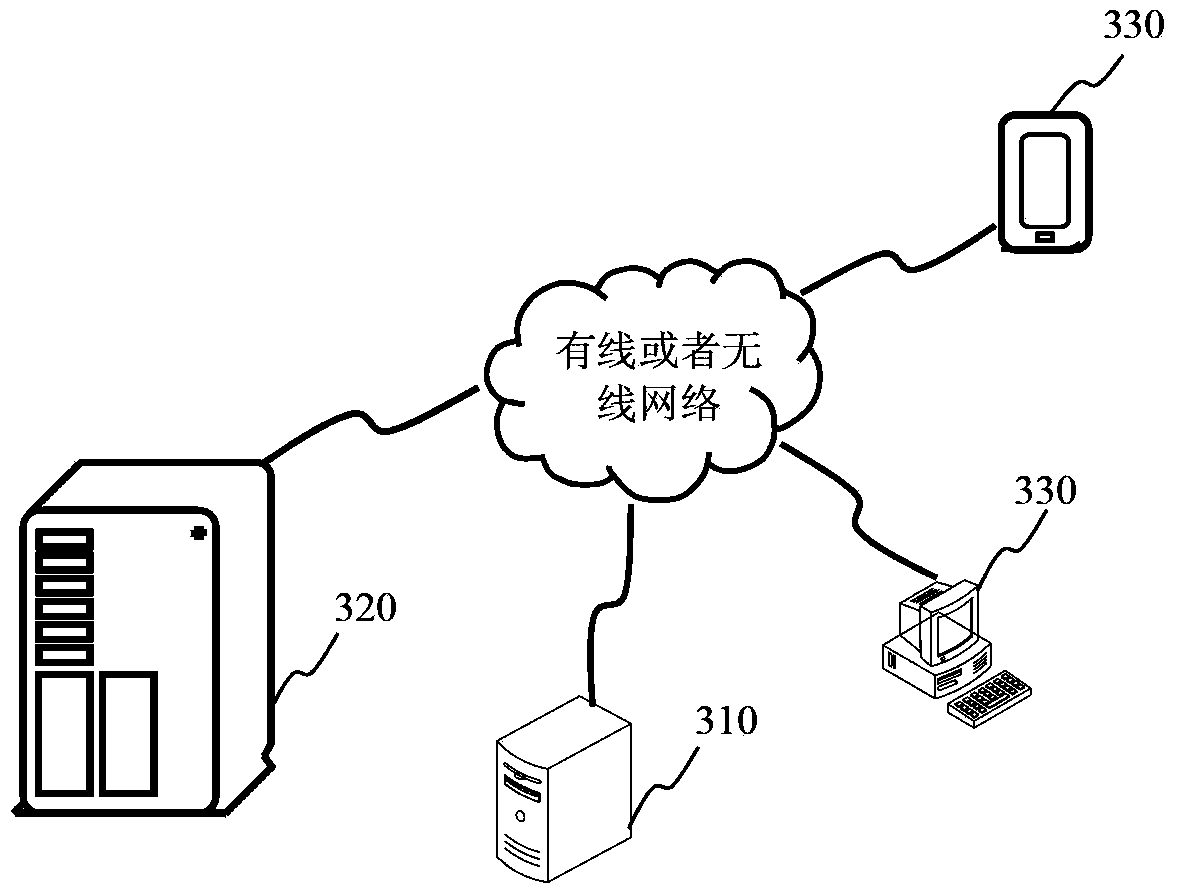
[0047] Please refer to figure 2 , which shows a method flowchart of the verification method provided by Embodiment 2 of the present invention. In the embodiment of the present invention, the verification method is applied to image 3 The illustrated implementation environment is taken as an example for illustration. The implementation environment includes a server 310, a business data center 320, and a terminal 330. The terminal may be any one of a desktop computer, a notebook, a smart phone, and a tablet computer. The verification methods include:
[0048] Step 201, the business data center stores business data in advance;
[0049] The business data center 320 stores business data in advance, and the business data is a collection of business characteristics of services. The business features include at least one of the conditions required for starting the business functions in the service, the limited attributes of the business functions in the service, the unique feature...
Embodiment 3
[0099] Please refer to Figure 4 , which shows a method flowchart of the verification method provided by Embodiment 3 of the present invention. In the embodiment of the present invention, the verification method is applied to Figure 5 The illustrated implementation environment is taken as an example for illustration, and the implementation environment includes a server 510 and a terminal 520, and the terminal may be any one of a desktop computer, a notebook, a smart phone, and a tablet computer. Different from the previous embodiment, in this embodiment, the server generates verification questions and standard answers according to pre-stored business data, and then interacts with the terminal to complete the verification process according to the generated verification questions and standard answers; instead of using business data The center generates verification questions and standard answers, and then sends the verification questions and standard answers to the server, so ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com