Distributed hash table network-based anonymous communication method
A distributed hash table and anonymous communication technology, which is applied in the field of computer networks, can solve the problems of P2P network user privacy threats, affecting the normal operation of P2P networks, and not considering user privacy protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
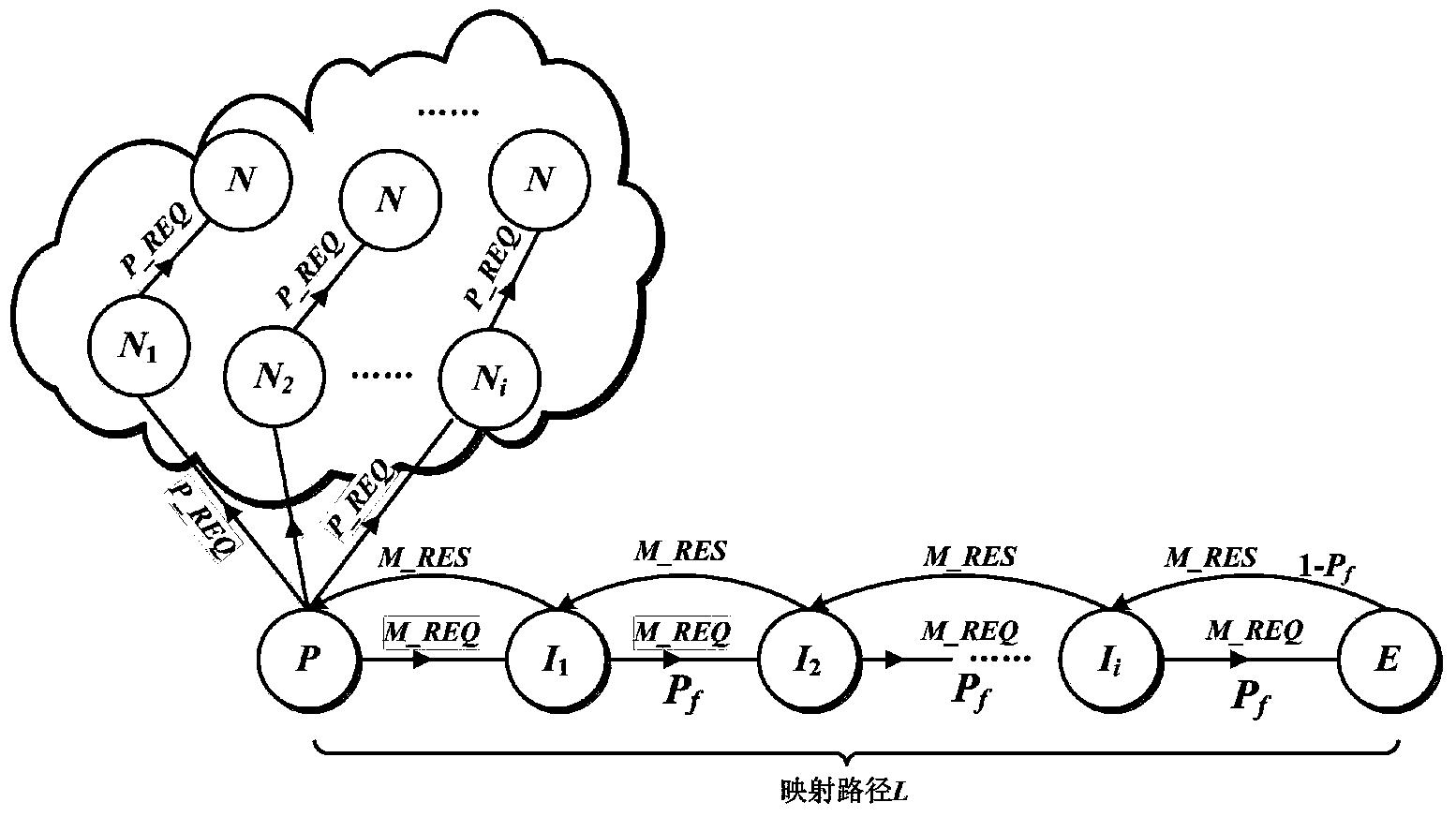
[0062] The overall block diagram of the anonymous communication scheme based on the distributed hash table (DHT) network is as follows: figure 1 As shown, it includes the anonymous publishing process of resources, the anonymous search process of resources and the anonymous transmission process of resources. Specifically, the anonymous publishing process of resources is as follows: figure 2 As shown, the specific steps are as follows:
[0063] Step 1. At the initial moment, in the DHT network, the user node P owns a resource File and hashes it:
[0064] Hash(File)=FID
[0065] The obtained ID of the resource is set as FID. Node P selects a neighbor node I with the longest survival time from its routing table 1 , send the resource mapping message M_REQ (Map Request) to node I 1 , I 1 After receiving the M_REQ message, it will choose the probability P f1∈[0, 1] continue to forward backwards, or with probability (1-P f1 ) terminates forwarding to become the mapping node E...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com