Abnormity processing method and abnormity processing device
An abnormal and abnormal event technology, applied in the field of information security, can solve the problem of not saving the communication state and the information input by the user.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
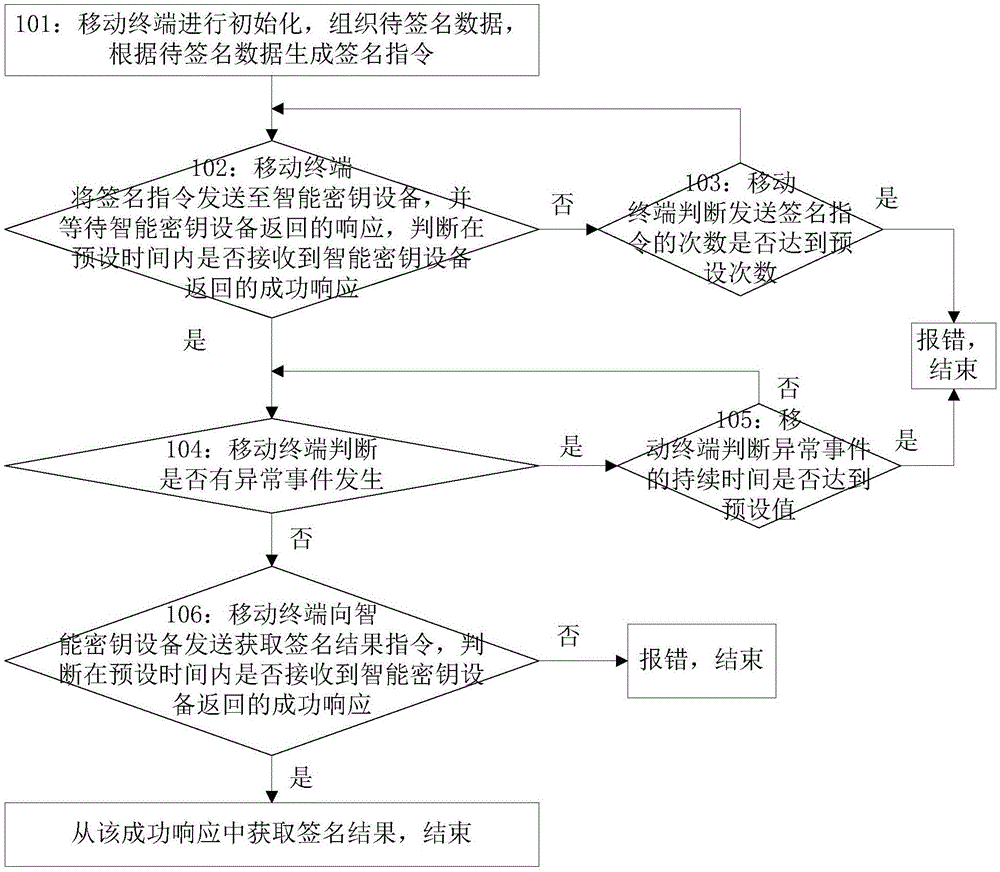
[0101] Embodiment 1 of the present invention provides a method for handling exceptions, such as figure 1 shown, including:
[0102] Step 101: The mobile terminal initializes, organizes the data to be signed, and generates a signature instruction according to the data to be signed;
[0103] In this embodiment, the initialization specifically includes: setting the screen status to highlight, initializing the number of PIN code verifications, setting the number of signature command sending times to the initial value, setting the number of signature result acquisition times to the initial value, resetting the abnormal event flag, and starting System event monitoring service.
[0104] Among them, after the mobile terminal is initialized, it also includes: receiving the PIN code input by the user, judging whether the PIN code is correct, if so, organizing the data to be signed, otherwise reporting an error, and ending;
[0105] Specifically, the mobile terminal generates a verific...
Embodiment 2
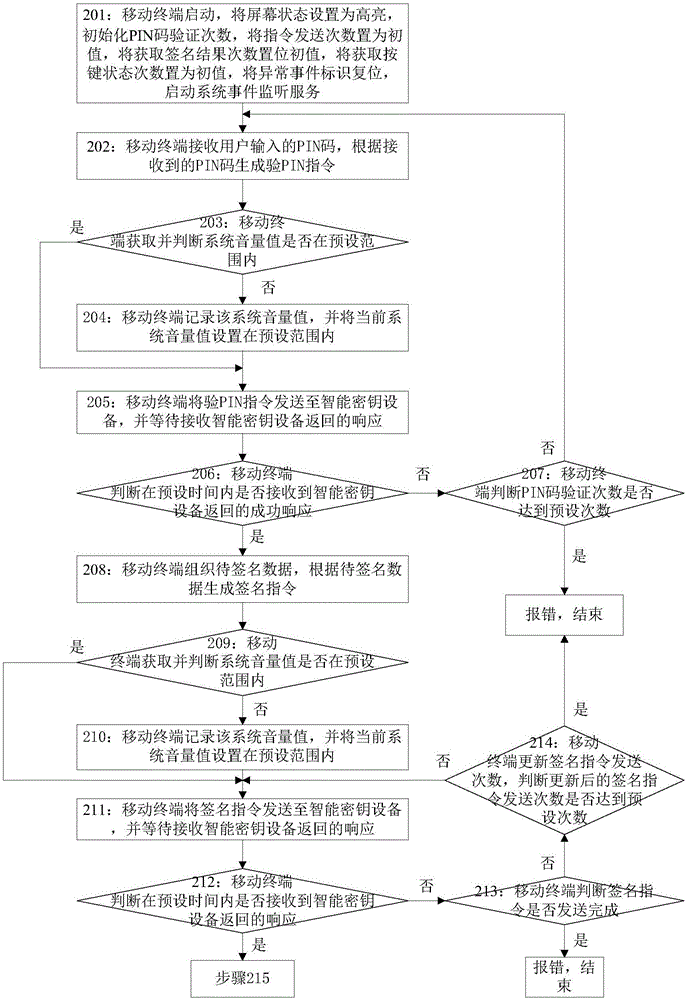
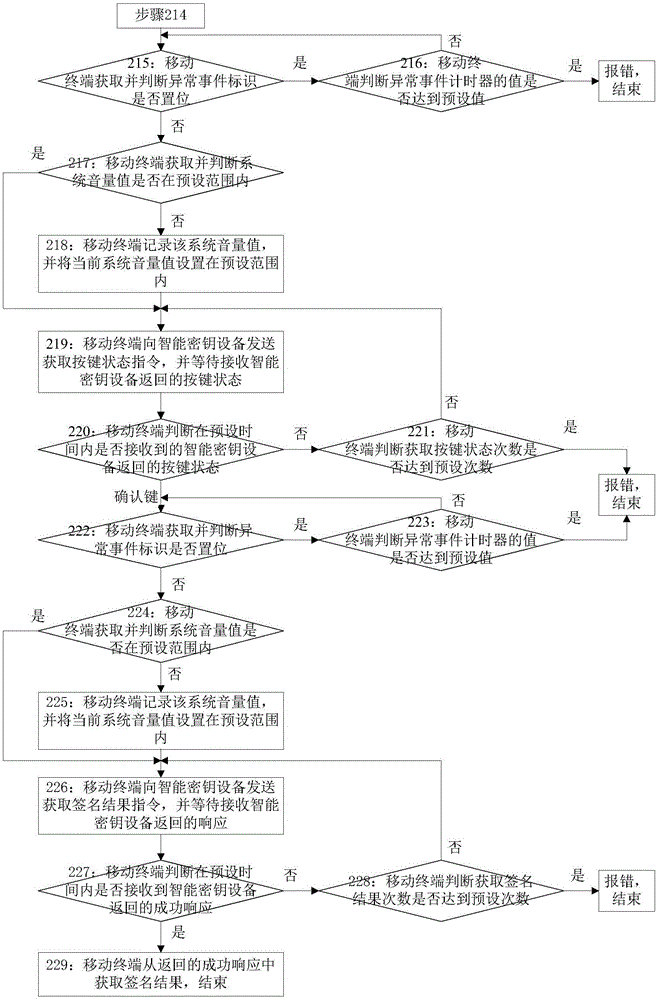
[0128] Embodiment 2 of the present invention provides a method for handling exceptions, such as figure 2 and image 3 shown, including:
[0129] Step 201: Start the mobile terminal, set the screen state to be highlighted, initialize the number of times of PIN code verification, set the number of command sending times as the initial value, set the number of times of obtaining signature results as the initial value, and set the number of times of obtaining key state as the initial value, Reset the abnormal event identification and start the system event monitoring service;
[0130] Wherein, the mobile terminal sets the screen state to be highlighted, specifically: the mobile terminal sets the idleTimerDisabled system attribute of the mobile terminal to YES, so as to prevent a black screen abnormal event from occurring when the communication is not completed;
[0131] In this embodiment, the mobile terminal receives the event message sent by the system to the mobile terminal t...
Embodiment 3
[0198] Embodiment 3 of the present invention provides a device for handling exceptions, such as Figure 4 shown, including
[0199] Instruction generation module 1: used to organize the data to be signed, and generate signature instructions according to the data to be signed;
[0200] Sending module 2: used to send the signature command to the smart key device, and also used to send the command to obtain the signature result to the smart key device;
[0201] Receiving module 3: used to receive the response returned by the smart key device;
[0202] The first judging module 4: used to judge whether a successful response returned by the smart key device is received within a preset time; it is also used to judge whether the number of times of sending signature instructions reaches the preset number of times;
[0203] The second judging module 5: used for judging whether there is an abnormal event when the first judging module judges that the successful response returned by the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com