Data packet forwarding method, device and system
A forwarding method and forwarding device technology, applied in the field of communication, can solve problems such as low security, complicated user identity verification and authentication process, user identity information leakage, etc., and achieve enhanced security, simplified identity verification and authentication process, The effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
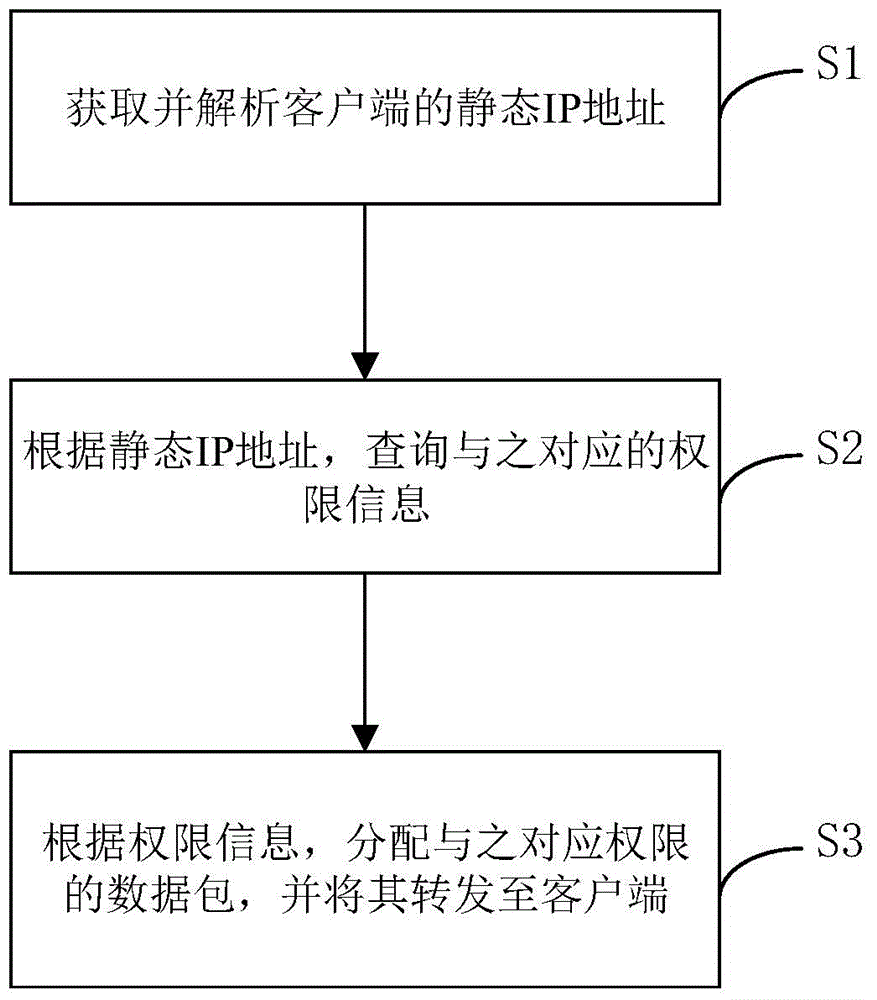
[0058] In this embodiment, before obtaining and analyzing the static IP address of the client, it also includes assigning a static IP address to the client establishing a communication connection with it through the server.
[0059]First, a Tun-based virtual NIC interface is established between the server and the client. The data packet receiving and sending operations of the virtual NIC interface are not directly associated with the real physical NIC, but the data packets are forwarded through user space. For example, under linux, there are many ways to realize the interaction between core state and user state data packets through the virtual network card interface: you can create special sockets with common sockets, and use sockets to realize data interaction; create files through the proc file system To perform data interaction; you can also use the device file, accessing the device file will call the corresponding routine of the virtual network card interface, the virtual n...
Embodiment 2
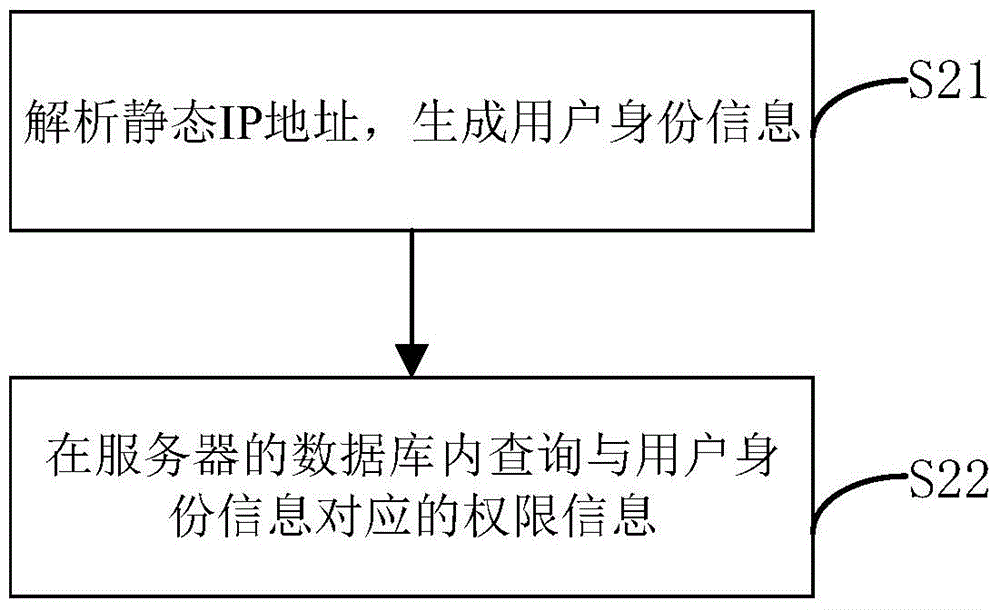
[0063] figure 2 figure 1 Shown is a flow chart of specific steps for querying the corresponding authority information according to the static IP address. This step specifically includes:
[0064] S21, analyzing the static IP address to generate user identity information. The static IP address is a line of character strings. In this embodiment, the character string is used as the identity information of the user. On the server side, the character string is directly verified to identify the identity information of the client; after identity information identification is completed, the character string can be The format is adjusted accordingly to match the query format within the database.
[0065] S22. Query the authority information corresponding to the user identity information in the database of the server. For example, on the server side, corresponding permissions are assigned to different IP addresses, or corresponding permissions are assigned to IP addresses under dif...
Embodiment 3
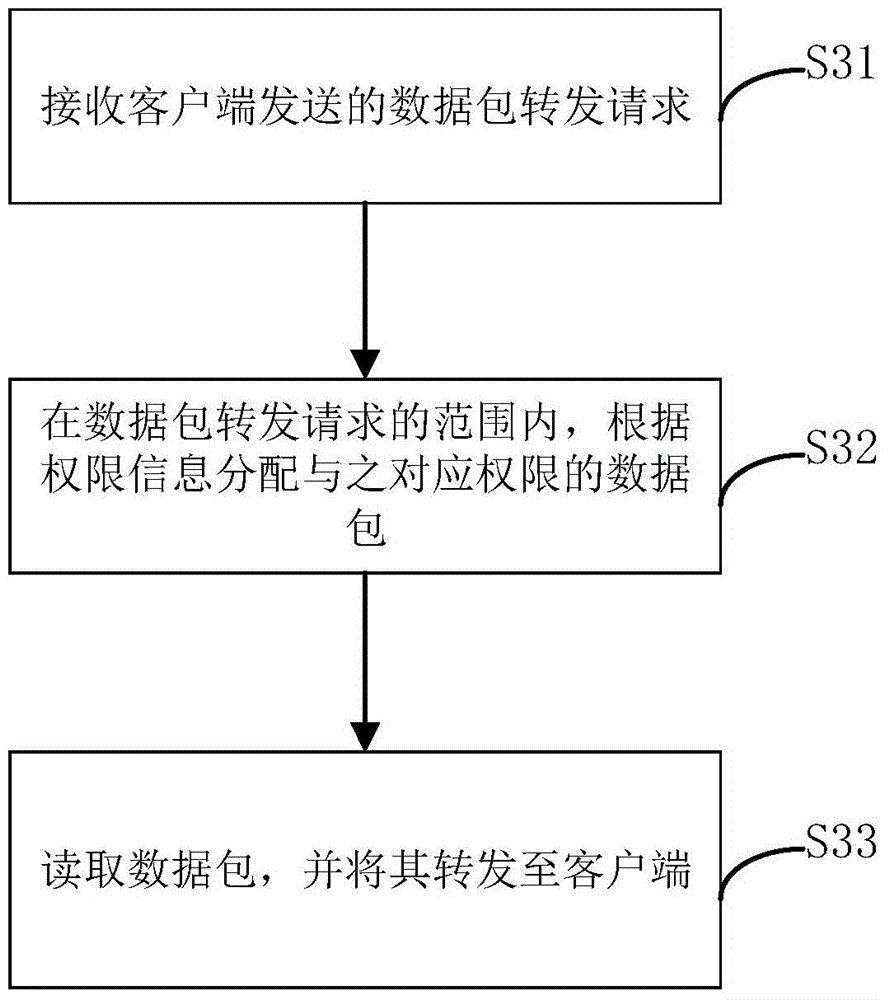
[0068] image 3 yes figure 1 Shown is a flow chart of specific steps of assigning data packets with corresponding permissions according to the permission information and forwarding them to the client. This step specifically includes:
[0069] S31. Receive a packet forwarding request sent by the client. It can be understood that other clients may send the data packet forwarding request to the client, or the client may send the data packet forwarding request to the server.
[0070] S32. Within the scope of the data packet forwarding request, assign a data packet corresponding to the authority according to the authority information. It can be understood that on the server side, there are many ways to distribute data packets: store the data packets to be sent according to the authority level from high to low, and then allocate the data packets of this level according to the authority level of the client; Within the access rights, arbitrarily select the data packets to be forwa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com