Method for realizing message protection in reading and message destruction after reading in mobile terminal instant communication
A technology of a mobile terminal and an implementation method, which is applied in the directions of wireless communication, message/mailbox/announcement, electrical components, etc., can solve the problems of message security protection methods that have not yet been seen in mobile terminals, and achieve the improvement of instant communication security, privacy protection and security. , the effect of broad application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
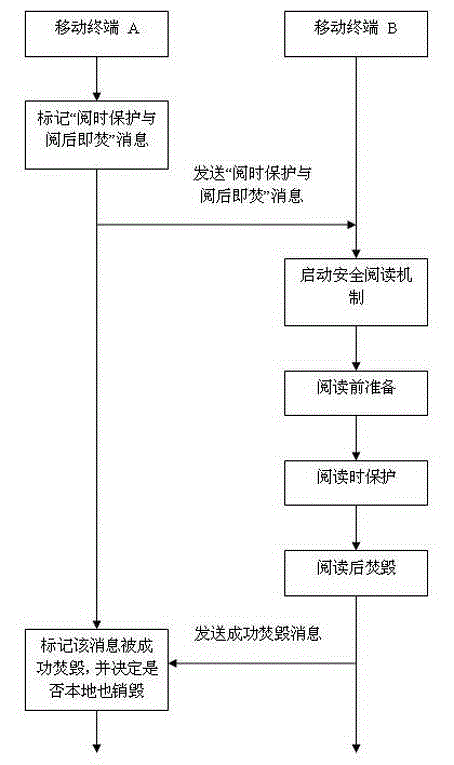
[0018] The method for implementing instant message protection and burning after reading of mobile terminal instant messaging in the present invention is to install a security protection module on the mobile terminal, and the security protection module is set in the application layer of the Android operating system of the mobile terminal, such as figure 1 As shown, the security protection module processes sensitive messages according to the following steps:
[0019] Step S1: When mobile terminal A sends a sensitive message that needs to be protected to mobile terminal B, mobile terminal A marks the sensitive message as a "protected while reading and burns after reading" message through its security protection module, and then sends to mobile terminal B;
[0020] Step S2: After the mobile terminal B receives the message, the security protection module on it judges whether the received message is a "protected while reading and burns after reading" message, and if so, starts the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com