Testing method and system for Android application permission leakage vulnerabilities
A technology of application permissions and testing methods, applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., can solve the problems of lack of strict specification of feature definition mode, false positives in vulnerability detection, inability to decompile Android applications into Java code, etc. , to achieve the effect of reducing the detection false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
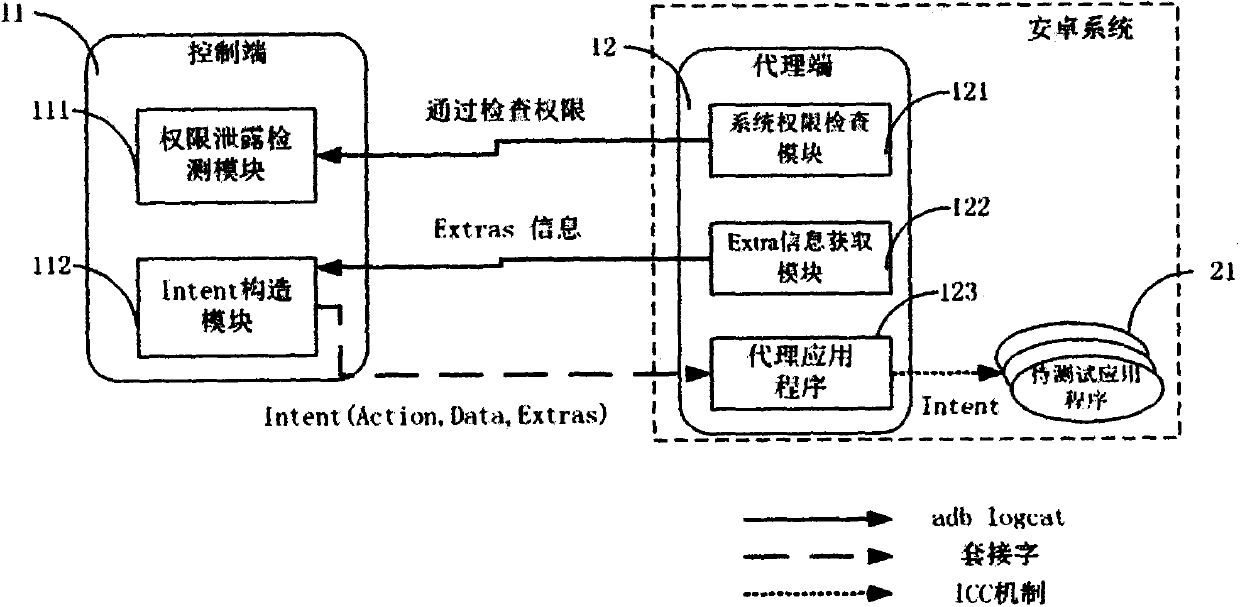
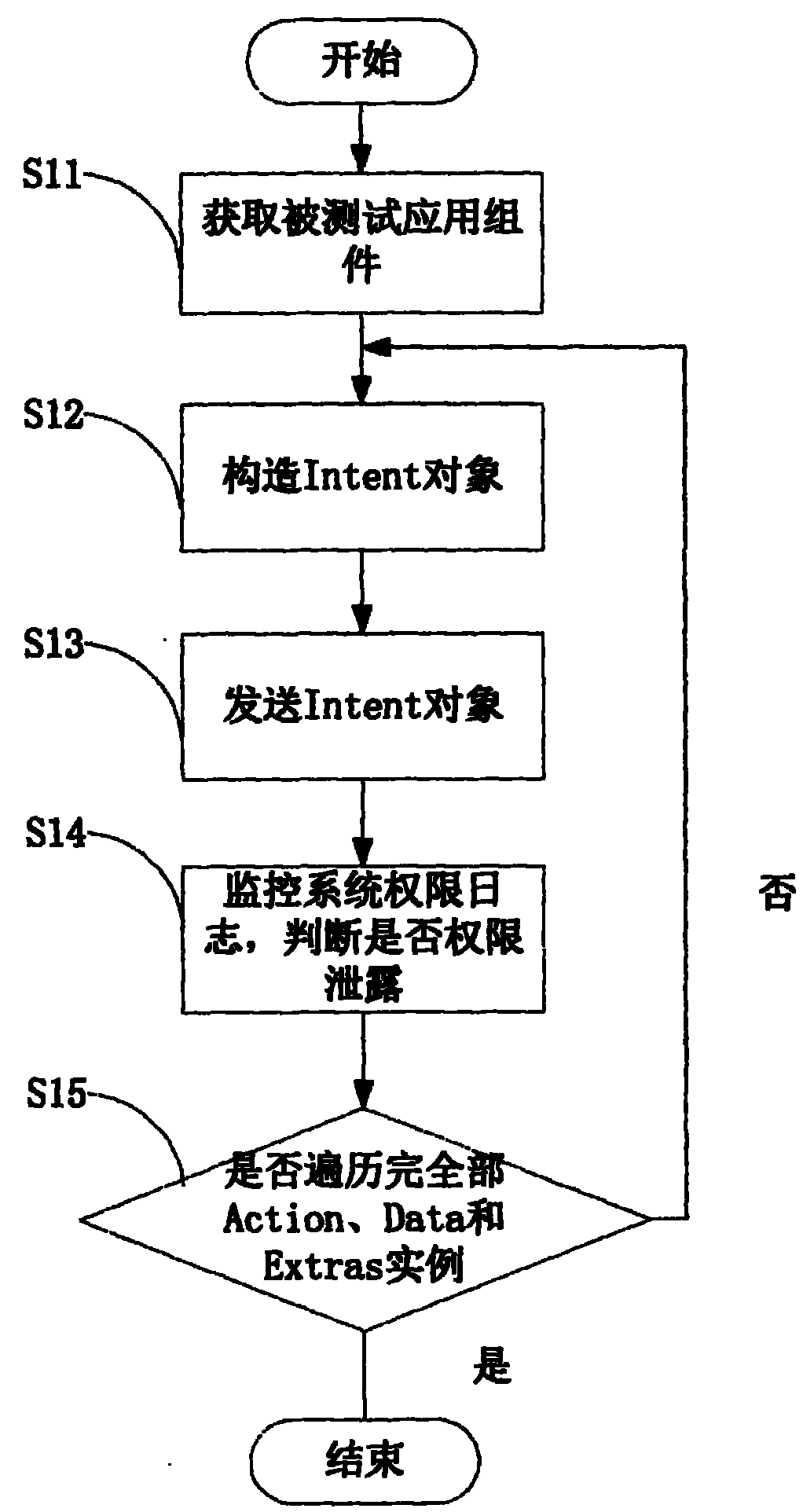
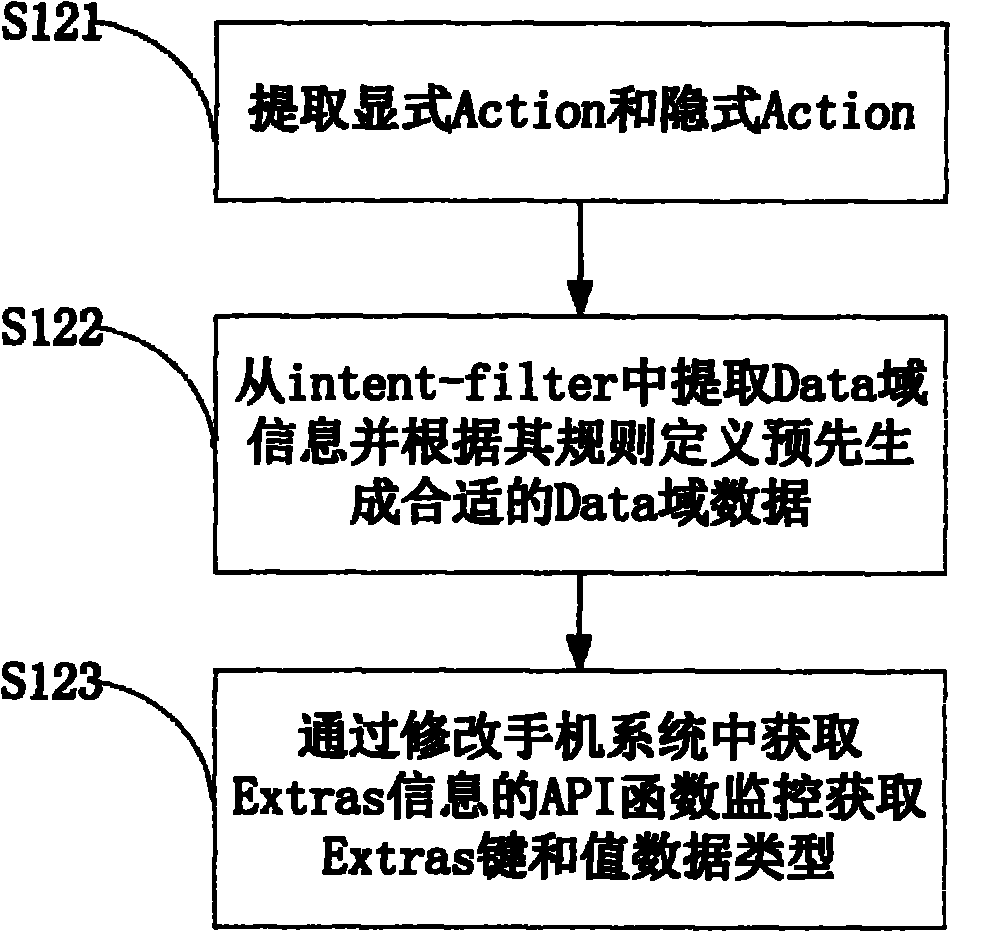
[0021] The inventor found through research that: ICC (Inter Component Communication) is a communication mechanism between Android application components. There are three components in the Android application that use the ICC mechanism to communicate: Activity, Service, and Broadcast Receiver. These three components can communicate through the Intent object, and the Intent object contains the data information transmitted during the communication process. There are two types of Intent: explicit and implicit. The explicit Intent contains the component name to specify the target component. The implicit Intent does no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com