A Location Privacy Protection Method in Internet of Things Authentication
A privacy protection, Internet of Things technology, applied in the field of location privacy protection in IoT authentication, can solve problems such as label location exposure, and achieve the effect of protecting location privacy, ensuring location privacy security, and the method is simple and efficient
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below in conjunction with the accompanying drawings.
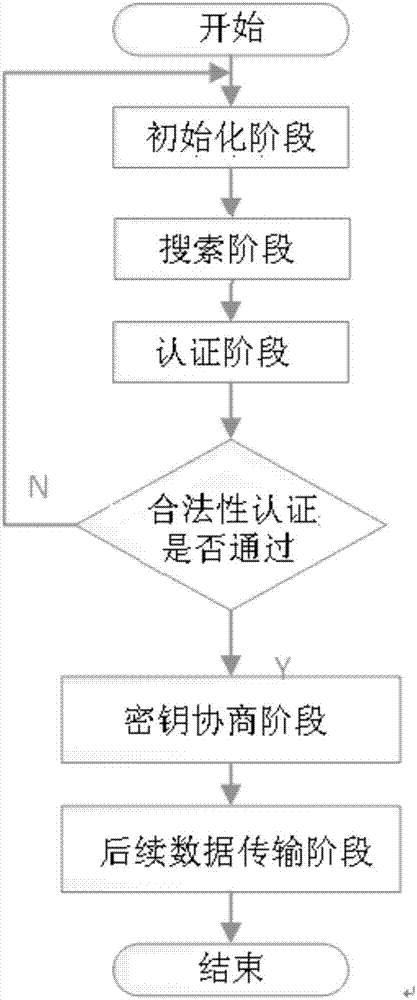
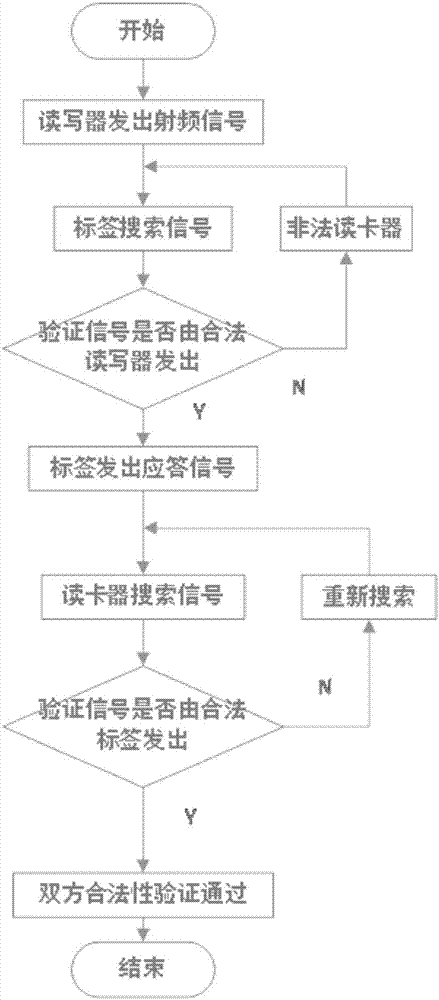
[0034] The present invention provides a location privacy protection method in Internet of Things authentication. The main idea is to divide the perception layer authentication into two steps: the first step is that the reader / writer sends out information and searches for radio frequency tags. The radio frequency tag will verify the information with the legality of the reader's identity, and determine whether to return an answer; the second step, the radio frequency tag sends a message to complete the authentication answer. The reader will verify the information with the legality of the radio frequency tag to determine whether it passes the verification.
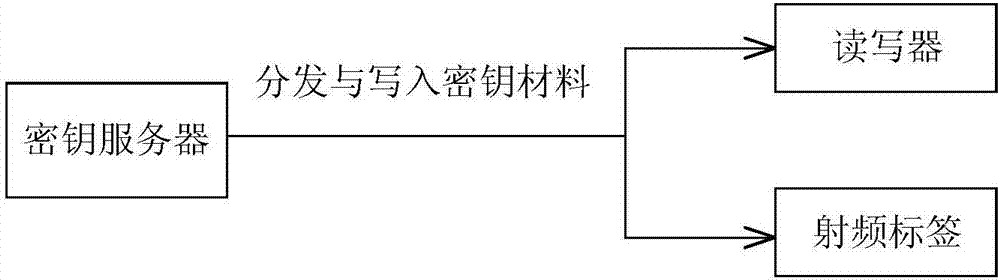
[0035] The main framework of the present invention is as follows: distribution of key material, design of search and authentication process, negotiation and generation of key. Two types of entities are defined: reade...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com