A wpa shared key cracking system based on gpu cluster
A GPU cluster, shared key technology, applied in the field of password cracking, can solve the problems of low cracking speed, poor scalability, limited cracking ability, etc., to achieve the effect of improving cracking speed, load balancing, and improving cracking performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
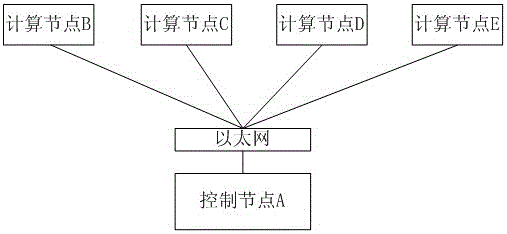
[0023] A WLAN contains at least one wireless access point AP and one user (client). The WPA / WPA2-PSK authentication process is a four-step handshake process. The client generates a verification value MIC through the input key, AP name (SSID), user MAC address, random number Nonce and other data and sends it to the AP. Compare with the stored correct MIC value, if they are consistent, the identity authentication will be passed, otherwise it will be rejected. The main difference between WPA and WPA2 is that WPA uses the HMAC-MD5 algorithm in the last step of generating the MIC value, while WPA2 uses the HMAC-SHA1 algorithm. Therefore, the method of the present invention is applicable to WPA and WPA2.
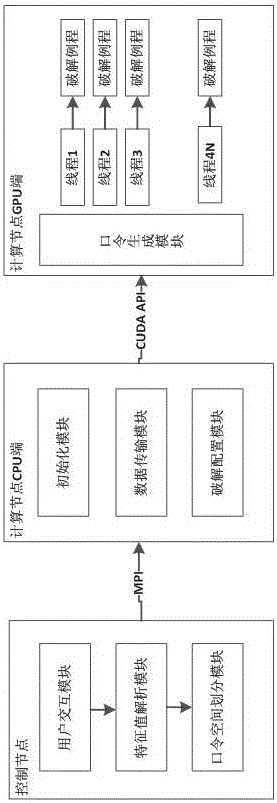
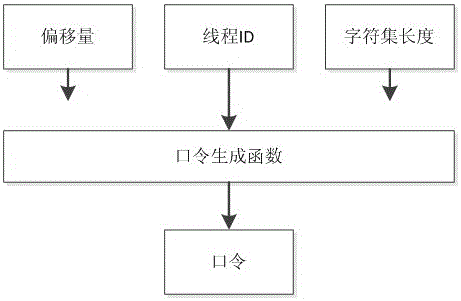
[0024] A GPU cluster is a cluster system based on GPU computing nodes, and its main computing work is completed by the GPU of ea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com