A Malicious Code Detection Method Based on Dendritic Cell Algorithm
A malicious code detection, dendritic cell technology, applied in the field of information security, can solve problems such as unreasonable, DC detection failure, too simple, etc., to achieve the effect of improving detection ability, reducing false positive rate, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
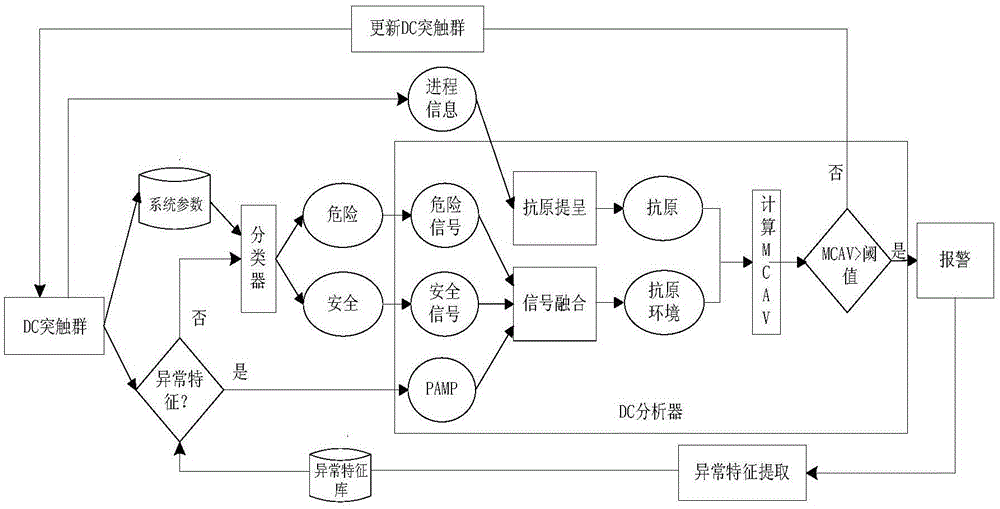
[0028] The design scheme of the present invention emphasizes detection efficiency and false positive rate. The former is mainly achieved by effectively reducing the parameters of the original algorithm and simplifying the analysis process under the premise of ensuring the correctness of the algorithm; the latter is based on the original DCA algorithm by introducing concepts such as system state parameters and support vector machines. Solve the problem of signal generation and classification in DCA-based malicious code detection.
[0029] The method is as follows:
[0030] The dendritic cells distributed in the computer monitor the operation of the computer system, and when a new process is detected in the system, the detection program is activated;
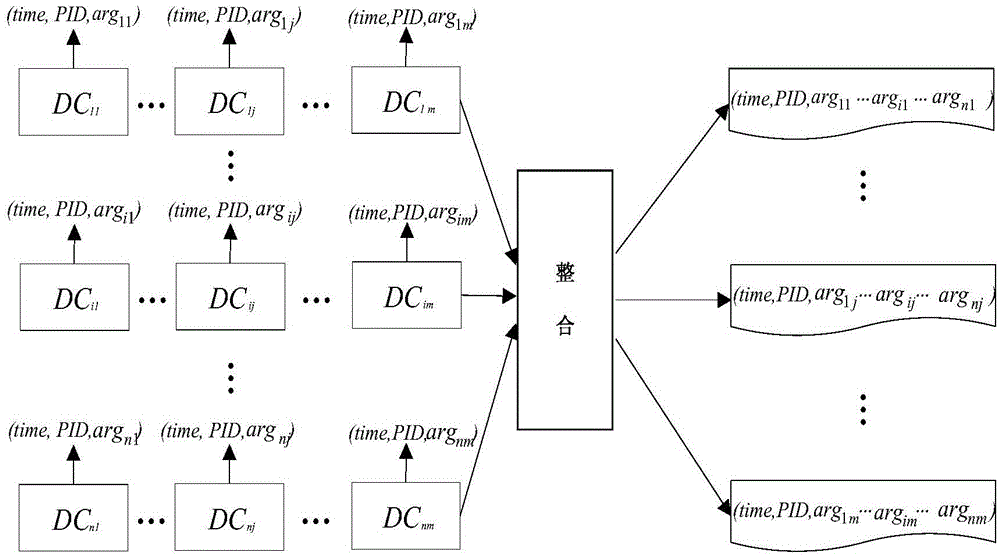
[0031]First, the dendritic cell DC (Dendritic Cell,) records the system status parameters during the running of the process at a certain collection frequency, including: memory utilization, CPU utilization, registry values and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com