Survival authentication method on basis of identification cards and composite biological feature recognition
A biometric identification and authentication method technology, applied in the field of computer system design, can solve problems such as easy to falsify, easy to falsify in remote authentication, and unclear photos of ID cards, so as to solve the problem of survival identification and reduce the possibility of falsification. Reduce the effect of manual review
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
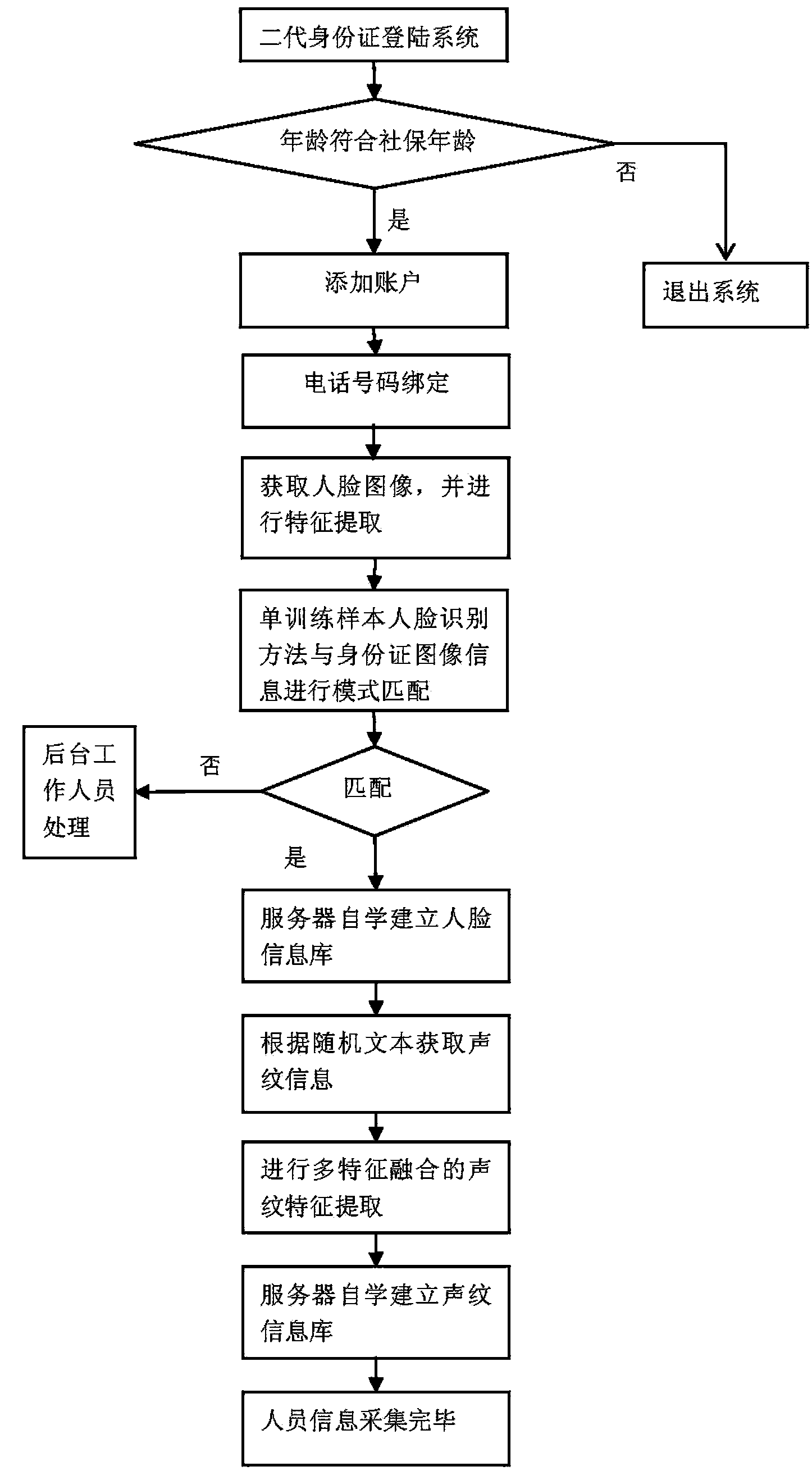
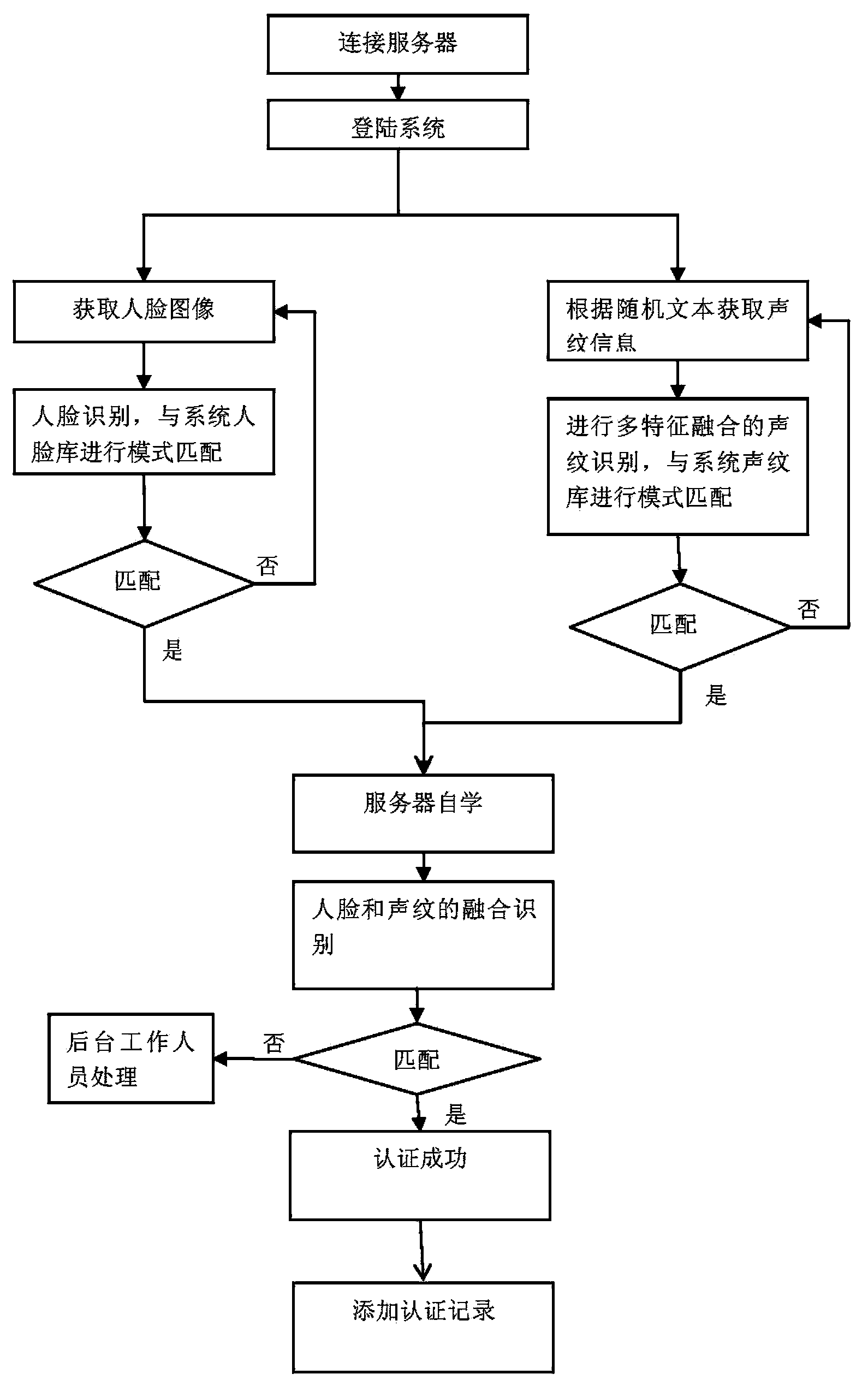
[0035] In a nutshell, improving the efficiency of personnel remote identity and survival authentication, reducing authentication costs, facilitating personnel operations, and reducing the possibility of fraud are the current direction of survival authentication.
[0036] A generalized technical solution:
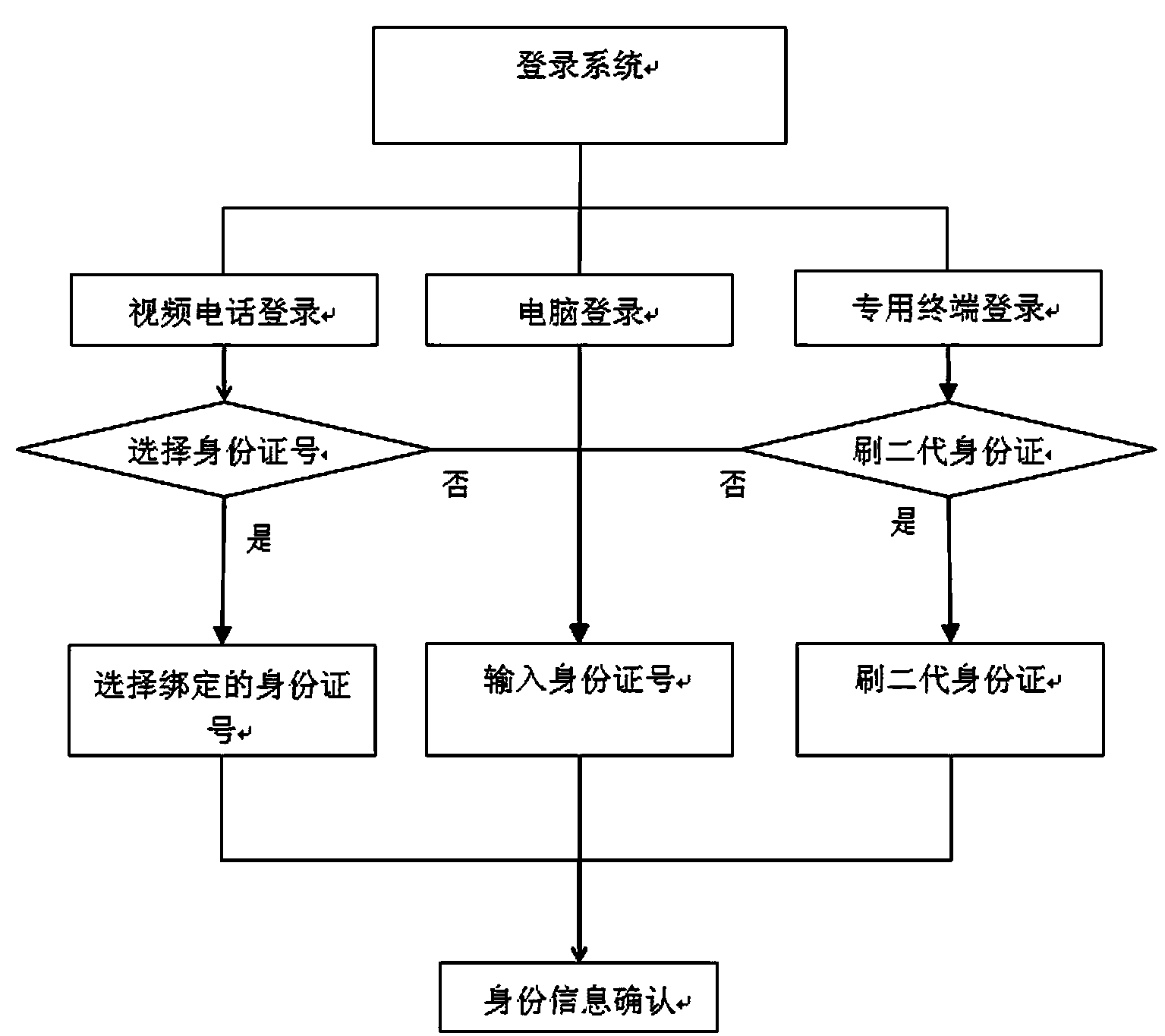
[0037] The system realized by this method should include a verification network supported by a server group, that is, remote identification is performed by the verification network, and a dedicated terminal or a common terminal is configured on the client side. Among them, special-purpose terminals should have second-generation ID card reading modules, face recognition modules, voiceprint recognition modules, network modules and storage information modules, and ordinary terminals should include network modules and face and voiceprint acquisition modules, such as videophones, personal computer, etc. All terminals are hereinafter collectively referred to as terminals.
[003...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com