A method and device for protecting an executable program
A technology for executing programs and monitoring devices, which is applied in the field of information security and can solve problems such as easy leakage of data information, and achieve the effects of increasing the difficulty of debugging and cracking, improving security, and preventing data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
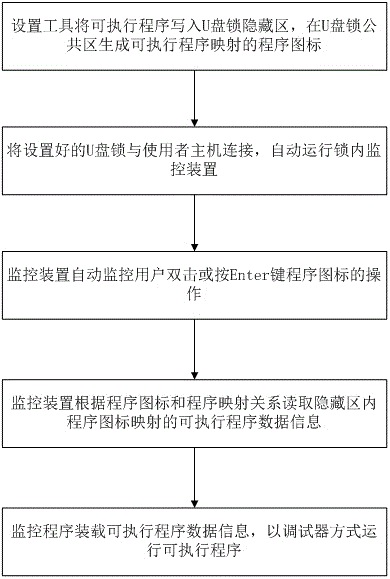
[0065] The executable program to be protected in this embodiment is a file whose suffix ends with .exe, and the storage device is a U disk dongle. According to the content of the present invention, a method for preventing copying of an executable program is provided, such as image 3 shown, where in image 3 The setting device is represented by a setting tool, and the specific steps include:
[0066] 1. Automatically write executable program information into the hidden area of the U disk encryption lock through the setting device;
[0067] 2. Generate executable program location and path mapping program icons in the U disk dongle public area;
[0068] 3. When in use, insert the set U disk dongle into the USB interface of the host, and the monitoring device inside the lock will start running automatically;
[0069] 4. The monitoring device monitors the user double-clicking or selecting the program icon and pressing the Enter key by monitoring the mouse or keyboard actions;...
Embodiment 2
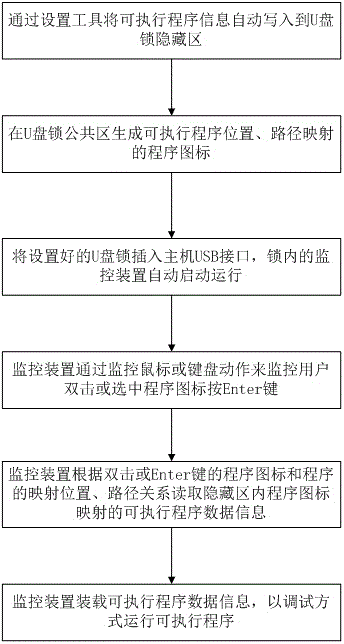
[0073] The executable program to be protected in this embodiment is a file whose suffix ends with .bat, and the storage device is a U disk dongle. According to the content of the present invention, a method for preventing copying of an executable program is provided, such as Figure 4 shown, where in Figure 4 The setting device is represented by a setting tool, and the specific steps include:
[0074] 1. Find the executable program of .bat by setting the device, and write the executable program into the hidden area of the U disk dongle;
[0075] 2. Set the device to generate a shortcut-like program icon corresponding to the executable program in the U disk dongle public area;
[0076] 3. The setting device generates a mapping table in the hidden area corresponding to the position of the executable program data content and the program icon. In the mapping table, the hidden area where the corresponding program is located can be found according to the identification informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com