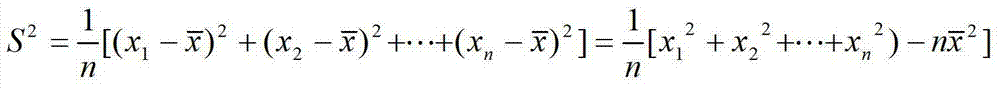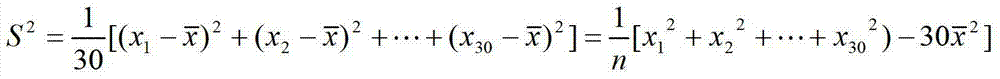Variance-based firewall abnormal log detection method
A detection method and firewall technology, applied in the information field, can solve problems such as the inability to mine abnormal behavior information and the lack of abnormal log analysis functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
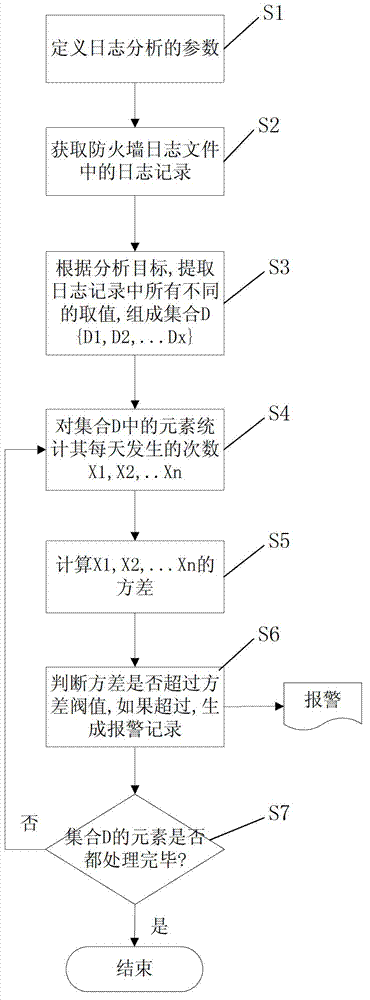
[0023] The specific implementation method of the technical solution proposed by the present invention will be described below according to the firewall logs.
[0024] Such as figure 1 As shown, the implemented method of the present invention first defines analysis parameters, step S1. For example, set the following parameters:
[0025] ●Analysis target: destination IP address
[0026] ●Time range: last thirty days
[0027] ●Variance threshold: 90
[0028] Take out the log information of the last thirty days from the firewall log, step S2. For example, the number of records in the log is 10,000.
[0029] According to the destination IP address, all different destination IP addresses are listed in the extracted 10,000 logs to form a destination IP address set, step S3. For example, in the firewall logs of the last thirty days, there are one hundred different destination IP addresses, and the set of destination IP addresses is {a 1 , a 2 , a 3 …a 100}.
[0030] Count t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com