A method, system and device for defending against cross-site request forgery (csrf) attacks
A cross-site request forgery and request packet technology, applied in the network field, can solve problems such as difficulty in defending against CSRF attacks, and achieve the effect of preventing CSRF attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
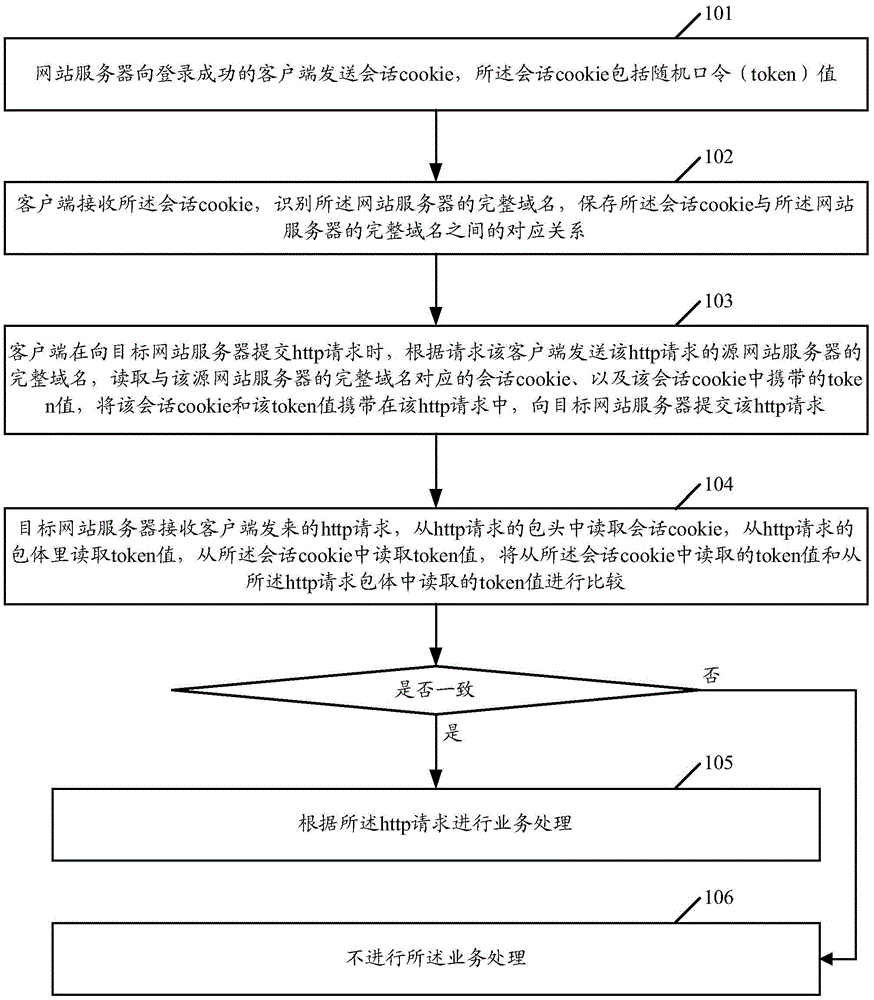
[0037] figure 1 It is a flowchart of a method for defending against CSRF attacks provided by the present invention.
[0038] Such as figure 1 As shown, the method includes:
[0039] Step 101, the website server sends a session cookie to a client that has successfully logged in, and the session cookie includes a random password (token) value.
[0040] Step 102, the client receives the session cookie, identifies the complete domain name of the website server, and saves the correspondence between the session cookie and the complete domain name of the website server.
[0041] Step 103, when the client submits an http request to the target website server, read the session cookie corresponding to the complete domain name of the source website server and the session cookie according to the complete domain name of the source website server that the client sends the http request to. The token value carried in the cookie, the session cookie and the token value are carried in the http...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com