Network segment-crossing data security exchange device and exchange method
A data security and exchange device technology, applied in the field of data exchange, can solve problems such as the inability to complete data exchange automatically and quickly, the lack of guarantee for information security exchange, and the limitation of network application capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
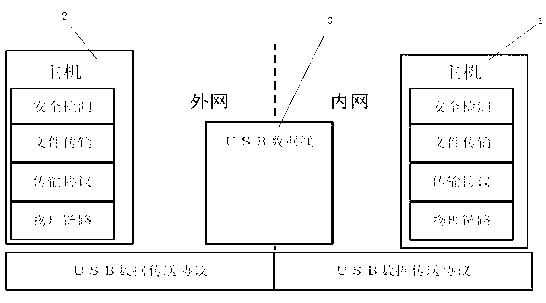
[0042] Please refer to the accompanying drawings for a further description of the present invention.
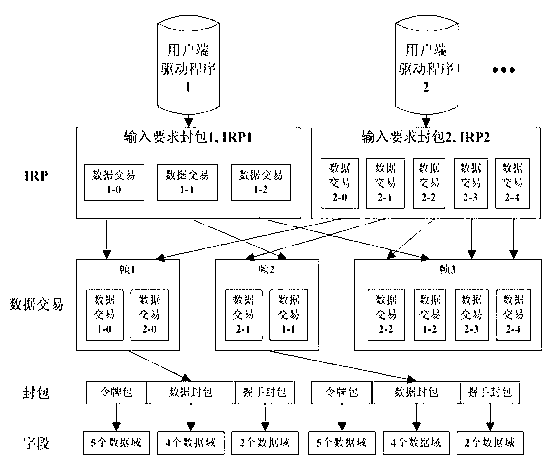
[0043] USB uses multiple peripherals to share a peripheral bus. The key is the standardization and standardization of the interface characteristics (electrical and mechanical characteristics) and transmission information between each peripheral and the host. USB adopts the serial method to transmit data, which changes the chaotic state of the connection between the host and the peripheral, unifies the interface between the peripheral and the host, simplifies the setting, and increases the number of peripherals that the host can connect to, and provides Higher transmission efficiency.
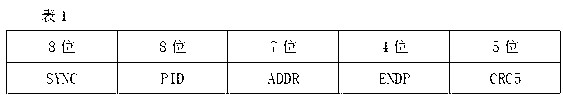
[0044] There are four types of USB transfers: Control Transfer, Interrupt Transfer, Bulk Transfer and Isochronous Transfer. Each transport mode corresponds to a specific endpoint and a specific way to achieve data transmission. The present invention adopts batch type transmission.
[0045]Bu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com