Method and system for safely controlling network resource
A network resource and security control technology, applied in the transmission system, electrical components, user identity/authority verification, etc., can solve problems such as network resource confusion, and achieve the effects of avoiding network resource confusion, clear hierarchical division, and preventing damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
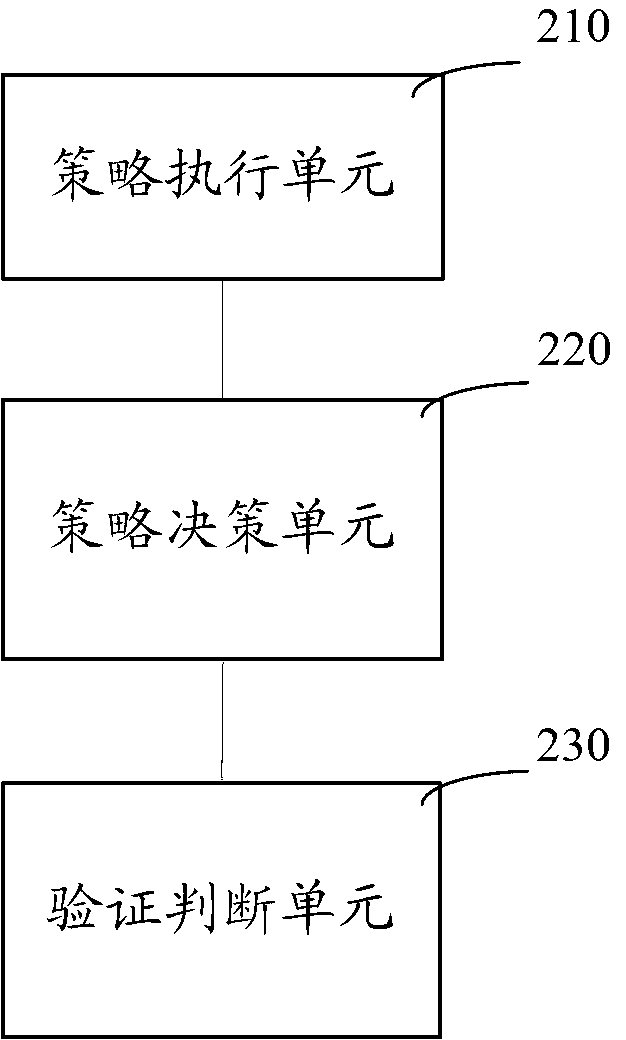
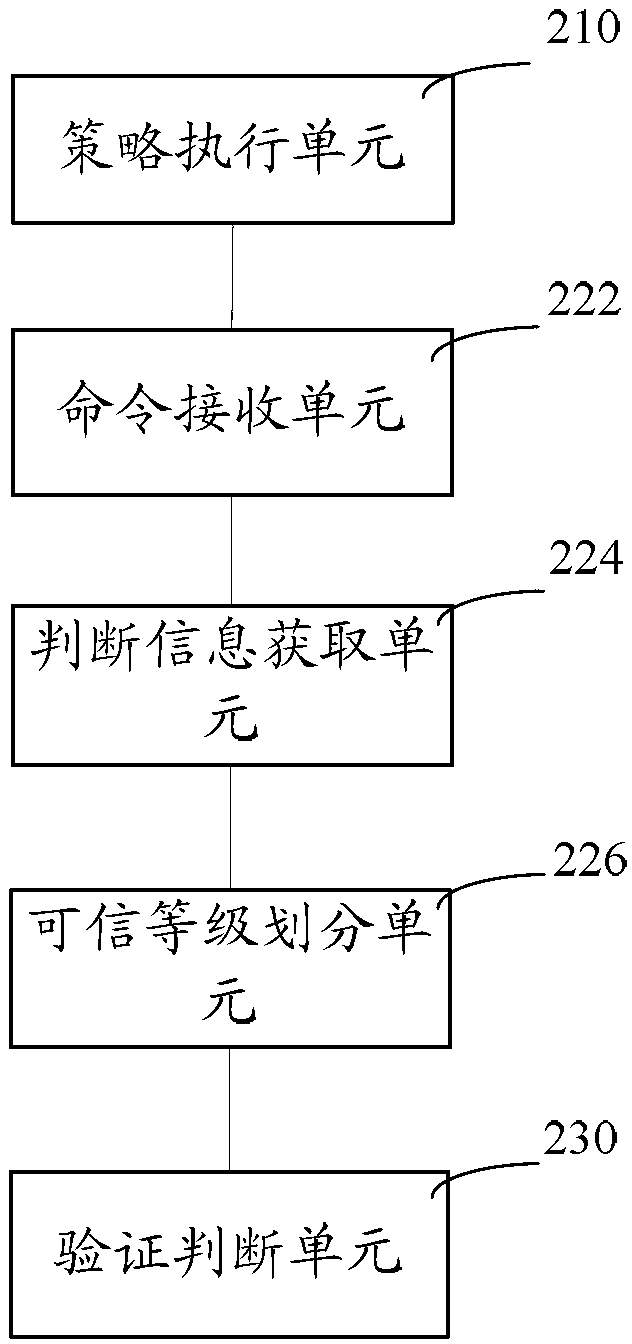
[0017] Such as figure 1 As shown, a method for network resource security control includes steps:
[0018] Step S110, collect the identity authentication information and integrity information of the access requesting end according to the access request of the access requesting end, and confirm the trust level of the access requesting end; in this embodiment, the system measures the trust level of the access requesting end In this case, IMVs (Integrity Measurement Verifiers, Integrity Measurement Verifiers) can communicate with IMCs (Intergrity Measurement Collectors, Integrity Measurement Collectors) on the access request end to collect the identity authentication information and integrity information of the access request end. Specifically, you can Including: the integrity of the trusted chain, kernel version, system version, kernel patch and signature information of firewall software and other information. The system evaluates the trust level of the access request end throug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com