Protection method and protection system of surveillance video content
A technology for monitoring video and protection systems, applied in closed-circuit television systems, components of television systems, image communications, etc., can solve problems such as video content leaks, and achieve the effect of security assurance and not easy leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
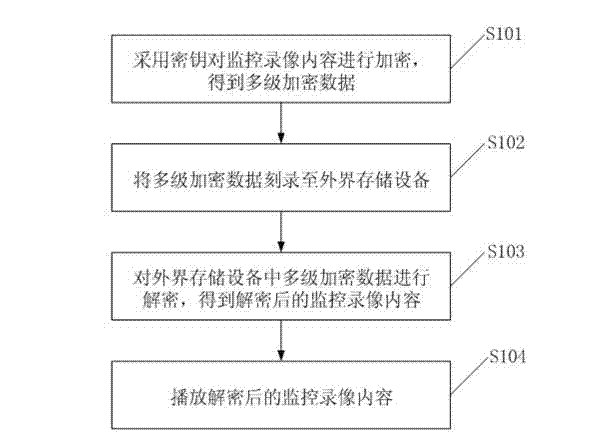
[0057] figure 1 It is a schematic flowchart of a method for protecting surveillance video content provided by Embodiment 1 of the present invention. see figure 1 , a surveillance video content protection method comprising:
[0058] S101: Using a key to encrypt the content of the surveillance video to obtain multi-level encrypted data.
[0059] S102: Burn the multi-level encrypted data to an external storage device (such as a DVD disc).
[0060] S103: Decrypt the multi-level encrypted data in the external storage device to obtain the decrypted surveillance video content.
[0061] S104: After the decryption is successful, play the decrypted surveillance video content.
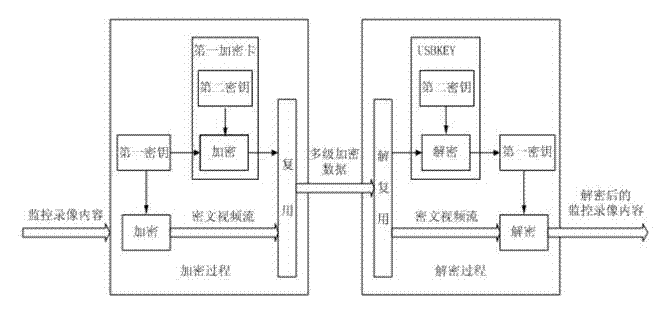
[0062] figure 2 It is a block diagram of encryption and decryption of surveillance video content provided by Embodiment 1 of the present invention.
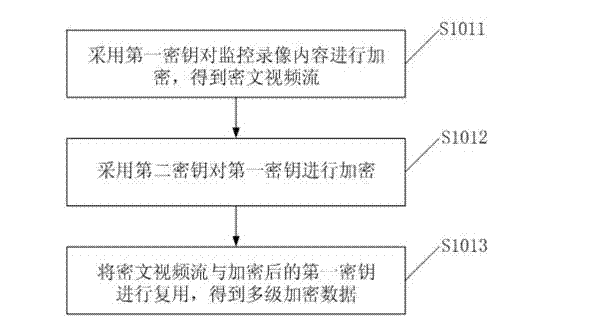
[0063] image 3 It is a schematic diagram of the encryption process of surveillance video content provided by Embodiment 1 of the present invention. combin...
Embodiment 2
[0079] Figure 5 It is a schematic diagram of a surveillance video content protection system provided in Embodiment 2 of the present invention. see Figure 5 , a monitoring video content protection system includes: a monitoring subsystem 501 , a playback subsystem 502 , and an authorization subsystem 503 .
[0080] The monitoring subsystem 501 establishes a connection with the IP camera, receives the monitoring video content collected by the camera in real time, realizes encryption, recording, and playback of the monitoring content, and burns the encrypted monitoring content to an external storage device, such as a DVD disc; wherein, The encryption process can be completed by calling the first encryption card through the encryption library, and then scrambling and multiplexing; when the monitoring subsystem 501 plays back the encrypted monitoring content, the USBKEY library calls the USBKEY to decrypt the encrypted monitoring content.
[0081] The playback subsystem 502 comp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com