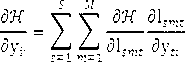Telcom phone phishing-resistant method and system based on discrimination and identification content analysis
A telecommunications phone and content analysis technology, applied in transmission systems, electrical components, wireless communications, etc., can solve the problems of inability to accurately detect fraudulent calls and easy misjudgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
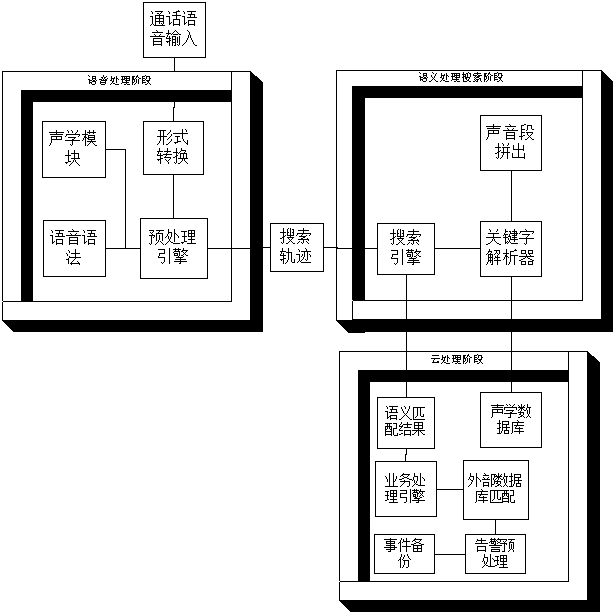
[0021] The present invention provides a method and system for preventing telecommunications and telephone fraud based on the semantic content analysis of telephone voice. Specifically, the method and system are realized by including four steps:
[0022] Step 1: In the speech processing stage, set the speech sequence input into the library, converted into parametric speech waveforms by a form converter , then the voice waveform establishment probability P(W|S) can be calculated according to the voice sample library model P(S), and then the model M can be established through P(W|S), and there is a hidden Markov process (HMM) to obtain The joint probability P(W,S|M) of , followed by parameter matching through the acoustic model and speech grammar matcher.
[0023] In the preprocessing engine, establish a suitable sound sample library, including the extraction of sound features, and use Mel-Frequency Cepstral Coefficients (MFFCC) to do cepstral analysis to extract features, in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com