Method and device of intelligent intercept
An intelligent and information communication technology, applied in the field of information processing, can solve the problems of low convenience, poor intelligent interception and interception effect, and imperfect functions, and achieve the effect of improving convenience, accurate matching results, and improving interception effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0083] This example provides a method of intelligent interception, see figure 1 , the method flow is as follows:
[0084] 101: Receive communication information, where the communication information includes at least one of incoming calls and short messages;
[0085] 102: Match the communication information with a preset interception rule, and intercept the communication information according to the matching result, wherein the preset interception rule includes intercepting incoming calls and short messages of preset numbers, and intercepting preset key At least one of the short messages is intercepted.
[0086] Preferably, before matching the communication information with the preset interception rules, it further includes:
[0087] Preprocessing communication information;
[0088] Match communication information with preset interception rules, including:
[0089] Match the preprocessed communication information with preset interception rules;
[0090] Among them, the com...
Embodiment 2
[0118] In order to explain the method provided by the above-mentioned embodiment 1 in more detail, below, in combination with the content of the above-mentioned embodiment 1, take the following embodiment 2 and embodiment 3 as examples to illustrate the method of intelligent interception, see the following embodiment 2 for details and Example Three:
[0119] Embodiment two
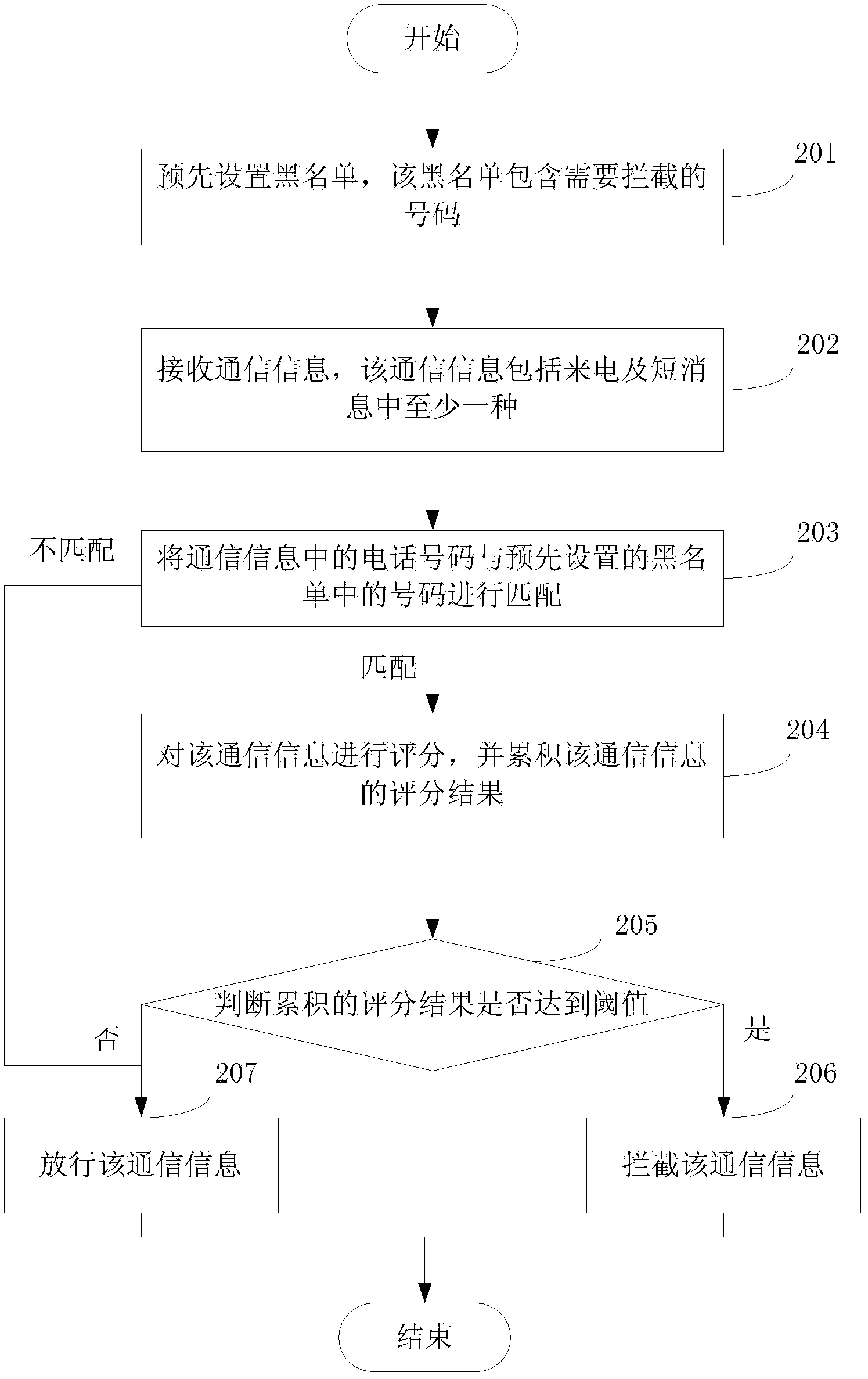
[0120] This example provides a method of intelligent interception. For the convenience of illustration, combined with the content of the first embodiment above, the preset interception rule is used as the preset blacklist containing the interception number, that is, the incoming calls and short messages of the preset number are blocked. Interception is taken as an example to illustrate the method provided in this embodiment. see figure 2 , the method flow provided by this embodiment is specifically as follows:
[0121] 201: Preset a blacklist, the blacklist contains numbers that need to be intercepted;...
Embodiment 3
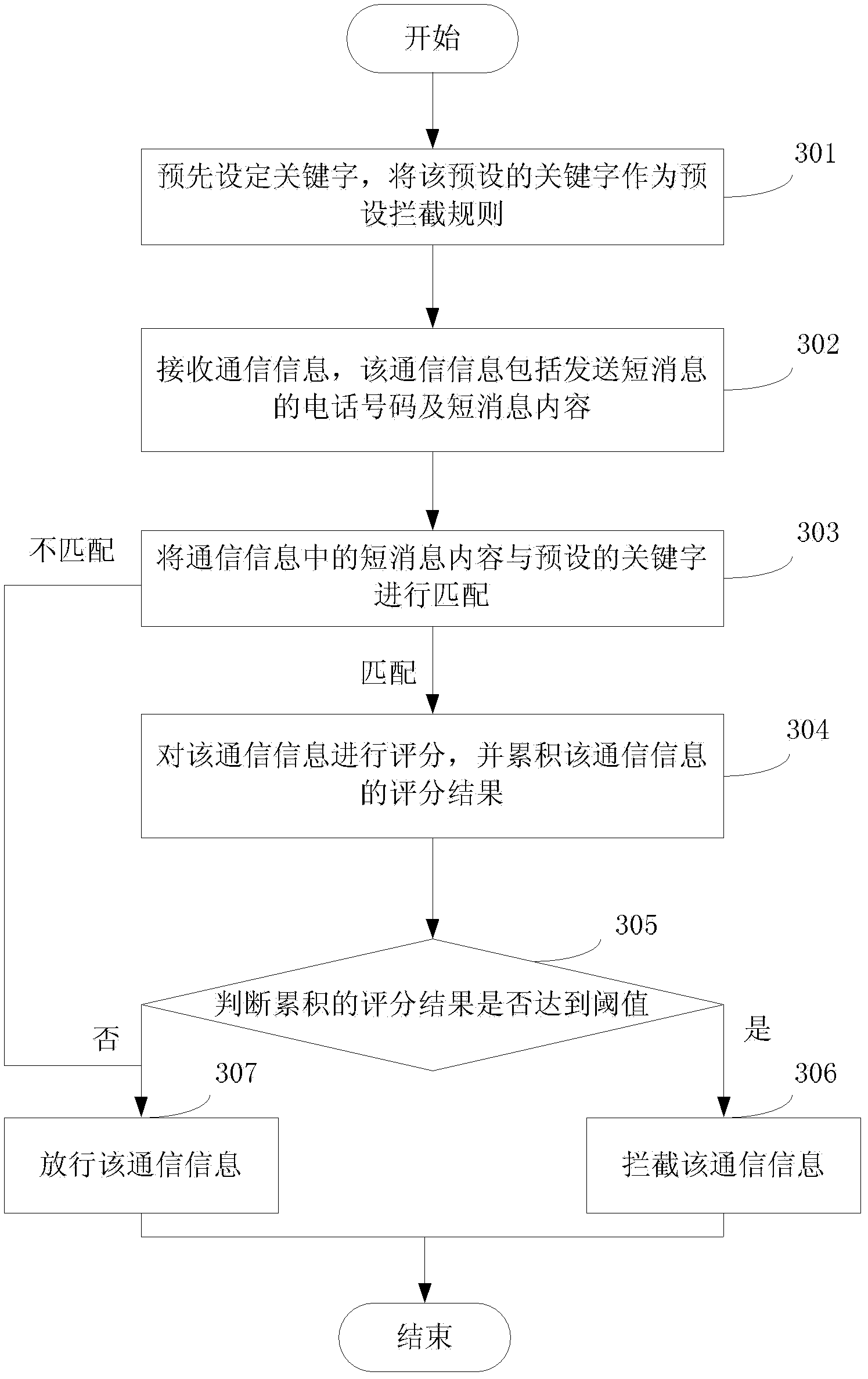
[0143] This example provides a method of intelligent interception. For the convenience of explanation, in combination with the content of the above-mentioned embodiment 1, take the preset interception rule as the preset keyword, that is, intercept the short message of the preset keyword as an example. The methods provided in the examples are illustrated. Since the preset interception rule is a preset keyword, the communication information applicable to the preset interception rule includes the phone number and content of the short message. see image 3 , the method flow provided by this embodiment is specifically as follows:
[0144] 301: preset keywords, and use the preset keywords as default blocking rules;
[0145] Specifically, this embodiment does not limit the specific content and quantity of the preset keywords. In order to filter the communication information that needs to be intercepted according to the preset keywords and avoid causing harassment to users, some wor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com