Anomaly detection method based on network flow analysis
A network traffic and anomaly detection technology, applied in the field of information security, can solve problems such as high detection complexity and unsatisfactory detection accuracy, and achieve the effect of reducing the dimensionality of traffic characteristics, improving performance, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
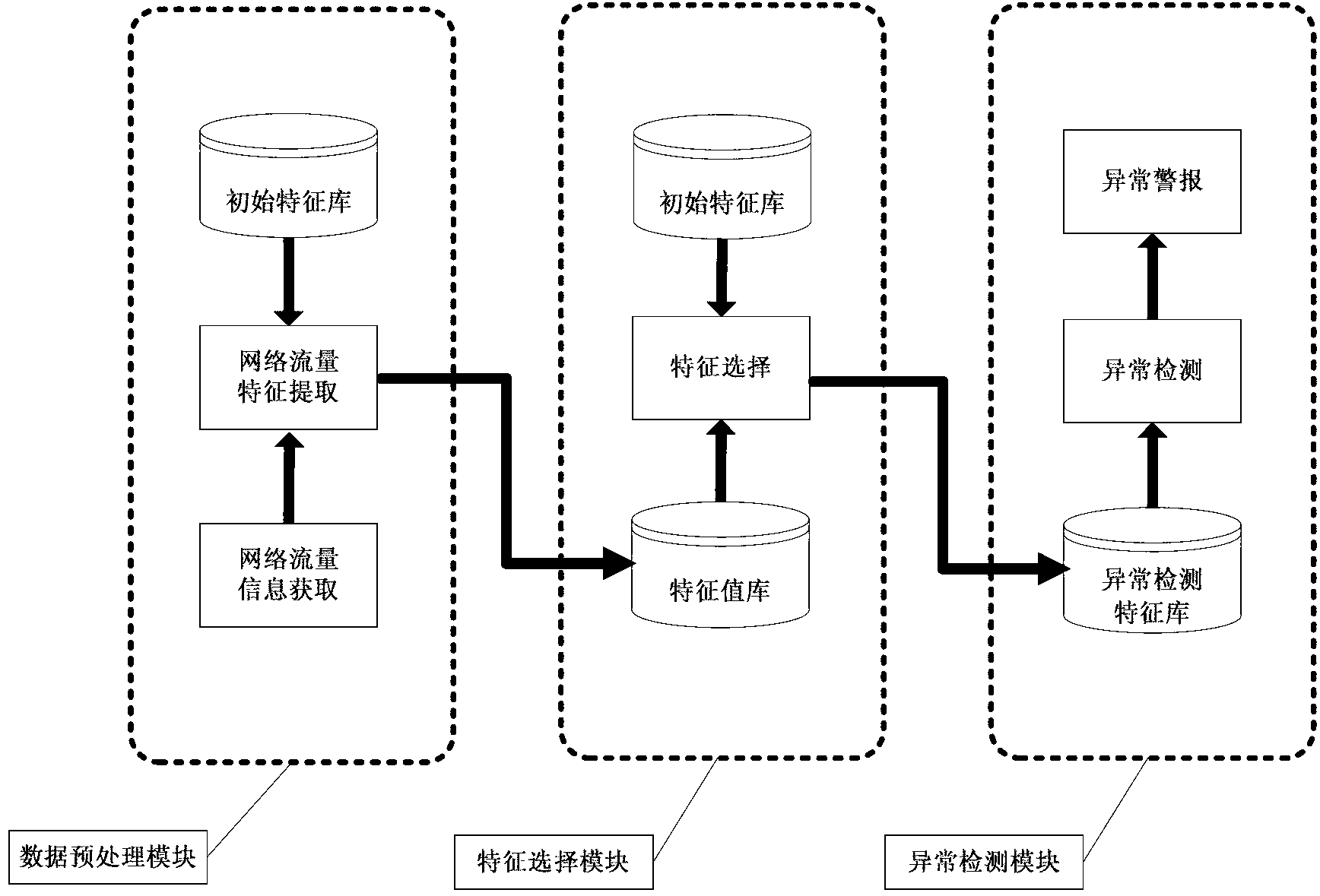
[0029] Attached below figure 1 Introduce the steps of the realization method of the present invention in detail:
[0030] See attached figure 1 , the present invention is a solution for detecting anomalies by analyzing network traffic. The detection scheme is divided into three modules: 1. data preprocessing module, 2. feature selection module, 3. anomaly detection module. The detection process is as follows:
[0031] 1) First, use the data preprocessing module to perform data preprocessing on the network traffic. Open the obtained network traffic (normal or abnormal) information file, and count the values of each initial feature in the same time interval (such as 2s) according to the traffic features in the initial feature library (110 in total, see the initial feature set table), 110 One initial eigenvalue forms a sample, and multiple samples form a sample set (normal or abnormal), and the sample set is stored in the eigenvalue library. After processing, a normal sampl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com