Method and device for synchronizing security association (SA) between equipment
A technology between devices and devices, applied in the field of communication networks, can solve problems such as waste, and achieve the effects of improving utilization, solving data flow loss, and saving bandwidth resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
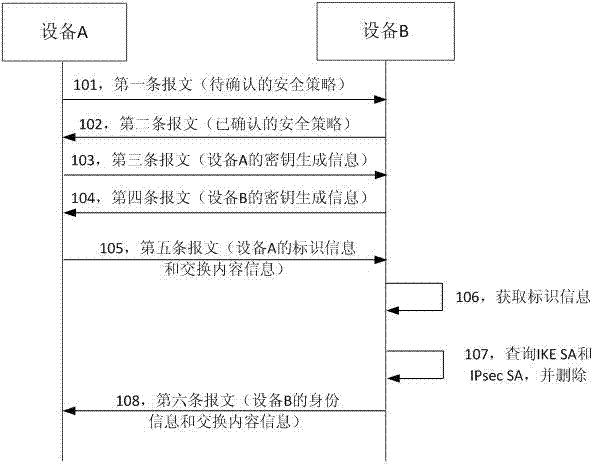
[0034] This embodiment describes the flow of the SA synchronization solution between devices in the main mode exchange mode, as figure 1 As shown, the process includes the following steps:
[0035] In step 101, network device A sends a first message to peer network device B for requesting SA parameter exchange, and the message carries an SA security policy to be confirmed.
[0036] Step 102, network device B returns a second message to network device A according to the received first message to confirm the SA security policy, and the message carries the SA security policy confirmed by network device B.
[0037] The above steps 101-102 implement the SA parameter exchange process, which is used for negotiating and confirming relevant security policies. Specifically, network device A sends the IKE policy to the peer network device B, and network device B searches for a matching policy and returns it to network device A. Network device A receives the policy confirmed by network d...
Embodiment 2
[0069] This embodiment describes the flow of the SA synchronization solution between devices in the aggressive mode exchange mode, such as image 3 As shown, the process includes the following steps:
[0070] Step 301, network device A sends a first message to network device B to request confirmation of the SA security policy and key exchange, the first message carries the SA security policy to be confirmed and key generation information of device A .
[0071] Step 302, IPsec SA peer B returns a second message to network device A according to the received first message, and the second message carries the SA security policy confirmed by network device B and network device B's key generation information.
[0072] The above steps 301-302 implement the security policy and key exchange process, which are used for security policy negotiation and exchange of Diffie-Hellman public value and auxiliary data.
[0073] Step 303, network device A sends a third message to network device ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com