Computing device identifying method and device
A computing device and identification technology, applied in the computer field to achieve the effect of accurately identifying computing devices and ensuring stability and uniqueness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
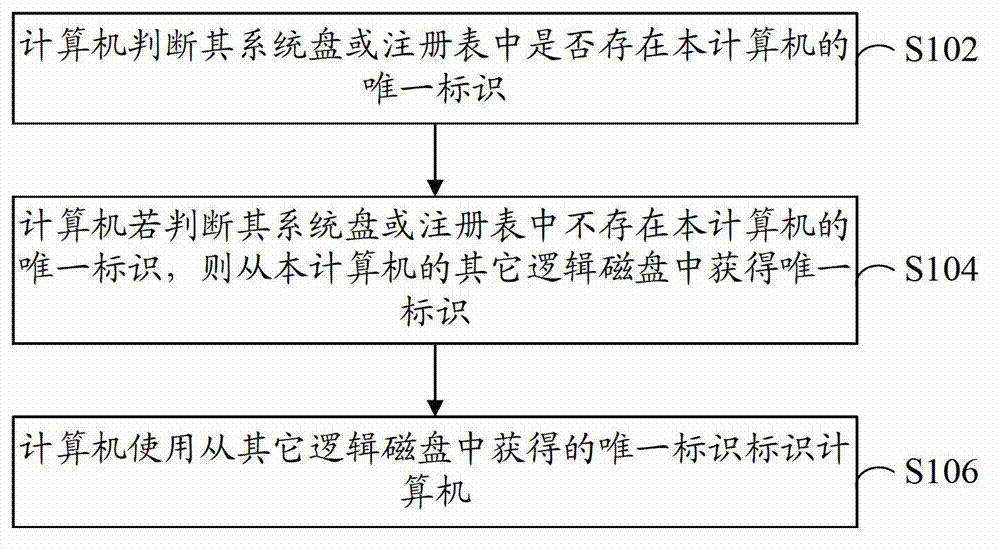
[0035] refer to figure 1 , shows a flow chart of steps of a method for identifying a computing device according to Embodiment 1 of the present invention.
[0036] The computing device identification method in this embodiment includes the following steps:
[0037] Step S102: The computer judges whether the unique identifier of the computer exists in its system disk or registry.
[0038] Wherein, the unique identifier of the computer is obtained by calculating the identifier calculation parameters, and the identifier calculation parameters include at least one of the following computer name, GUID (Globally Unique Identifier), and remaining disk size of the system disk. In addition to the above, the identification calculation parameters may also include random numbers.
[0039] Initially, the unique identifier of the computer exists in the registry, system disk and other logical disks of the computer. When something happens, such as after the system is reinstalled, the unique ...
Embodiment 2
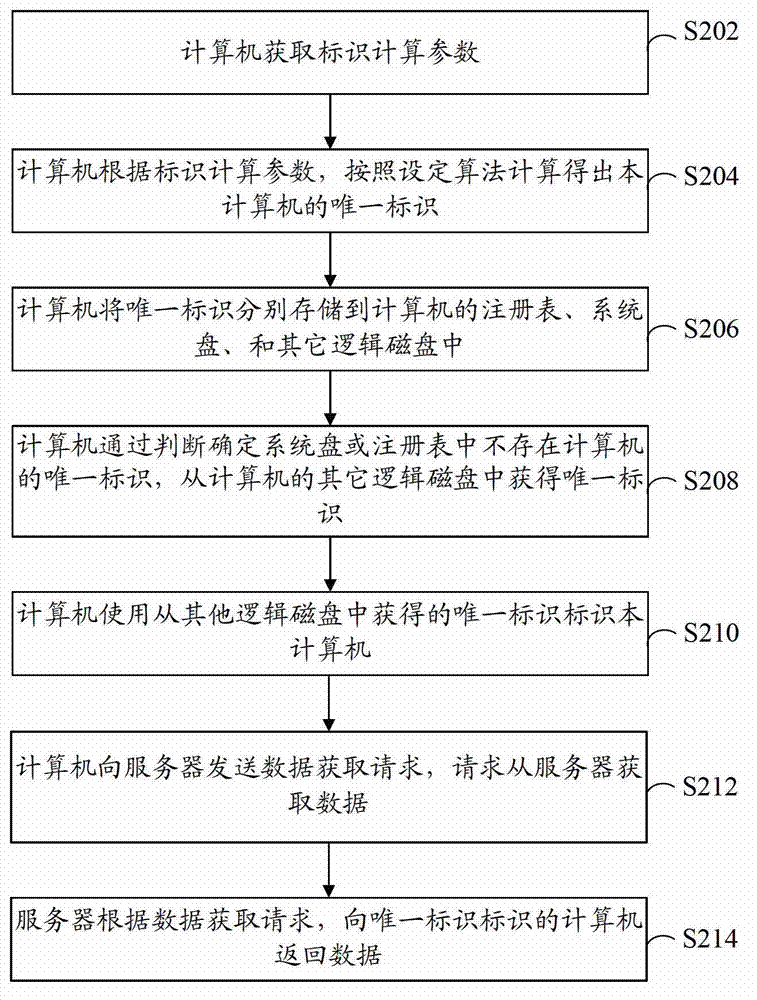
[0046] refer to figure 2 , shows a flow chart of steps of a method for identifying a computing device according to Embodiment 2 of the present invention.
[0047] The computing device identification method in this embodiment includes the following steps:
[0048] Step S202: The computer obtains the identification calculation parameters.
[0049] In this embodiment, the identification calculation parameters include one or more of computer name, GUID, remaining disk size of the system disk of the computer, and may also include random numbers and the like.
[0050] Step S204: The computer calculates the unique identifier of the computer according to the set algorithm according to the identifier calculation parameters.
[0051] For example, by combining the identification calculation parameters and random values, a unique identification is calculated according to the set algorithm, so that the possible repetition rate of the identification is extremely low.
[0052] Preferably...
Embodiment 3
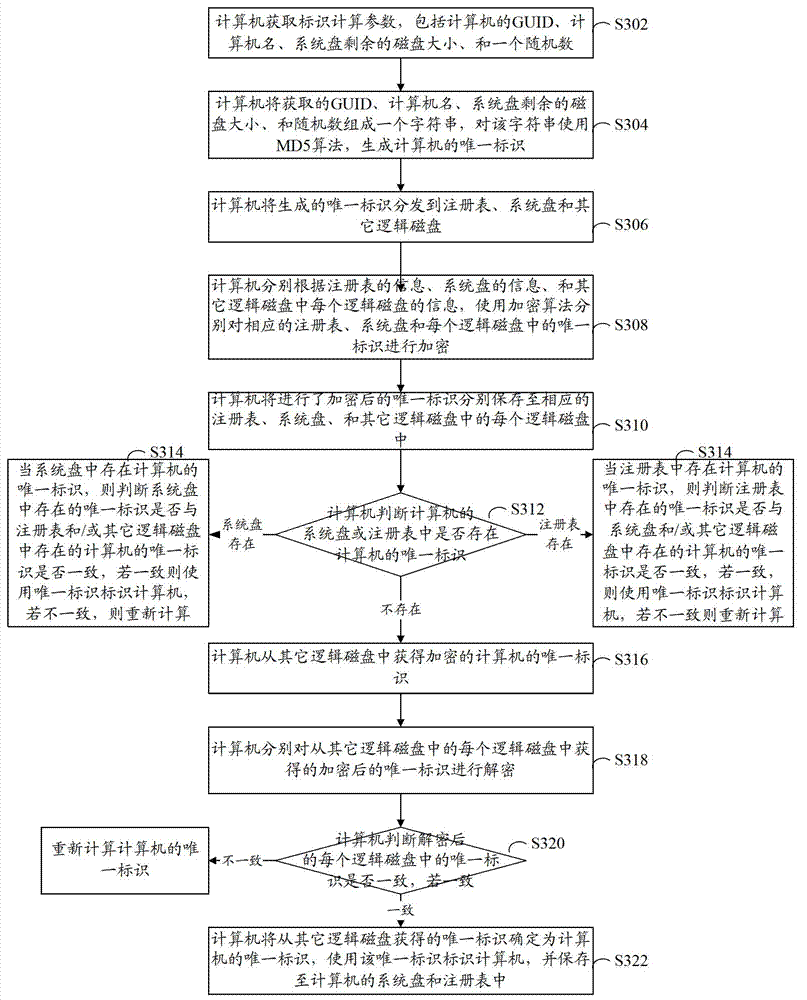
[0070] refer to image 3 , shows a flow chart of steps of a method for identifying a computing device according to Embodiment 3 of the present invention.
[0071] The computing device identification method in this embodiment includes the following steps:
[0072] Step S302: The computer acquires identification calculation parameters, including computer GUID, computer name, remaining disk size of the system disk, and a random number (pseudo-random number calculated by the computer).
[0073] Step S304: The computer forms a character string with the obtained GUID, computer name, remaining disk size of the system disk, and random numbers, and uses the MD5 algorithm on the character string to generate a unique identifier of the computer.
[0074] Step S306: The computer distributes the generated unique identifier to the registry, system disk and other logical disks.
[0075]Step S308: According to the information of the registry, the information of the system disk, and the infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com