Method and system for preventing computer virus from frequently infecting systems
A computer virus and repeated infection technology, applied in the field of computer defense, can solve the problems of server business interruption, difficult to clear, and the effectiveness of the clearing strategy is poor, and achieves the effect of ensuring security and eliminating the harm of viruses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
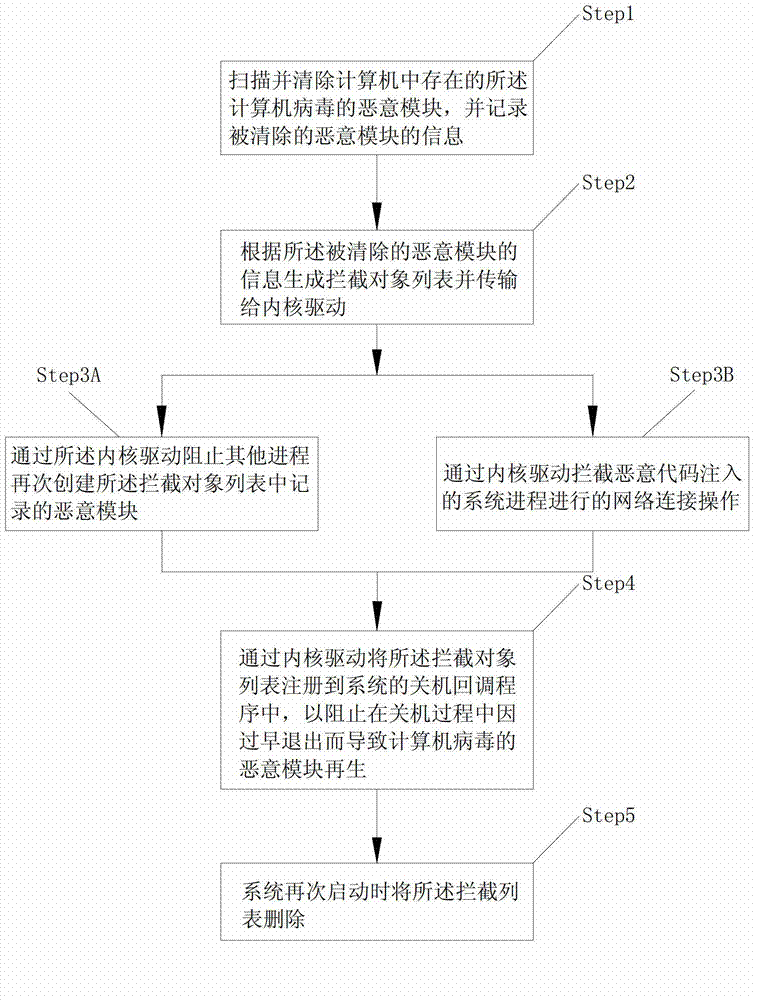
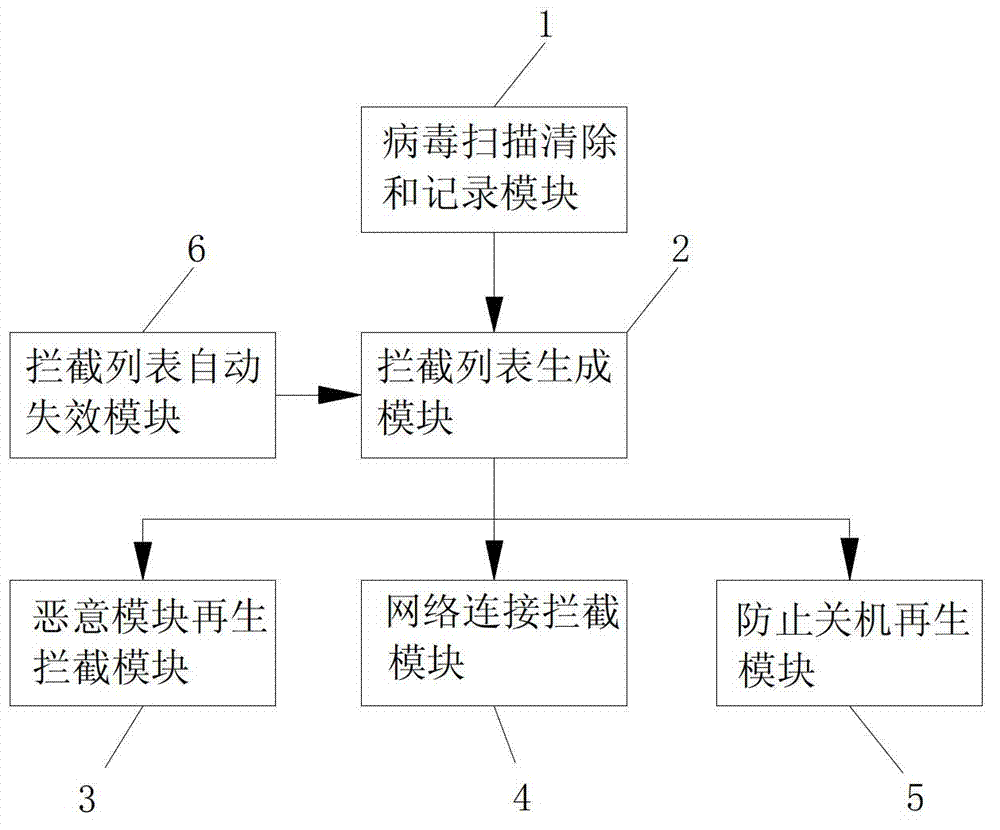
[0039] Such as figure 1 As shown, this embodiment discloses a method for preventing computer viruses from repeatedly infecting a system, comprising the following steps:
[0040] Step1: Scan and remove the malicious module of the computer virus that exists in the computer, and record the information of the removed malicious module; the malicious module includes files, registry, and processes, and the information of the removed malicious module is recorded , specifically: record the complete file path name corresponding to the file; record the path (key) and key value (Value) of the registry; and record the complete file path name of the file corresponding to the process. The specific scanning and removal methods can adopt many existing conventional methods, such as setting up a virus database, scanning all files, registration lists, and processes in the system, and if they are in it, it will be removed. For example: the malicious module corresponding to the computer virus is t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com