Software running security measurement and estimation method based on network environment
A software security and network environment technology, applied in the field of network information security analysis and evaluation, can solve problems such as poor pertinence, lack of test basis, lack of test basis, etc., and achieve the effect of good scalability, flexible evaluation method and objective evaluation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
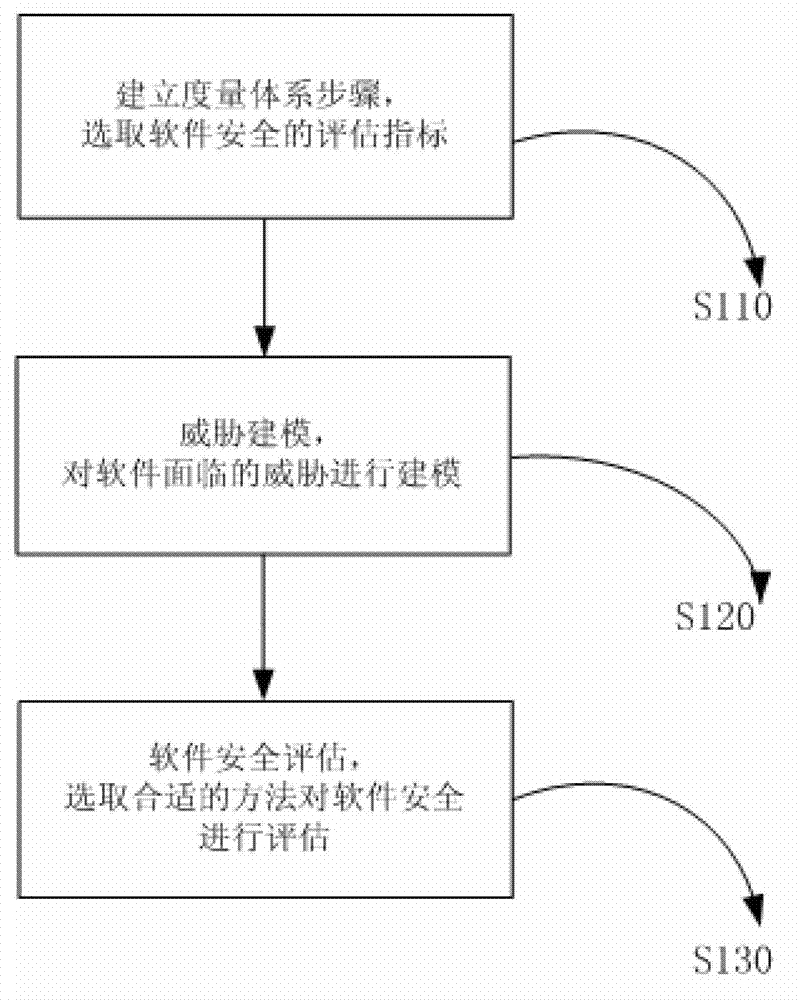
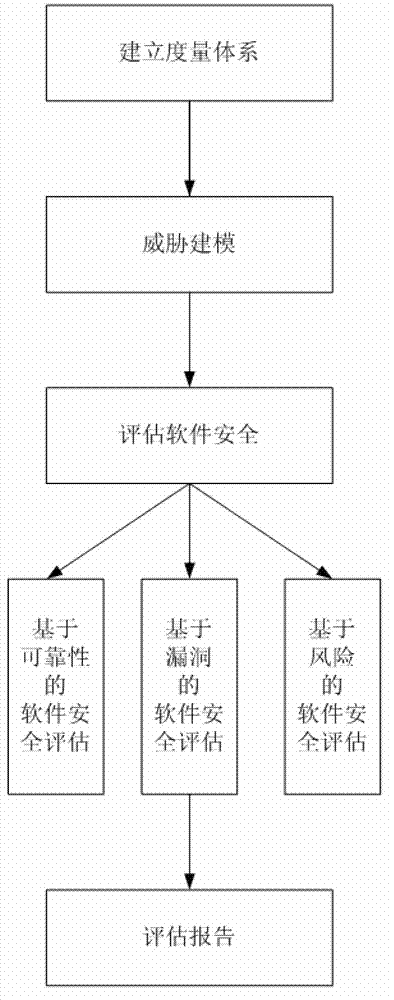
[0023] refer to figure 1 , figure 1 It is a flow chart of the steps of the software security evaluation embodiment in the network environment of the present invention, including the following steps: step S110 of establishing a measurement system, selecting software security evaluation indicators; threat modeling step S120, modeling the threats faced by the software in the network environment ; Software security assessment step S130, based on the assessment indicators, use the reliability-based software security assessment method, the vulnerability-based software security assessment method and the risk-based software security assessment method to perform security assessment on software facing threats in the network environment . ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com