A method for remote identification or anti-counterfeiting of a mobile phone with NFC function
A feature phone and identity technology, which is applied in the field of commodity identity identification and anti-counterfeiting applications, can solve the problems of inability to perform anti-counterfeiting identification, remember phone numbers, and waste resources, so as to improve reliability, security, and convenience And practicality, the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
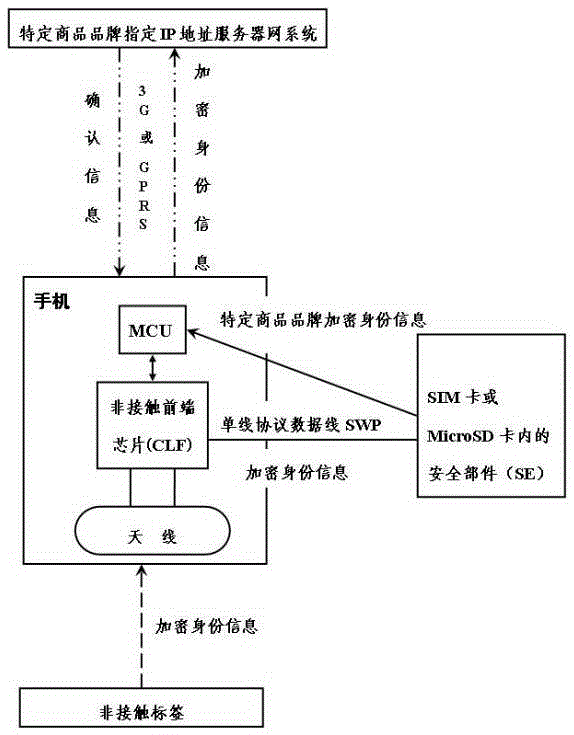
[0068] The security component (SE) placed in the SIM card is connected to the non-contact front-end circuit (CLF) in the mobile phone via the single-wire protocol (SWP) data line as an example of an NFC mobile phone (see attached figure 2 ).
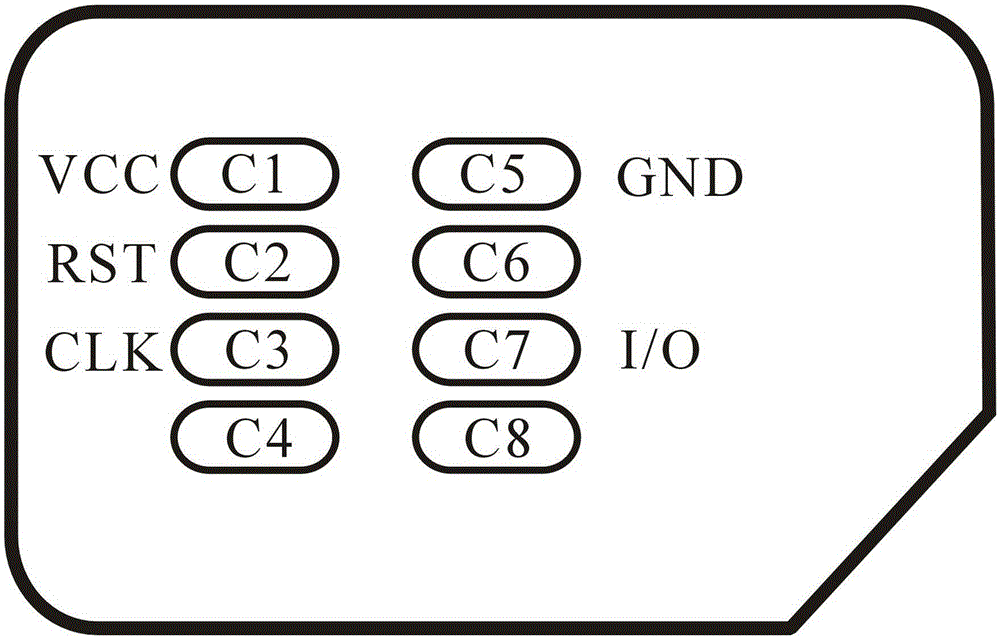
[0069] The security component (SE) placed in the SIM card is connected to the non-contact front-end circuit (CLF) in the mobile phone through the single-wire protocol (SWP) data line. The NFC mobile phone means that the mobile phone integrates the non-contact front-end circuit (CLF) and antenna, which will be safe The components are integrated into the SIM card, and pin C6 of the contact feet of the SIM card (see attached image 3 ) Is made as a single-wire protocol (SWP) data communication pin SWIO.
[0070] The security component (SE) placed in the SIM card is connected to the non-contact front-end circuit (CLF) in the mobile phone through the single-wire protocol (SWP) data line. The method for remote identification or anti-counterfeiting ...
Embodiment 2
[0109] Take the security component (SE) placed in the MicroSD card connected to the non-contact front-end circuit (CLF) in the mobile phone via the single-wire protocol (SWP) data line as an example (see attached figure 2 ).
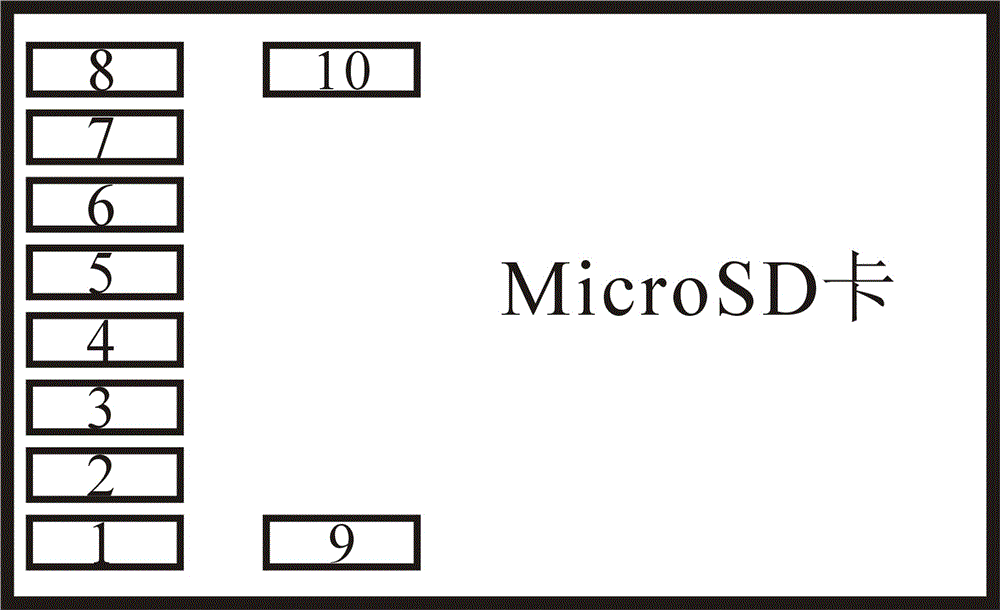
[0110] The security component (SE) placed in the MicroSD card is connected to the non-contact front-end circuit (CLF) in the mobile phone through the single-wire protocol (SWP) data line. The NFC mobile phone means that the mobile phone integrates the non-contact front-end circuit (CLF) and antenna, which will be safe The components are integrated into the MicroSD card, and the 9th and 10th pins are added to the 8 pins of the MicroSD card (see attached Figure 4 ), where the 9th pin is made as the single-wire protocol (SWP) data communication pin SWIO, and the 10th pin is the supply voltage pin SEVCC from the non-contact front-end circuit (CLF) of the mobile phone.
[0111] The security component (SE) placed in the MicroSD card is connected to the non-contact...
Embodiment 3
[0151] Take a mobile phone with an NFC-enabled MicroSD card as an example (see attached Figure 5 ).
[0152] A MicroSD card with NFC function refers to a MicroSD card integrated with a non-contact chip and a security component (SE); a mobile phone with an NFC-enabled MicroSD card has NFC function.
[0153] The following are the methods for remote identification or anti-counterfeiting of mobile phones with NFC-enabled MicroSD cards:
[0154] A method for automatically connecting to a server with a designated IP address for a specific commodity includes the following steps:
[0155] 1. The microprocessor (MCU) of the mobile phone initializes the MicroSD card with NFC function;
[0156] 2. Enter the mobile phone identification menu to activate the identification function;
[0157] 3. The microprocessor (MCU) of the mobile phone sends an identification request command to the non-contact front-end circuit (CLF) in the MicroSD card with NFC function through the MicroSD card interface;
[0158]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com