Detection method and device of website security
A technology for security detection and security detection data, applied in the field of website security detection methods and devices, can solve problems such as inability to detect and evaluate website security status, and achieve the effect of ensuring website security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0017] refer to figure 1 , shows a flow chart of steps of a website security detection method according to Embodiment 1 of the present application.
[0018] The website security detection method of the present embodiment comprises the following steps:
[0019] Step S102: Obtain the website security detection data of the website through the data access interface.
[0020] Wherein, the website security detection data includes at least one of the following: Trojan data, false fraud data, search shielding data, margin data, tampering data, and vulnerability data.
[0021] These website security testing data can explain the security status of the website from different aspects, and the collection of multiple website security testing data can reflect the overall security status of the website more comprehensively. The collected data may be stored in one or more databases, or may be stored in a suitable form in a suitable device.
[0022] The data access interface is an applicatio...
Embodiment 2
[0033] refer to figure 2 , shows a flow chart of steps of a website security detection method according to Embodiment 2 of the present application.
[0034] The website security detection method of the present embodiment comprises the following steps:
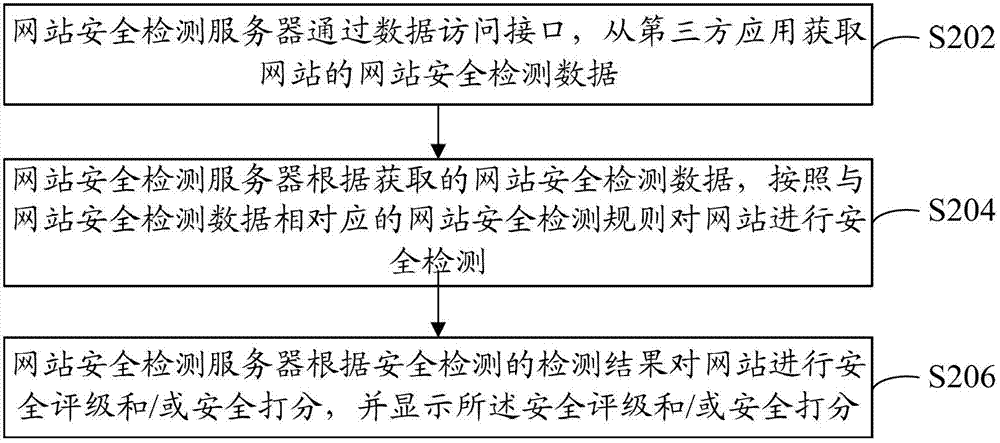
[0035] Step S202: The website security detection server acquires website security detection data of the website from a third-party application through the data access interface.
[0036] The website security detection server is provided with functional modules for implementing website security detection. In this embodiment, the functions implemented by the website security detection server can be regarded as the functions realized by the website security detection function module.
[0037] The third-party application can be an application that collects different types of security detection data of the website. The third-party application usually provides external data access interfaces, for example, vulnerability detection ac...
Embodiment 3
[0058] refer to image 3 , shows a flow chart of steps of a website security detection method according to Embodiment 3 of the present application.
[0059] In this embodiment, the website security detection method of this embodiment is described by taking the 360 website security detection server as an example. Among them, the initial security score of the website is set to 100 points.
[0060] The website security detection method of the present embodiment comprises the following steps:
[0061] Step S302: The 360 website security detection server obtains the website security detection data of the website to be detected.
[0062] In this embodiment, the acquired security detection data of the website to be detected includes: Trojan data, false fraud data, search shielding data, marginalia data, tampering data, and vulnerability data.
[0063] Specifically, when performing overall security detection on a website to be detected, this step includes:
[0064] Step A: Obt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com