Method and apparatus for identifying and verifying RFID privacy protection
A privacy protection and verification method technology, which is applied in the direction of cooperative devices, instruments, electrical components, etc., can solve problems such as easy tracking of tags, asynchronous updates of database and tags, hidden dangers of privacy leakage, etc., to achieve defense or reduce security threats Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the accompanying drawings.
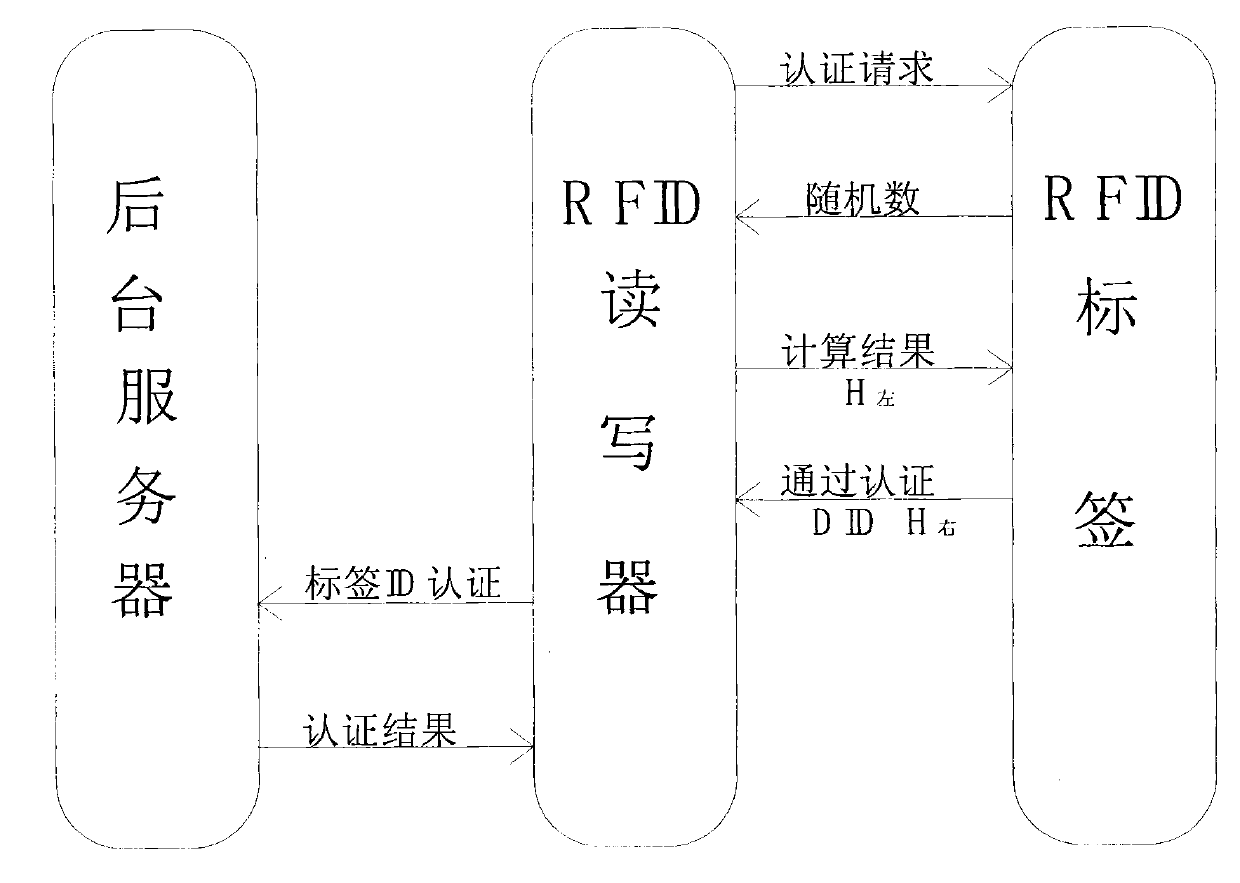
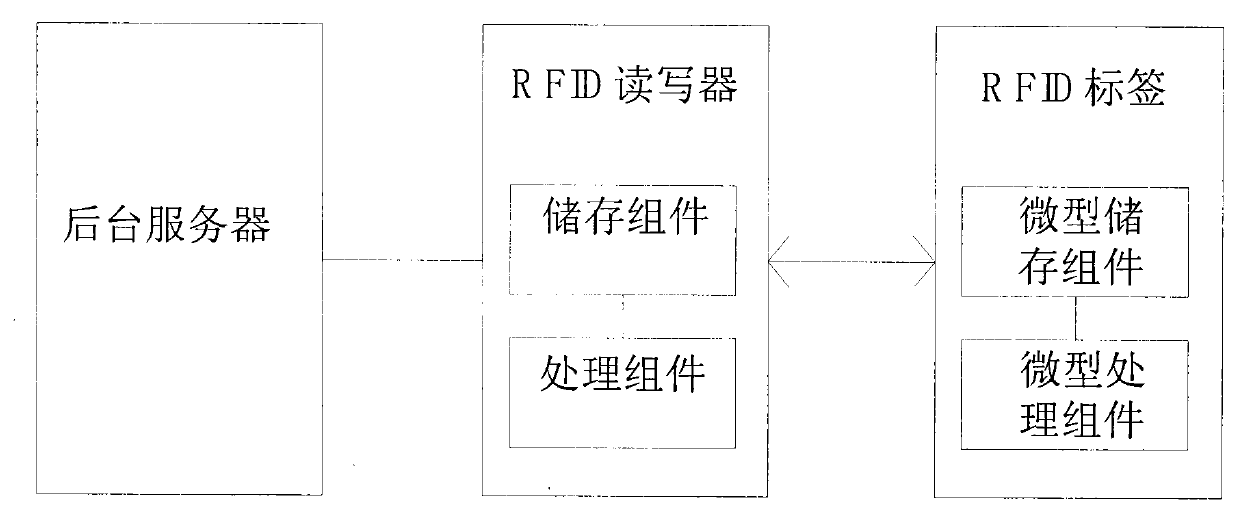
[0027] figure 1 It is a flow chart of the method of the present invention. The present invention realizes defense against illegal reader-writer scanning and illegal location tracking attacks through RFID tag and RFID reader-writer two-way authentication, and introduces hash function H(x) in RFID tag and RFID reader-writer authentication AND XOR Introduce a pseudo-random number generation module and a one-way hash function module in the RFID tag, introduce a pseudo-random number generation module and a function module in the RFID reader, and store the ID number of the RFID tag in the background server, in the RFID tag and the RFID reader The shared ciphertext Kr is also stored. First, the RFID tag authenticates the legitimacy of the RFID reader, and then the RFID reader and the background server verify the legitimacy of the RFID tag successively.
[0028] The identif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com