Web service security analysis method based on program slicing technique
A technology of program slicing and web services, which is applied in the field of web service security, can solve problems such as validity limitations, and achieve the effect of improving comprehensiveness and reducing the probability of missed detection and false detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
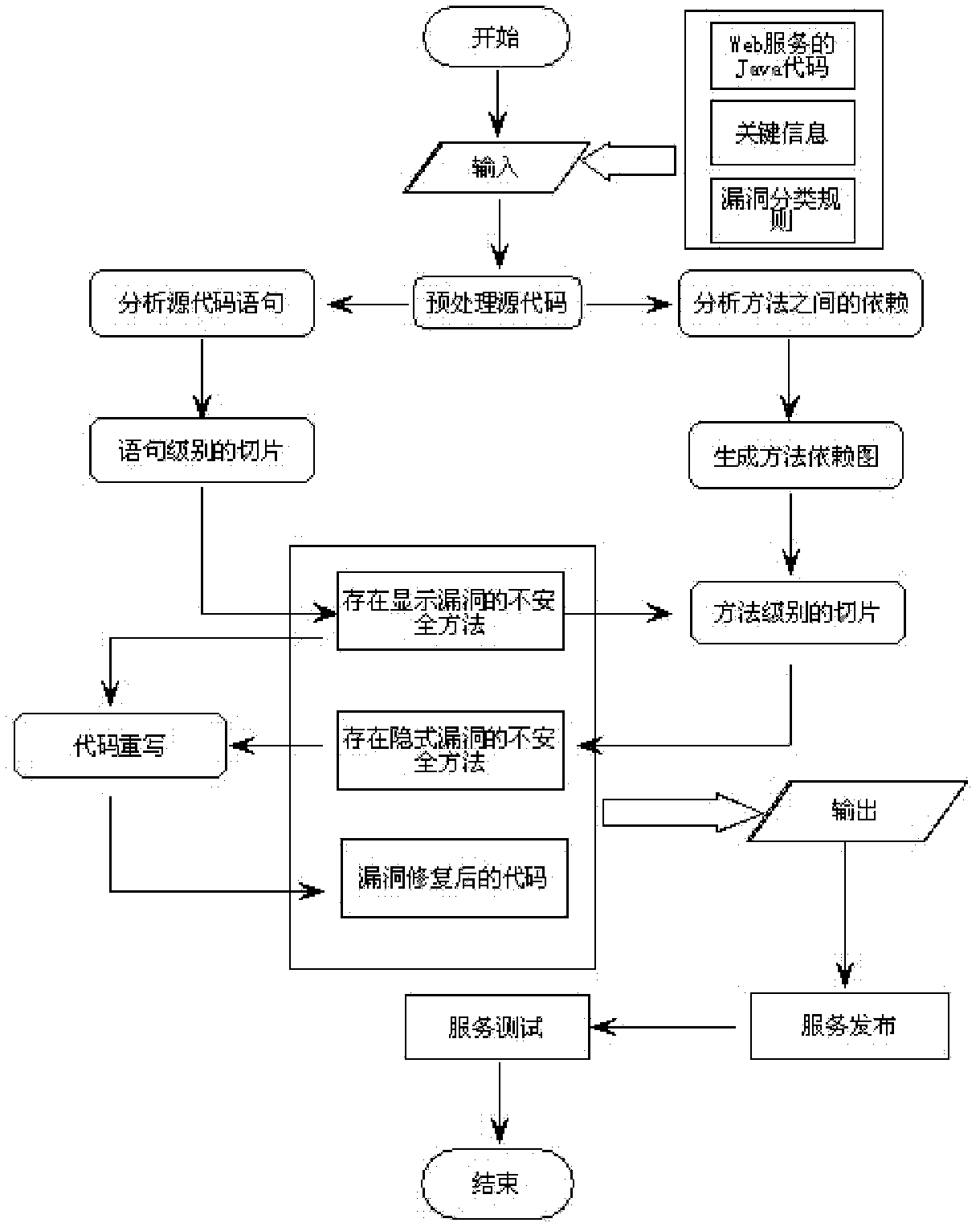
[0047] The Web service safety analysis method in the present invention includes a vulnerability classification module, a code analysis module, a slicing module, a vulnerability repair module, a service publishing module and a service testing module. figure 1 An overall flow framework of the platform of the present invention is given, and the work flow of each module is described. The following content is a detailed description of the implementation of each module in the present invention.
[0048] 1. Vulnerability classification module
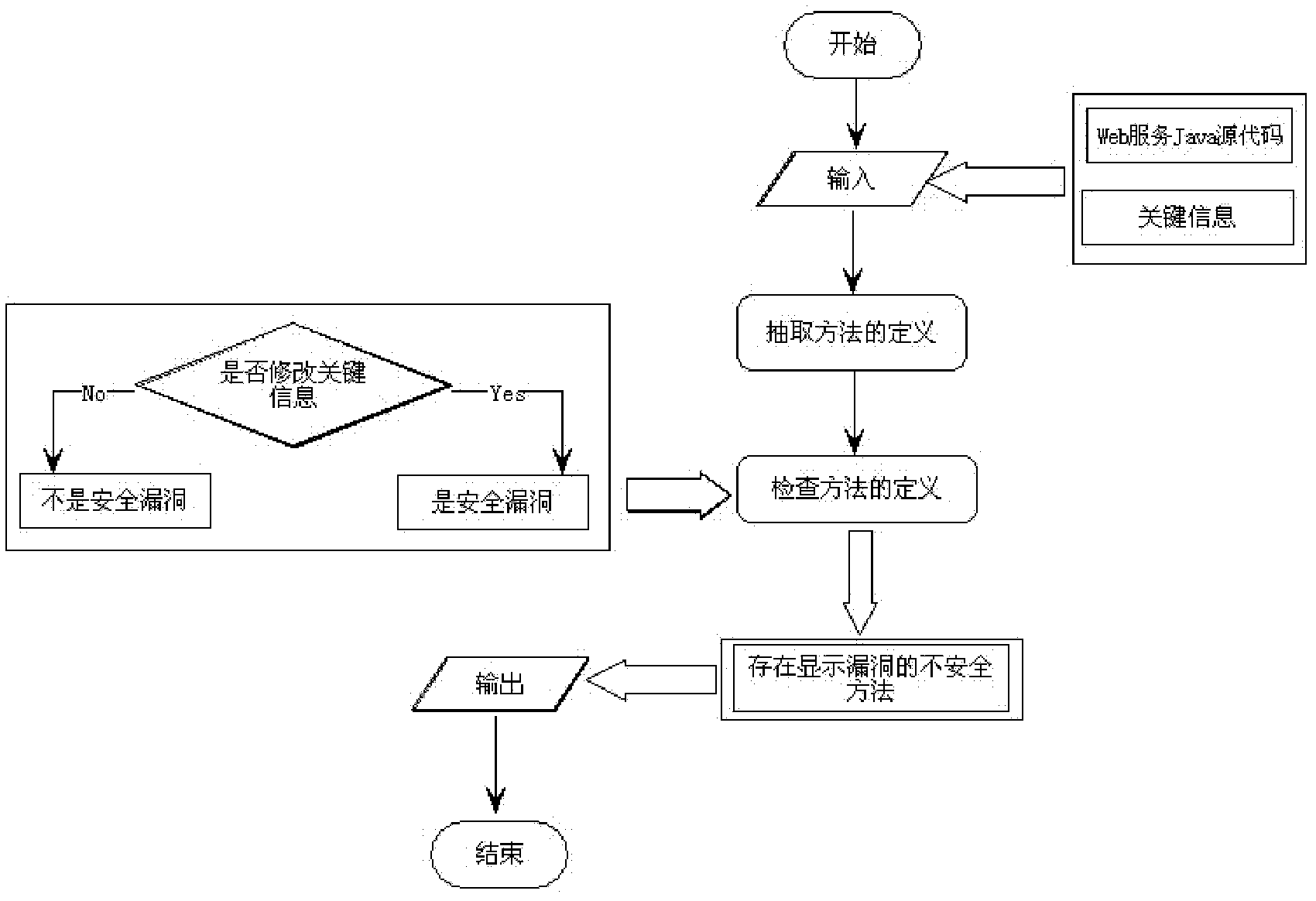
[0049] In the source code of the Web service, there are more or less private variables related to the storage service. If these variables are modified maliciously, some serious consequences may be caused. Therefore, in addition to the developer or manager of the Web service, Other personnel are not authorized to modify these variables. In the present invention, we refer to these variables as key information. There may be many methods in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com