Two-dimensional code encryption/decryption method and anti-counterfeiting method
An encryption method and two-dimensional code technology, applied in user identity/authority verification, record carriers used by machines, instruments, etc., can solve problems such as poor security, achieve security, ensure non-repetition, and improve anti-counterfeiting performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
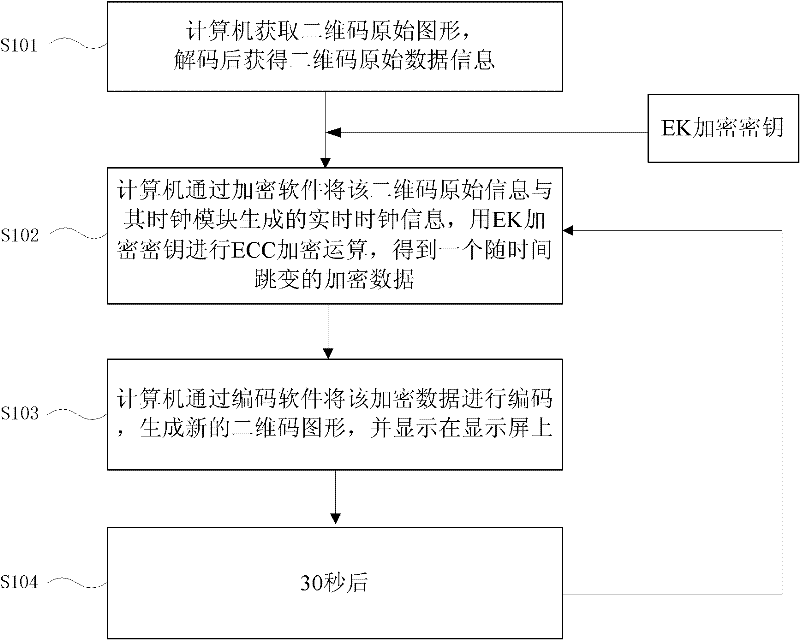
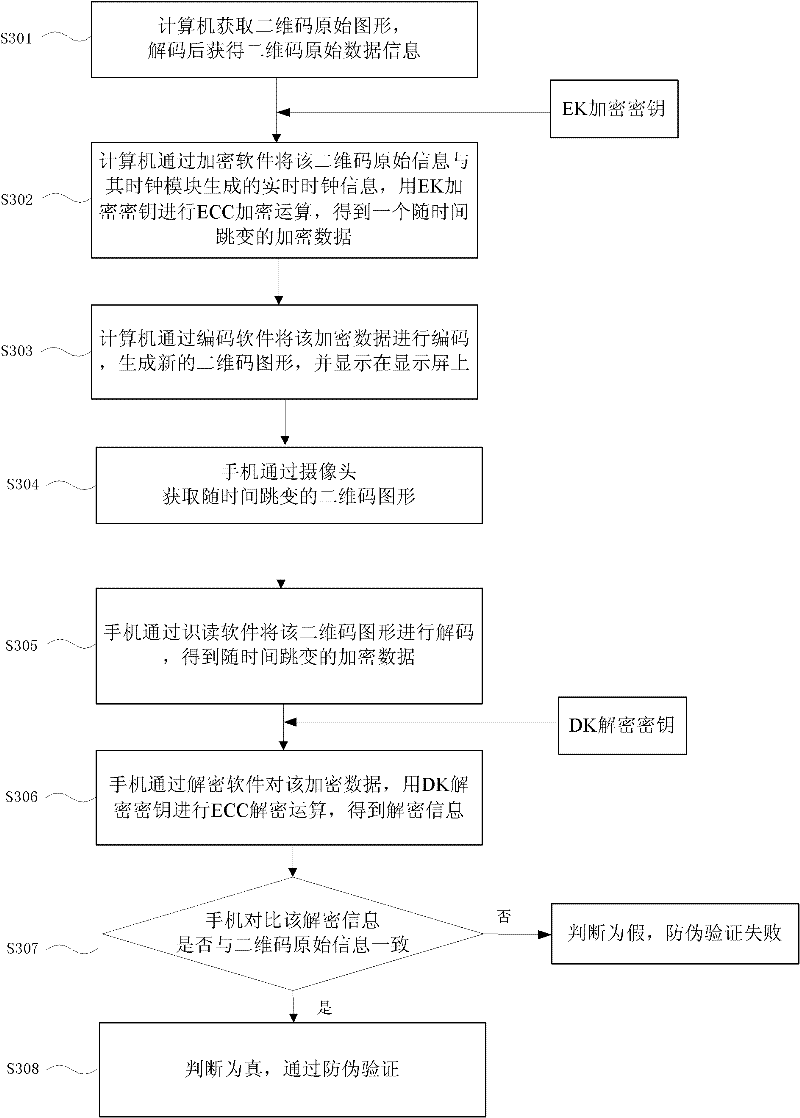
[0036] see figure 1 , the encryption method of QR code includes:
[0037] Step S101, the computer obtains the original graphic of the two-dimensional code, and obtains the original data information of the two-dimensional code after decoding;
[0038] Step S102, the computer uses the encryption software to perform the ECC encryption operation on the original information of the two-dimensional code and the real-time clock information generated by the clock module with the EK encryption key to obtain an encrypted data that changes with time;
[0039] Step S103, the computer encodes the encrypted data through encoding software to generate a new two-dimensional code graphic and display it on the display screen;
[0040] Step S104, after 30 seconds, repeat steps S102 to S103.
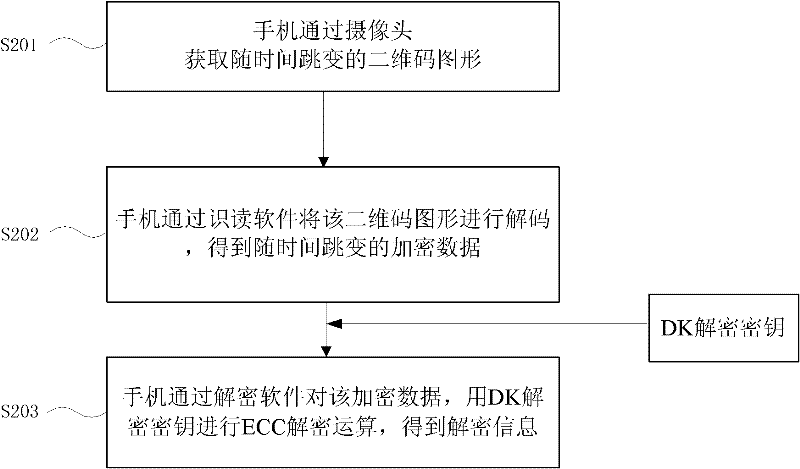
[0041] see figure 2 , figure 1 The decryption method corresponding to the two-dimensional code encryption method in Chinese, including:
[0042] Step S201, the mobile phone obtains the QR code graphics ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com