Key protection method in psam card
A key protection and key technology, which is applied in the field of key management, can solve the problems of CPU running away, not being able to know what instructions the CPU executes, PSAM card random rewriting, etc., and achieve the effect of preventing the key from being rewritten
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
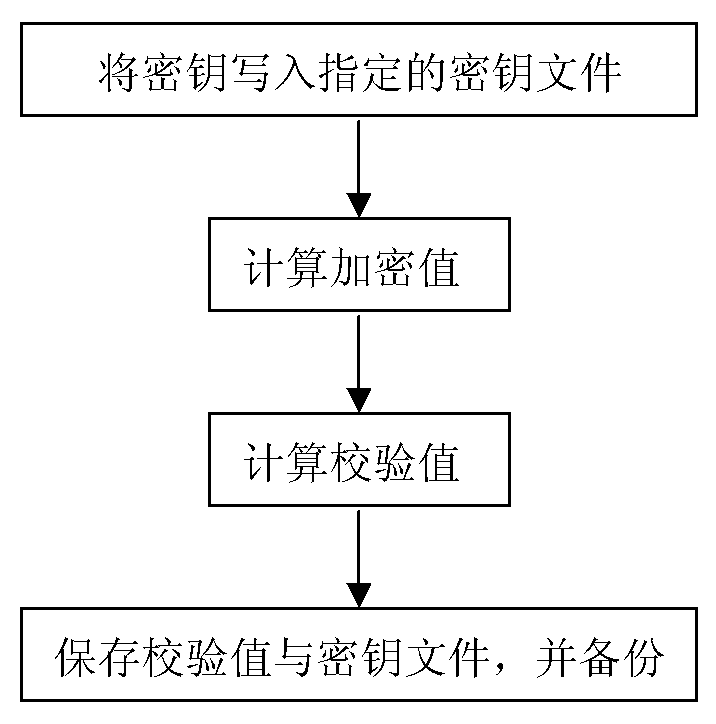
[0011] In order to prevent the key from being rewritten, and at the same time when rewriting occurs, the PSAM card can automatically recover the rewritten key file, and the invention adopts a backup mechanism. As shown in the figure, when issuing a PSAM card to load a key, first write the key into the specified key file, and at the same time use a specified algorithm (such as 3DES algorithm, or SM1 algorithm, etc.) The key value is the data of the specified encryption algorithm, and it is also used as the encryption key of the encryption algorithm to calculate the encryption value. The obtained encrypted value is grouped by 4 bytes, XORed with the packet data, and finally a 4-byte check value is obtained. This checksum is saved with the key file. When using the key, first check the key with the check value. While writing the key, back up the key and the verification value at the designated location of the PSAM card. The storage area of the backup key and the storage area ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com