A malicious information transmission defense method and system of a mobile intelligent terminal
A mobile intelligent terminal, malicious information technology, applied in wireless communication, electrical components, security devices, etc., can solve the problems of poor user interaction, incomplete security inspection of sent information, user economic losses, etc., to improve real-time and efficient The effect of preventing malicious information from being sent and solving the problem of malicious sending
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
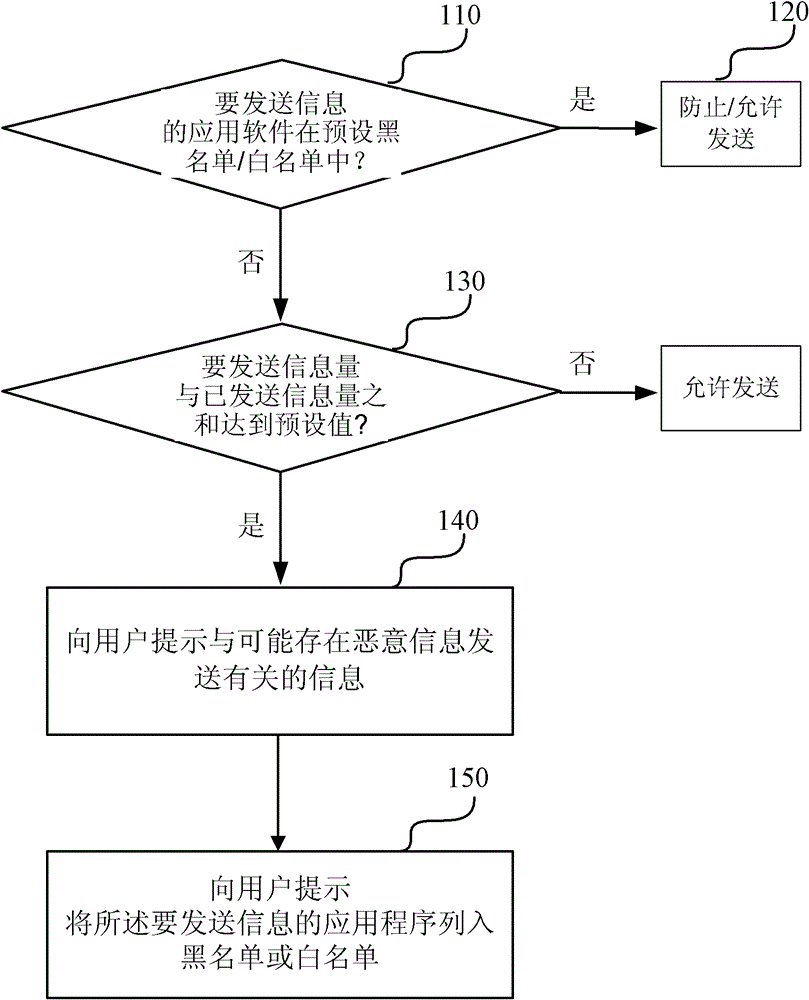
[0058] figure 1 A schematic flowchart of a method for defending malicious information transmission by a mobile smart terminal according to the first embodiment of the present invention is given. The steps of this embodiment will be described in detail below with reference to the accompanying drawings:
[0059] Judging step (110), when the application program of the mobile intelligent terminal is to send information, it is judged whether the sending object of the information is in the preset blacklist or whitelist;
[0060] In the processing step (120), if it is judged to be in the preset blacklist, then block the sending of the information; if it is judged to be in the preset whitelist, then allow the sending of the information.
[0061] Wherein, the blacklist is a list of application software not trusted by the smart mobile terminal; the white list is a list of application software trusted by the smart mobile terminal.
[0062] Each application program can be set in the trus...
no. 2 example
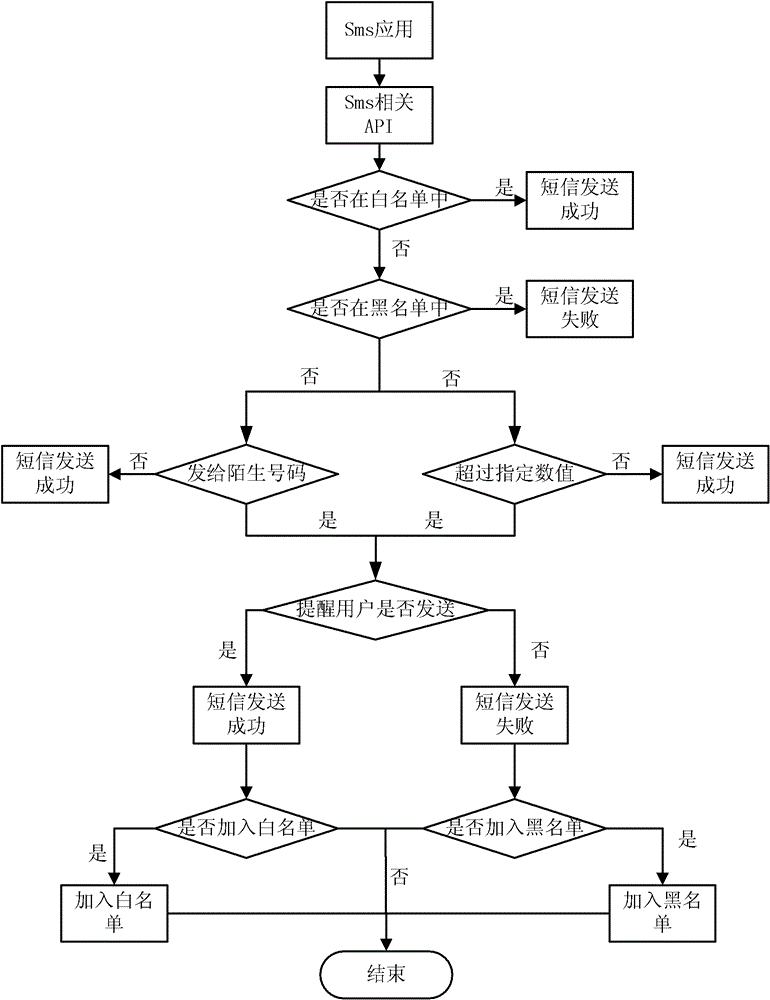
[0070] This embodiment describes in detail a method for defending against malicious information sent by an Android operating system terminal. figure 2 A flow example of a method for defending malicious information transmission by an Android operating system terminal according to this embodiment is given, and the steps of this embodiment will be described in detail below with reference to the accompanying drawings.
[0071] For ease of description, the same steps as those in the foregoing embodiments will not be described in detail, but only the differences from the foregoing embodiments will be highlighted. exist figure 1 and figure 2 In the same or similar steps as those in the foregoing embodiments, the same reference numerals are used.
[0072] In this example, refer to image 3 , by adding the checkWhiteList method and the CheckUnknownNumber method in the Android system, and modifying the method for sending the information in the framework layer of the Android system,...
no. 3 example
[0076] Figure 4 According to the third embodiment of the present invention, a schematic structural diagram of a malicious information transmission defense system of a mobile intelligent terminal, refer to the following Figure 4 To illustrate the composition of each part of this embodiment.
[0077] refer to Figure 4 , the module 41 , module 42 , module 43 , module 44 , and module 45 of this embodiment respectively execute the processing of step 110 , step 120 , step 130 , step 140 and step 150 of the first embodiment. It will not be expanded in detail here.
[0078] In addition, similar to the second embodiment, the malicious information transmission defense system of the third embodiment can also be a system using the Android operating system, and steps 110 and 120 are implemented by modifying the relevant methods of the Android operating system framework layer, and then by calling handleReachSentUnknown function to realize the function of prompting the user. It will n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com