Unified threat management system and data processing method thereof
A technology for managing systems and data, applied in the field of network security, can solve the problems of sensitive propagation of faults, affecting the function processing of predecessor modules, data privatization, etc., to achieve the effect of improving processing speed and strong dynamic scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
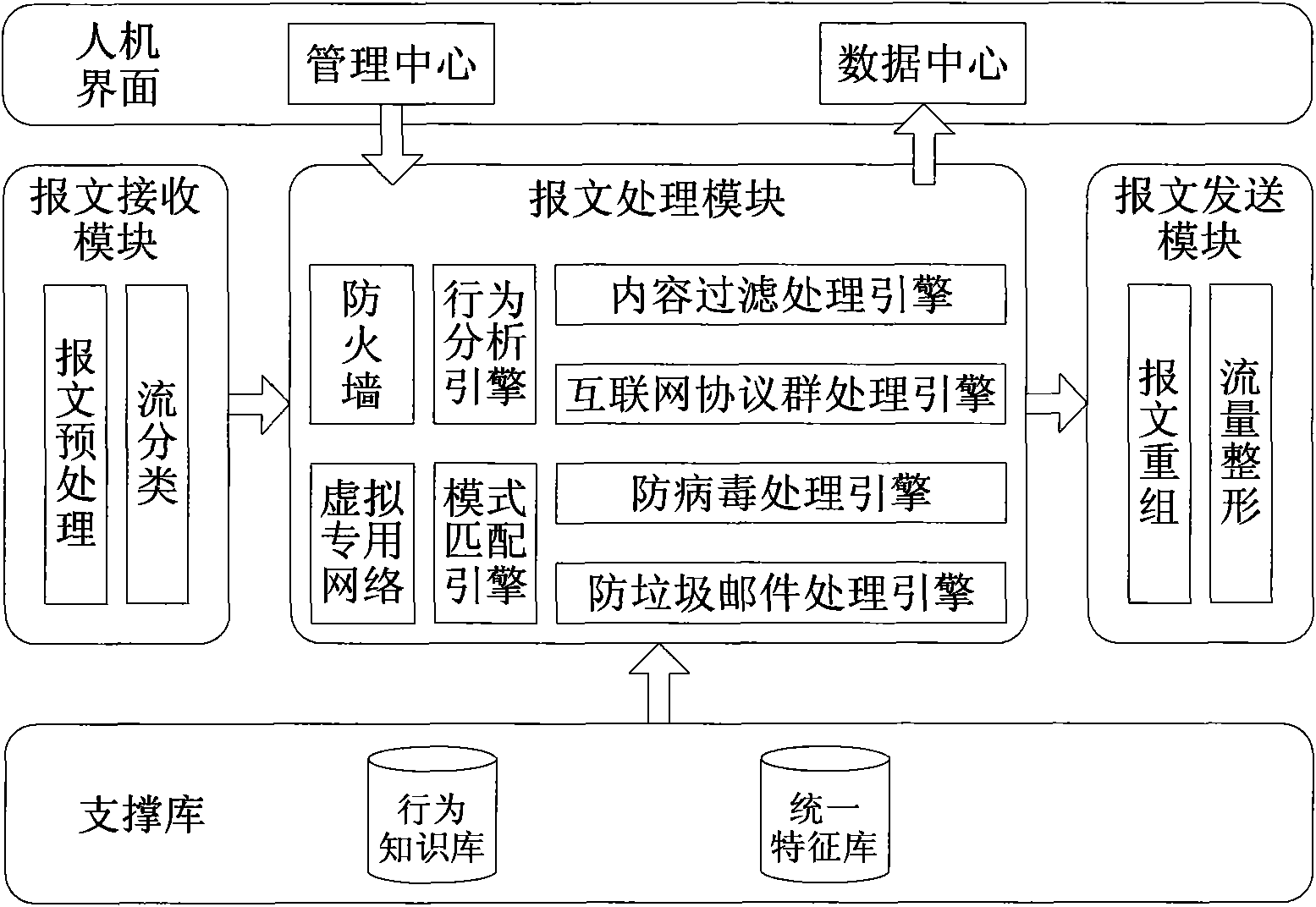
[0062] Embodiment 1, a unified threat management system, such as figure 2 shown, including:
[0063] The data storage module 102 includes a plurality of data pools, each data pool is used to store a type of data, and the types of data stored in each data pool are different from each other; The type is divided into different storage sub-modules, and each storage sub-module is called a data pool;
[0064] The service processing module 103 includes one or more computing pools, each computing pool is used to perform a processing operation to realize a service function, and read data from the data pool used to store the type of data required by the computing pool, Output the processed data to the data pool for storing this type of data; the service functions provided by each computing pool are different from each other; that is to say, the service processing module 103 is divided into different service sub-modules according to the different service functions provided, Each servi...
Embodiment 2
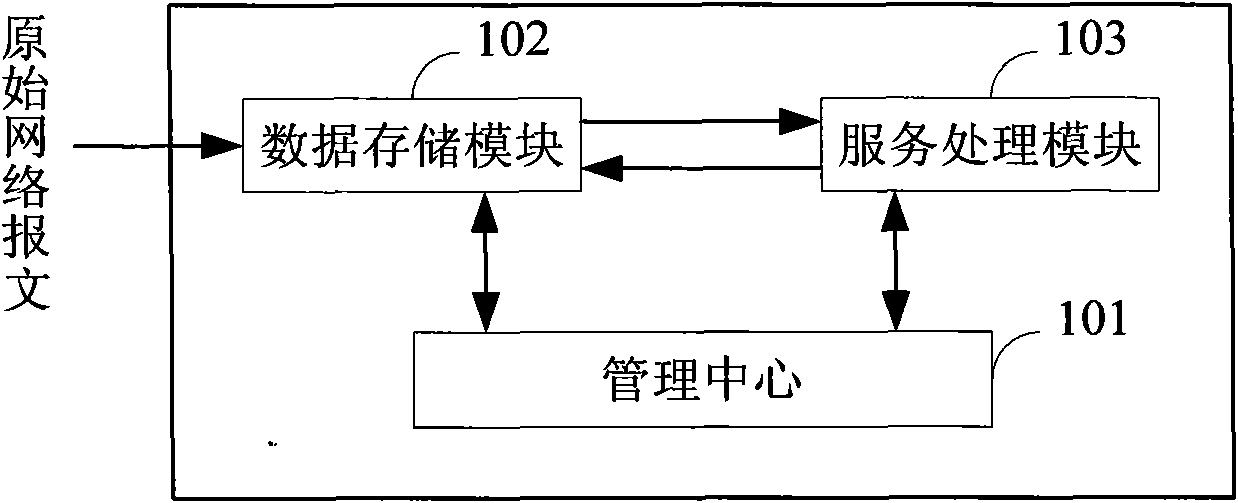
[0088] Embodiment 2, a unified threat management system includes the service processing module 103 , data storage module 102 and management center 101 in Embodiment 1.
[0089] In this embodiment, each data pool is as Figure 5 As shown, they can specifically include:
[0090] The memory is used to save the data of the type corresponding to the data pool, and to save the second identification of all the computing pools that need the data of this type;
[0091] The data monitor 1021 is configured to store and record the data in the memory when receiving data (which may be the original network packet data, or the data output by the computing pool in the service processing module 103) storage location; after each save, a data extraction notification is generated, sent to the computing pool corresponding to the second identifier saved in the memory, and the data storage location of this record is carried in the data extraction notification; and when a computing pool is received ...
Embodiment 3
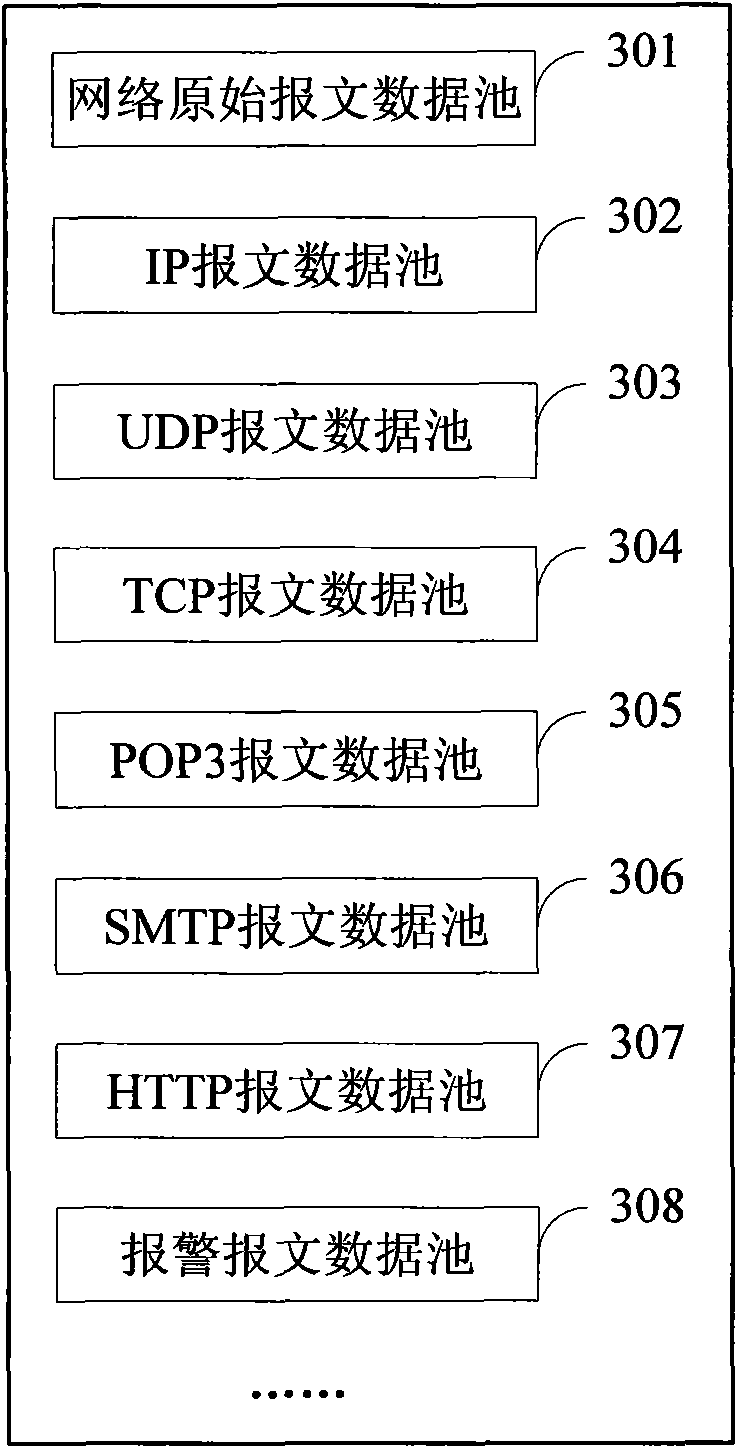
[0097] Embodiment 3, a unified threat management system includes the service processing module 103 , the data storage module 102 and the management center 101 in Embodiment 1 or 2.
[0098] In this embodiment, each computing pool is as Figure 6 As shown, they can specifically include:
[0099] The executor 1032 is used to execute one or more processing processes that implement the service functions corresponding to the computing pool; when there are multiple processing processes, these processing processes can be the same or different; each processing process processes the input data and then outputs ; Executor 1032 can be regarded as a set of processing processes;
[0100] The service manager 1031 is configured to, after receiving the data extraction notification from a data pool, return a data extraction message to the data pool when the data needs to be used, which carries the data storage location carried in the data extraction notification; from After the data is extra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com