A Method to Mitigate the Impact of Primary User Emulation Attacks
A technology for simulating attacks and main users, applied in electrical components, wireless communications, security devices, etc., can solve problems such as the inability to improve cooperative spectrum performance, and the energy detection method is not optimal, so as to reduce communication overhead, reduce impact, and reduce detection performance. the effect of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
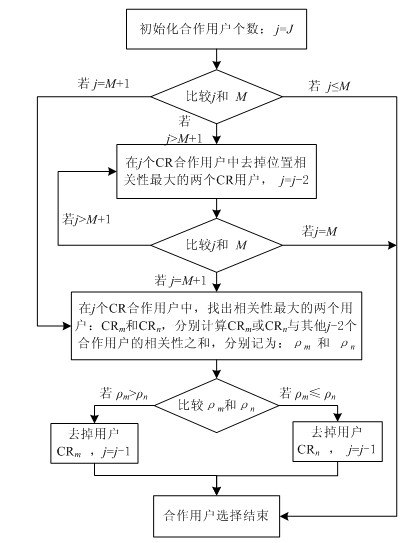
[0043] The specific implementation process of the method for mitigating the impact of the missed detection primary user simulation attack on the cooperative spectrum sensing performance of the present invention will be further described below in conjunction with the accompanying drawings.
[0044] Such as figure 1 , the cognitive radio network consists of a data fusion center, a master user simulated attacker and J cognitive radio users. The primary user transmitter transmits the relevant signal. In addition, due to occlusions such as the same obstacle, the signals received by cognitive radio users have location correlation. While the primary user emulation attack attacks as many cognitive radio users as possible with the smallest energy, so that the energy obtained by cognitive radio users from the primary user emulation attacker is equal to the energy obtained from the primary user. Master user impersonation attacks can also imitate other characteristics of the master us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com