A method and security agent device for preventing syn flood attack
A network security and legal technology, applied in the field of message attack prevention, can solve the problem of low implementation cost, and achieve the effect of low implementation cost, small changes and remarkable effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
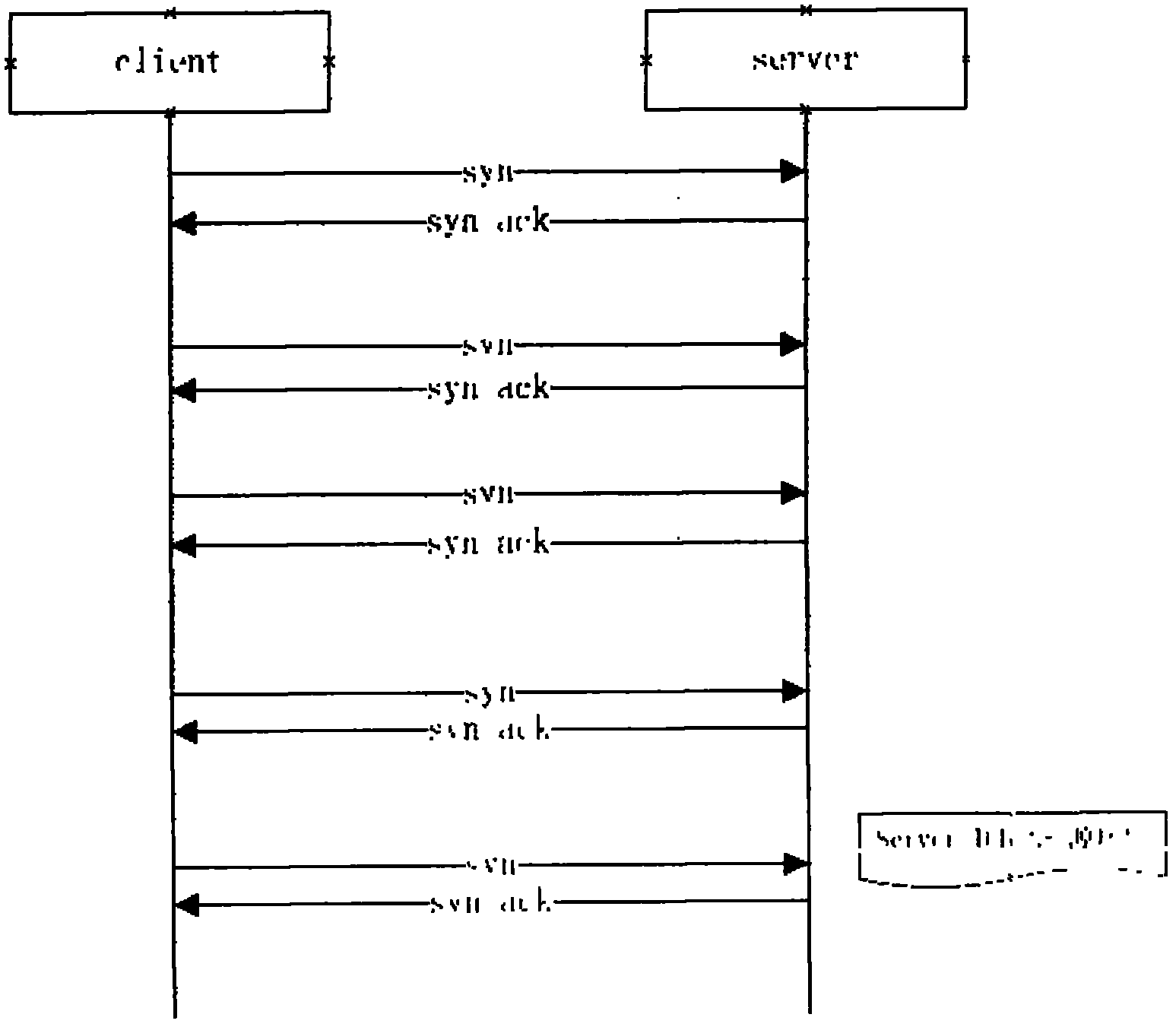
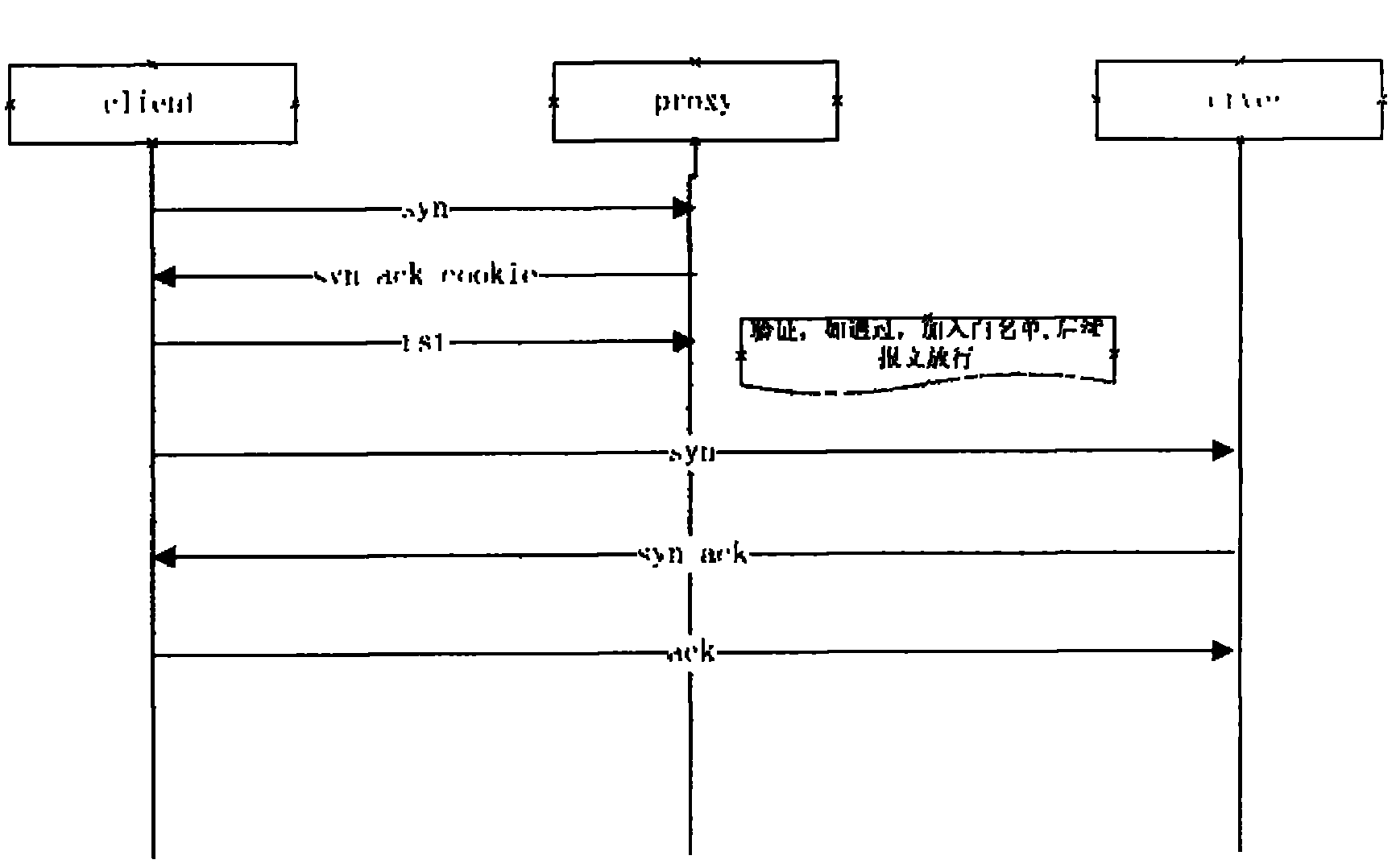
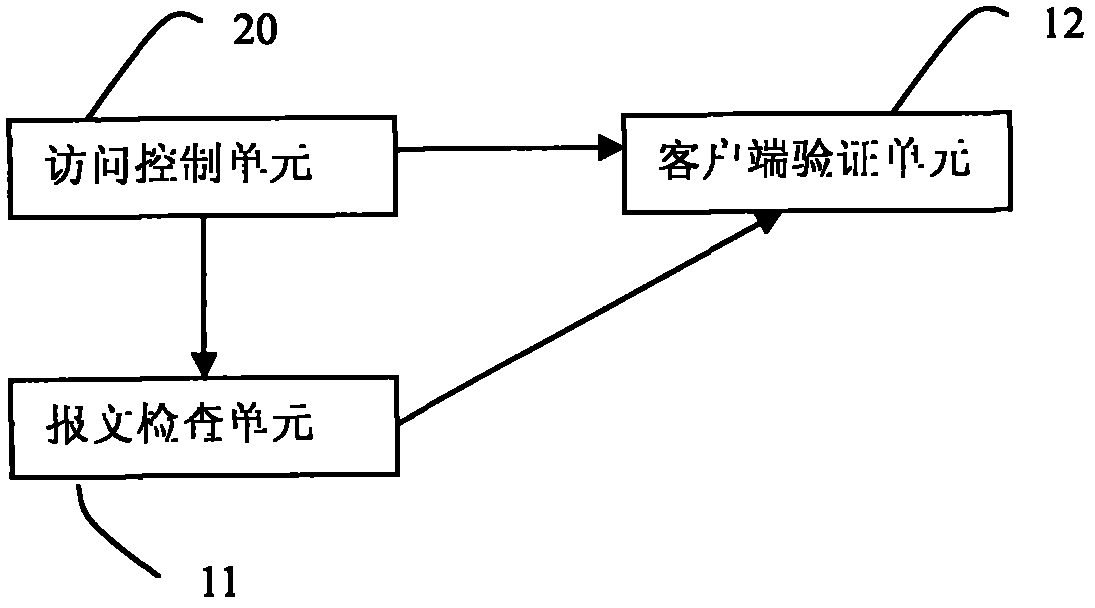
[0033] The invention utilizes a security proxy device located between a client (Client) and a server (Server) to prevent SYN Flood attacks based on the TCP protocol. The security agent device mentioned in the present invention is a logic device, which can be located on various physical network devices (such as routers, three-layer switches, firewalls and other network security devices) with security functions. The security agent device of the present invention mainly includes: a message checking unit 11 and a client verification unit 12 , wherein the network security device also includes an access control unit 20 . Each of the above units is a unit in a logical sense, and may be realized by software (that is, realized by running software codes in the memory by the CPU) or by hardware or firmware in terms of implementation. The following combination image 3 Take computer software as an example.
[0034] Step 101, screen out TCP SYN messages and verification response messages...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com