Method for combining identity-based cryptography and conventional public key cryptography
A public key cryptography system and identification cryptography technology, applied in the direction of public key of secure communication, user identity/authority verification, etc., which can solve the problems of public key cryptography system limitation, loss of user identification and private key, and information leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] Various details involved in the technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be pointed out that the described embodiments are only intended to facilitate the understanding of the present invention, rather than limiting it in any way.
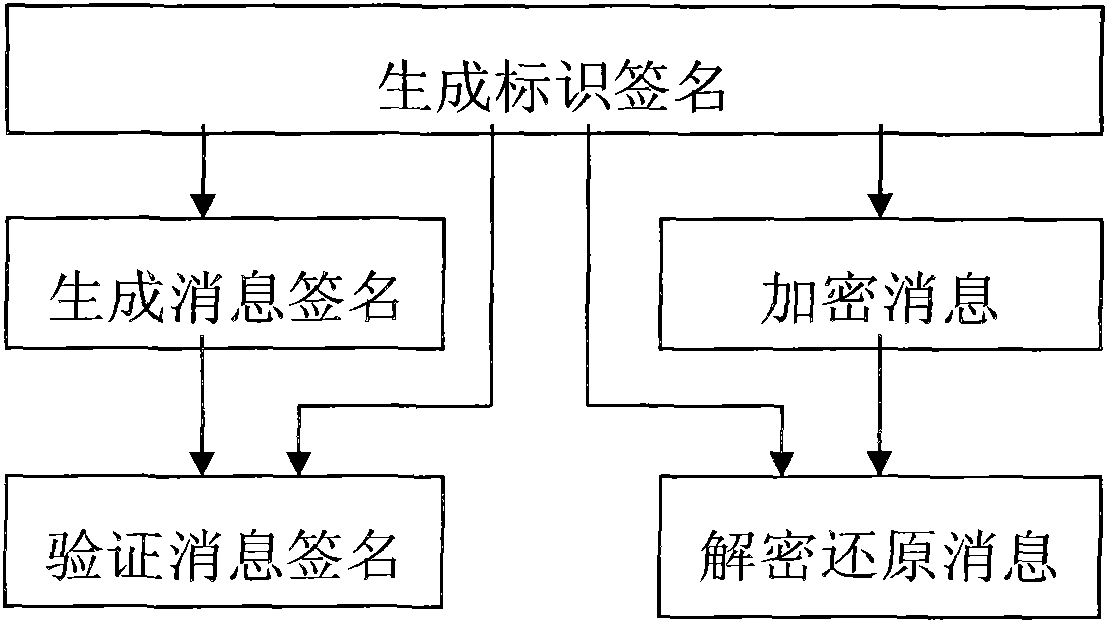
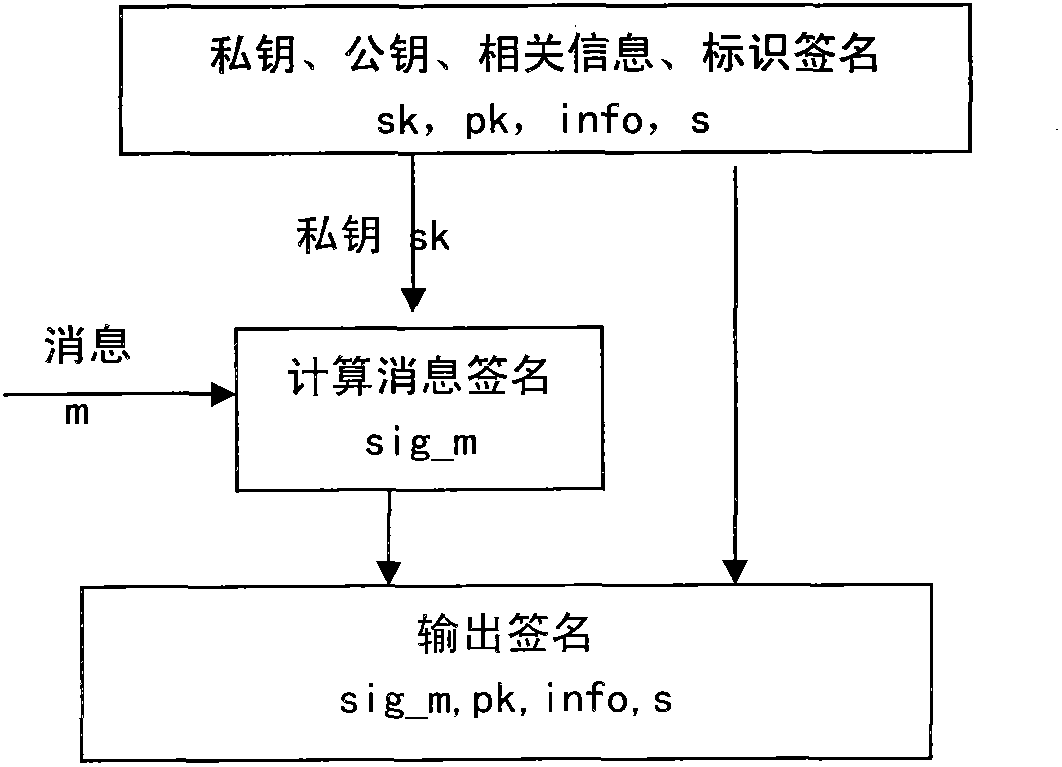
[0041] see figure 1 , a block diagram of the components of the present invention. Firstly, an identification signature is generated, and then based on the identification signature, operations such as message signature, verification of message signature, encryption of message, decryption and restoration of message can be performed.
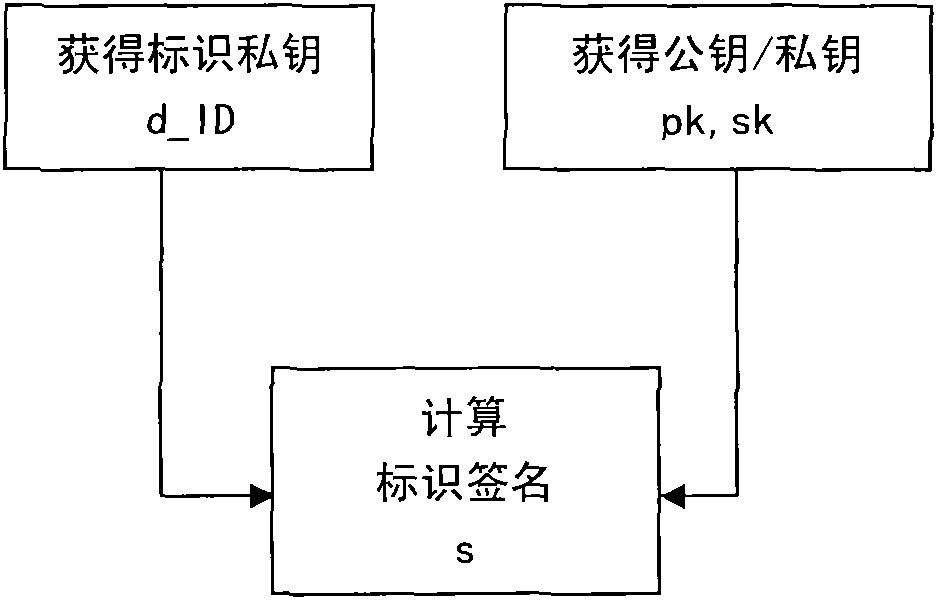
[0042] figure 1 Generating Identity Signatures section in , see figure 2 , the user first obtains the identification private key d_ID from the key center of the identification cryptosystem, such as BF-IBE, SK-IBE, etc., assuming that the signature and verification algorithms of the selected identification cryptosyste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com