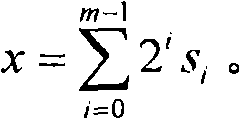Elliptic curve-based key exchange method
An elliptic curve and key exchange technology, which is applied in the field of key exchange based on elliptic curves, can solve problems such as insufficient security of calculation methods, inability to prevent small subgroup attacks, and failure to consider information such as the identities of both parties in communication, so as to improve security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
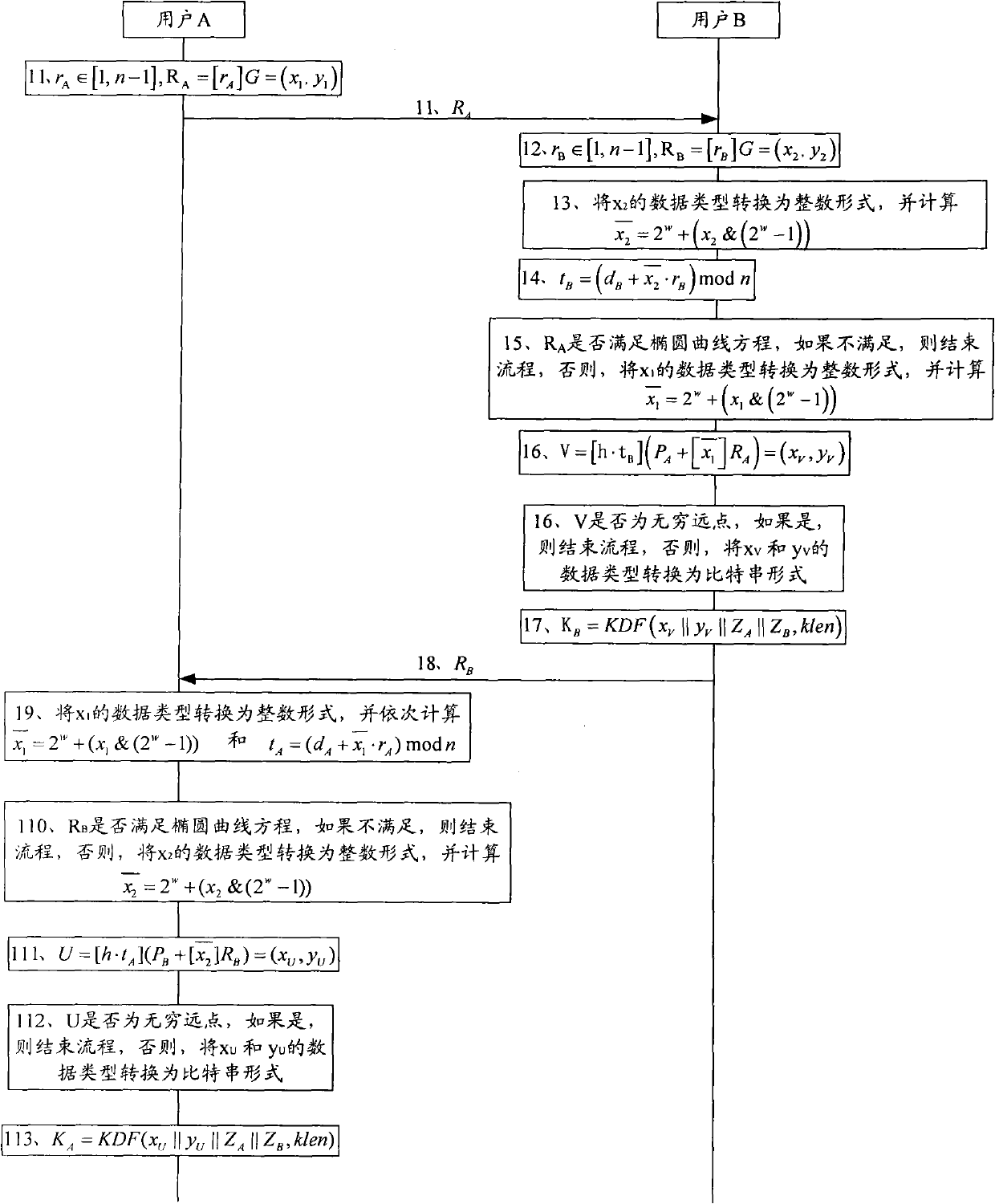
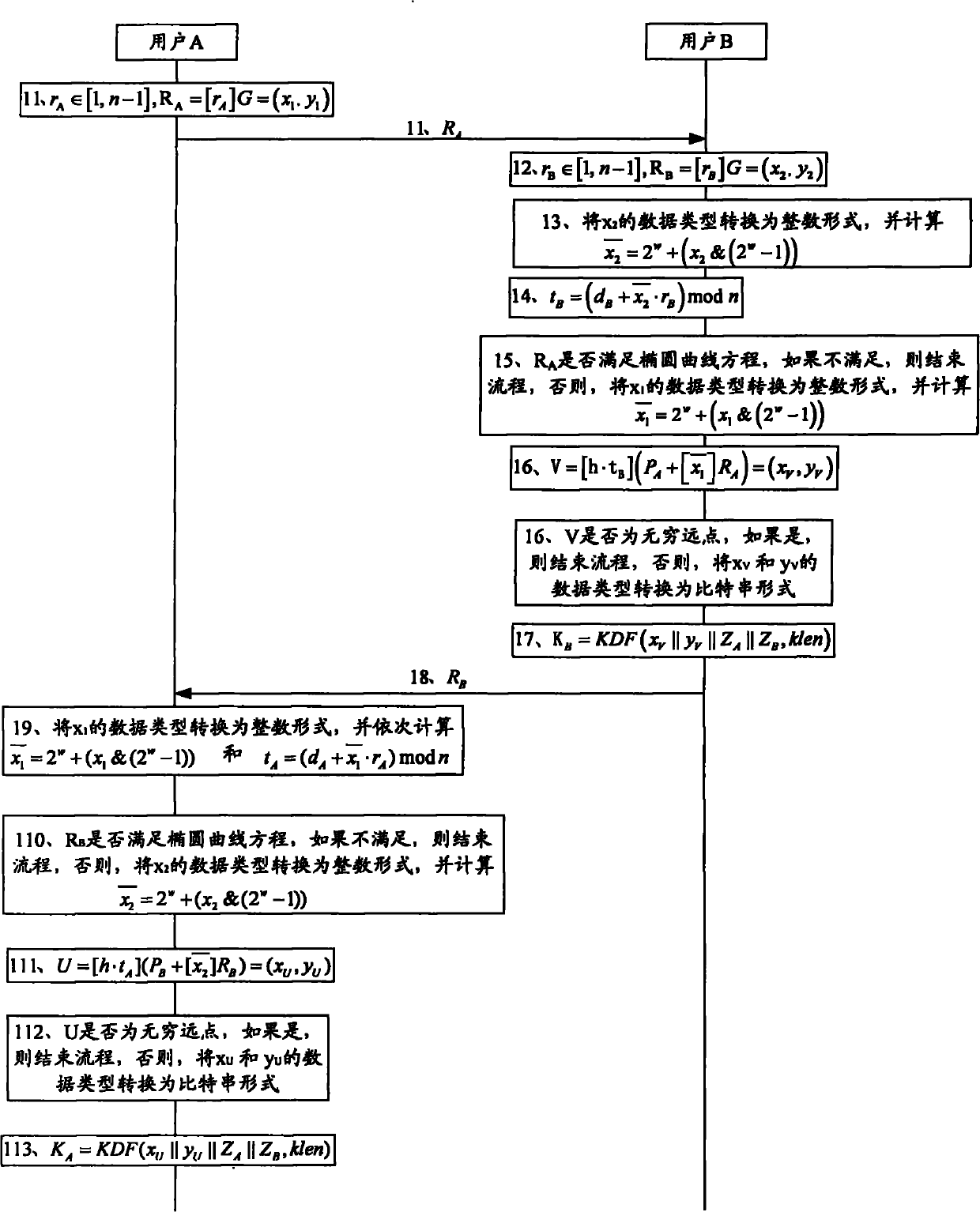
Image
Examples
example 1
[0089] Example 1: F q -192
[0090] Prime number q: BDB6F4FE 3E8B1D9E 0DA8C0D4 6F4C318C EFE4AFE3 B6B8551F
[0091] Coefficient a: BB8E5E8F BC115E13 9FE6A814 FE48AAA6 F0ADA1AA 5DF91985
[0092] Coefficient b: 1854BEBD C31B21B7 AEFC80AB 0ECD10D5 B1B3308E 6DBF11C1
[0093] Cofactor h: 1
[0094] Base point G=(x G ,y G ), whose order is denoted as n.
[0095] coordinate x G : 4AD5F704 8DE709AD 51236DE6 5E4D4B48 2C836DC6 E4106640
[0096] coordinate y G : 02BB3A02 D4AAADAC AE24817A 4CA3A1B0 14B5270432DB27D2
[0097] Order n: BDB6F4FE 3E8B1D9E 0DA8C0D4 0FC96219 5DFAE76F 56564677
[0098] User A's private key d A : 217B68E4 32A97CE6 A0C6E04E 0DF71CA4 9346980D75DBD585
[0099] User A's public key P A =(x A ,y A ):
[0100] coordinate x A : 365655CB 104D75C8 5250374B 27B86C7B 99100E85 05AD9A13
[0101] coordinate y A : 85D04BFE 5091FBE3 F0EFBB32 46C43631 3EFB918C 3935AB69
[0102] User B's private key d B : 02654286 C23E7C94 5E73A150 6C8E74D6 FE70EDC0D0E61BF0
[0...
example 2
[0187] Example 2: F q -256
[0188] Prime q: 8542D69E 4C044F18 E8B92435 BF6FF7DE 45728391 5C45517D722EDB8B 08F1DFC3
[0189] Coefficient a: 787968B4 FA32C3FD 2417842E 73BBFEFF 2F3C848B 6831D7E0EC65228B 3937E498
[0190] Coefficient b: 63E4C6D3 B23B0C84 9CF84241 484BFE48 F61D59A5 B16BA06E6E12D1DA 27C5249A
[0191] Cofactor h: 1
[0192] Base point G=(x G ,y G ), whose order is denoted as n.
[0193] coordinate x G : 421DEBD6 1B62EAB6 746434EB C3CC315E 32220B3BADD50BDC 4C4E6C14 7FEDD43D
[0194] coordinate y G : 0680512B CBB42C07 D47349D2 153B70C4 E5D7FDFC BFA36EA1A85841B9 E46E09A2
[0195] Order n: 8542D69E 4C044F18 E8B92435 BF6FF7DD 29772063 0485628D5AE74EE7 C32E79B7
[0196] User A's private key d A : 6FCBA2EF 9AE0AB90 2BC3BDE3 FF915D44 BA4CC78F88E2F8E7 F8996D3B 8CCEEDEE
[0197] User A's public key P A =(x A ,y A ):
[0198] coordinate x A : 3099093B F3C137D8 FCBBCDF4 A2AE50F3 B0F216C3 122D79425FE03A45 DBFE1655
[0199] coordinate y A : 3DF79E8D AC1CF0EC B...
example 3
[0289] Example 3: F 2 m-193
[0290] base field generator polynomial: x 193 +x 15 +1
[0291] Coefficient a: 0
[0292] Coefficient b: 00 2FE22037 B624DBEB C4C618E1 3FD998B1 A18E1EE0D05C46FB
[0293] Cofactor h: 4
[0294] Base point G=(x G ,y G ), whose order is denoted as n.
[0295] coordinate x G : 00 D78D47E8 5C936440 71BC1C21 2CF994E4 D21293AAD8060A84
[0296] coordinate y G : 00 615B9E98 A31B7B2F DDEEECB7 6B5D8755 86293725F9D2FC0C
[0297] Order n: 80000000 00000000 00000000 43E9885C 46BF45D8 C5EBF3A1
[0298] User A's private key d A : 5E39F93D AD7F334A 7D57E0CD 0F5C5556 128DABC4F5D21844
[0299] User A's public key P A =(x A ,y A ):
[0300] coordinate x A : 00 2A3B6E0C B88265C4 FB1DC1EB 9208DDFB AED784E5E8837972
[0301] coordinate y A : 00 635BF2ED BD18BAD5 4AE54A11 9EEED807 D8007A23909F4BCC
[0302] User B's private key d B : 0F479000 13BDBEB9 D37426A3 D5DCA50B 51D7E68AE85522ED
[0303] User B's public key P B =(x B ,y B ):
[0304] coordi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com