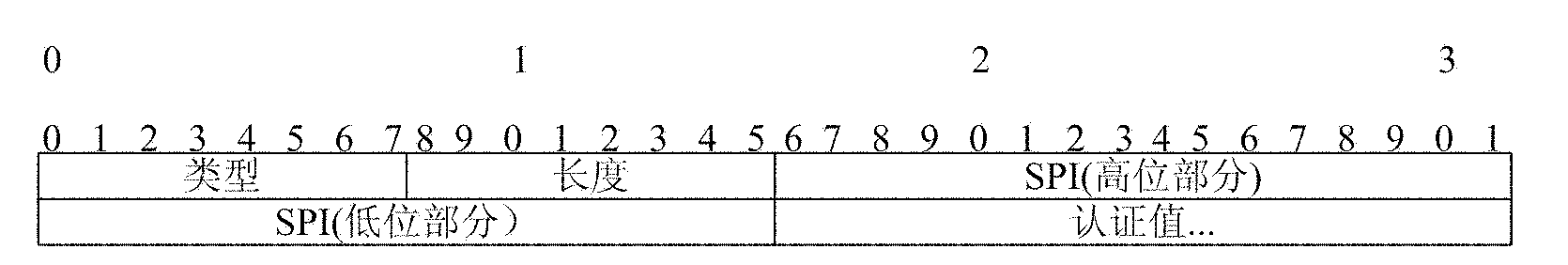Method for realizing mobile node identity anonymity during mobile internet protocol (IP) registration
A mobile node, anonymity technology, applied in the field of mobile IP network, can solve the problems of leakage, infeasibility, irrelevance, etc., to achieve the effect of protecting user privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
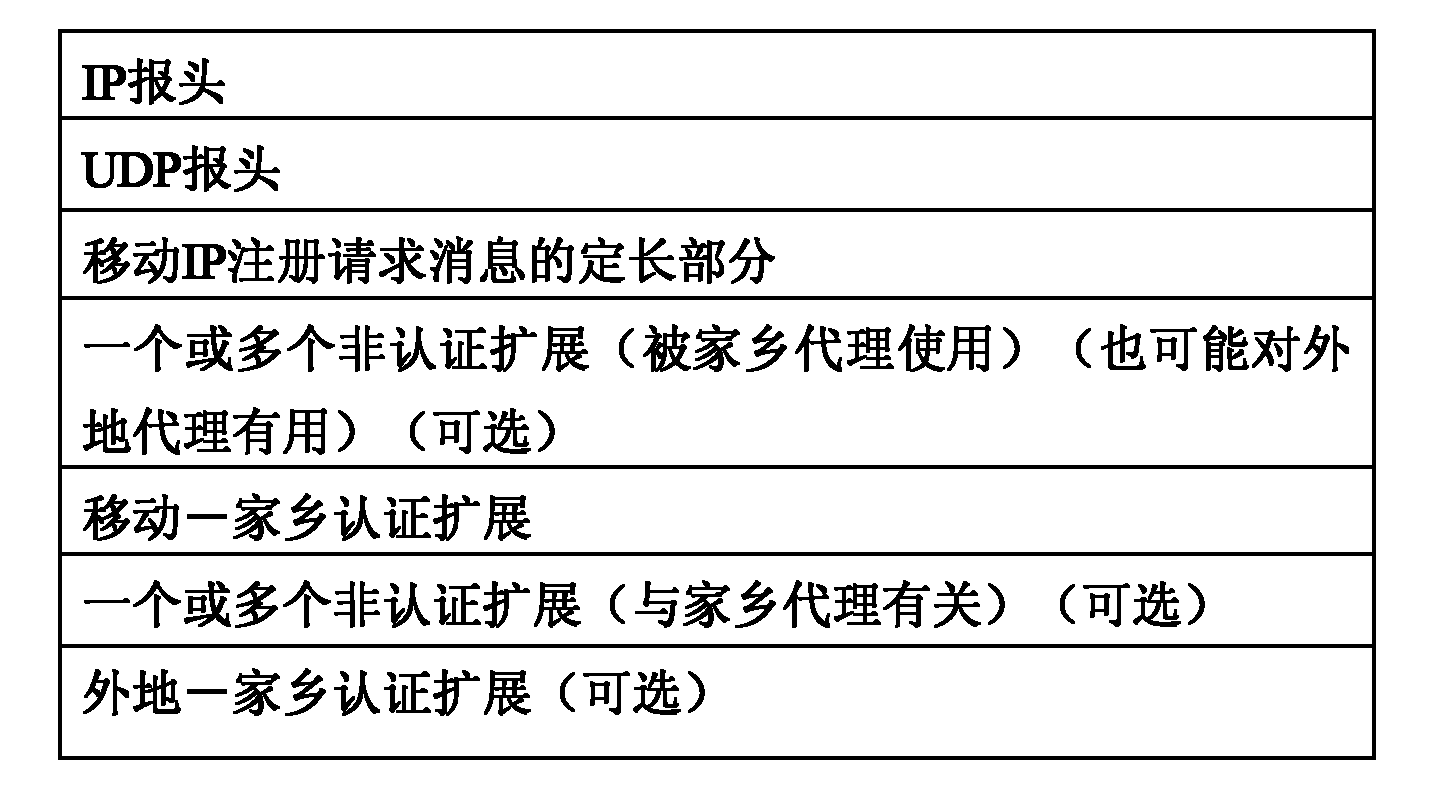
[0050] The core idea of the present invention is that in the mobile IP network, the mobile node utilizes the Hash function to carry out hash operation to construct the constantly changing temporary identity identifier of the mobile node, i.e. H(ID MN ||N HA ), then carry the temporary identity identifier information of the mobile node in the mobile IP registration request message sent, and set the home address field and IP source address field of the registration request message to 0, so that the home agent can register according to the received Request the mobile node temporary identity information in the message to authenticate the mobile node; the home agent randomly generates a new random number N' HA , placed in the high 32b of the identification field of the fixed-length part in the registration response message, and then return the registration response message to the mobile node, so that the mobile node can HA Calculate the temporary identity identifier information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com