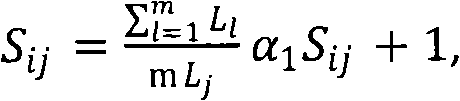Wormhole attack defense method based on multipath routing and trust mechanism in Ad hoc network
A wormhole and routing technology, applied in the field of information security, can solve the problem of packet loss of special guard nodes and attack nodes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
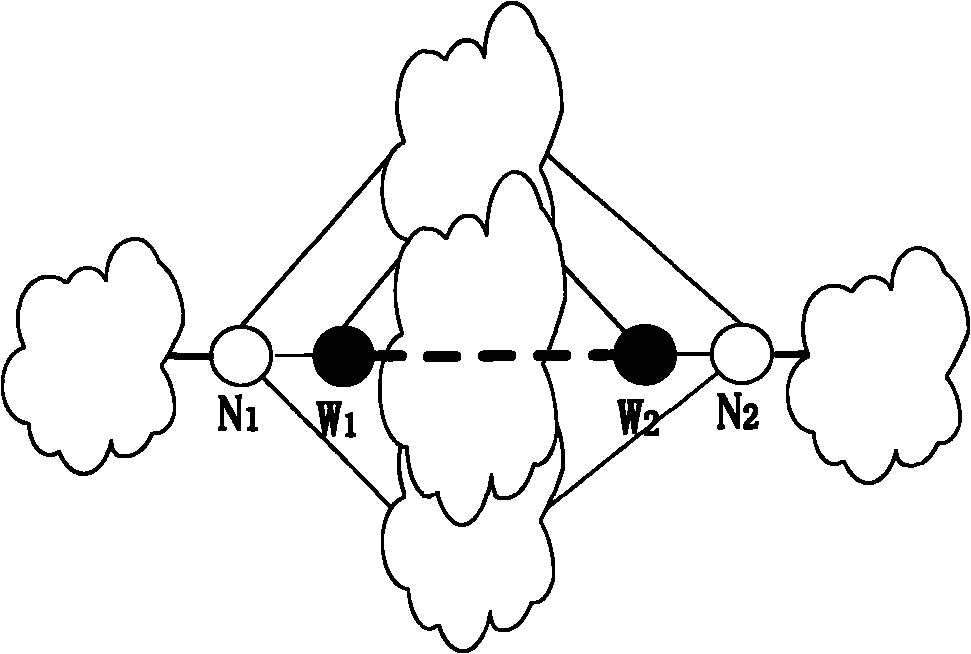
[0050] See figure 1, It is a schematic diagram of the Ad hoc network wormhole attack topology of the present invention;
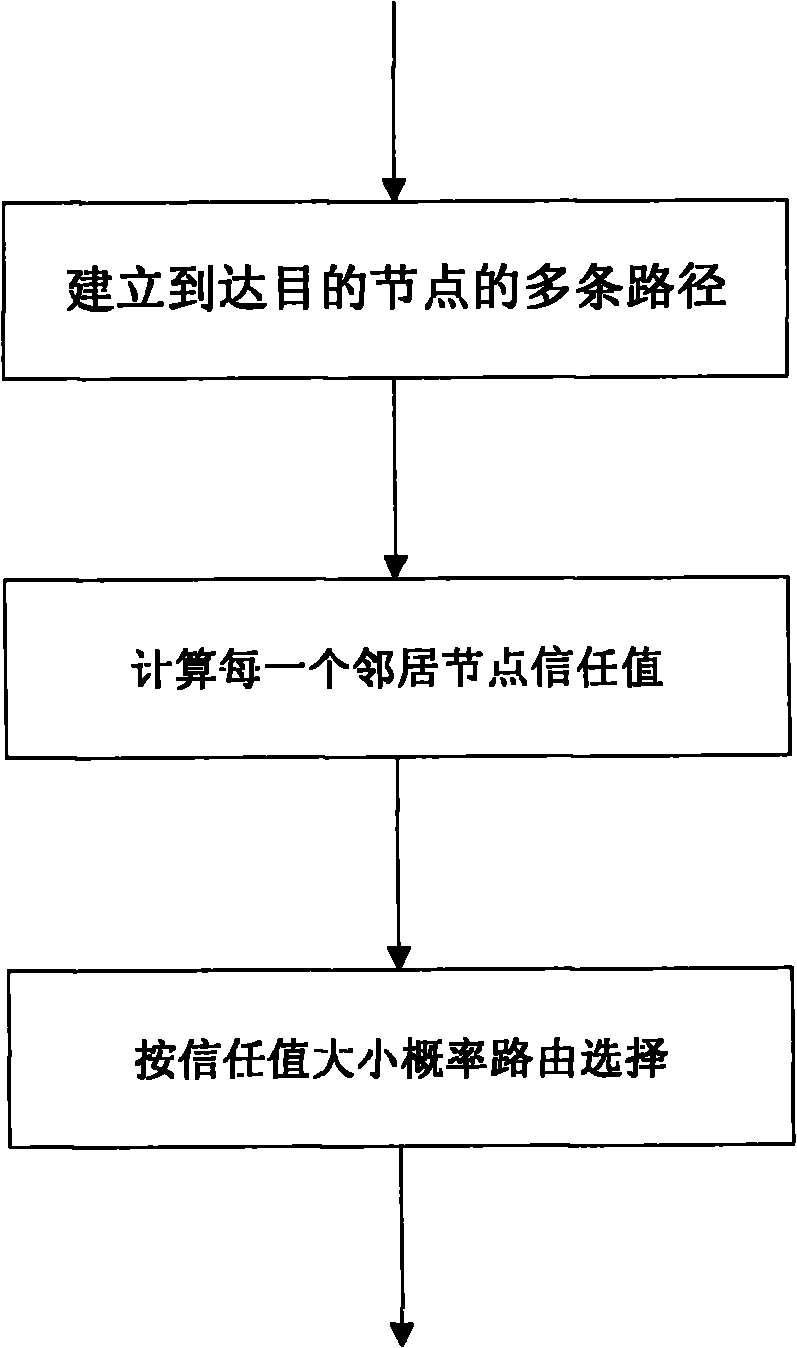
[0051] See figure 2, It is the overall schematic flow chart of the present invention
[0052] The wormhole attack defense method based on multi-path routing and trust mechanism in the Ad hoc network of the present invention, the specific steps of the method are as follows:
[0053] Step 1: The node establishes multiple paths to the destination node.
[0054]First of all, it is pointed out that for a node N, multipath means that different paths pass through different next-hop neighbor nodes. If a neighbor node has multiple paths to reach the destination node, the node N calculates these paths into one
[0055] If a node reaches the destination node, the number of different paths of the next hop is less than the threshold value. Then send a routing request message, and save all paths with different next hops in the routing table.
[0056] Step 2: The n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com